KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Some of the laptops distributed by the UK Department for Education (DfE) to vulnerable students have been found to be infected with malware as reported by the BBC.
The devices are given out for free by the government to support disadvantaged students unable to access remote education during the COVID-19 pandemic, including children and young people who have no digital devices, have only a smartphone, or share a single device with other family members.
DfE also partnered with the mobile network providers to give the students access to free data to be able to attend remote school while they learn from home.
However, as revealed by Bradford Schools teachers, some of the files found on the government-provided Windows laptops were infected with malware as discovered while preparing the devices for delivery to students.
“Upon unboxing and preparing them, it was discovered that a number of the laptops were infected with a self-propagating network worm,” according to one of the teachers.
DfE has already delivered more than 800,000 laptops and tablets until January 2021 to schools, academy trusts (trusts), and local authorities (LAs) around the UK.
“We are aware of an issue with a small number of devices,” a DfE official told the BBC. “And we are investigating as an urgent priority to resolve the matter as soon as possible.”
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
“DfE IT teams are in touch with those who have reported this issue. We believe this is not widespread.”
The malware found on the infected laptops is Gamarue (aka Andromeda), a modular malware strain known to be commonly used by Russian and Eastern European cybercriminals.
Gamarue is sold on underground cybercrime markets and it is capable of allowing attackers to take control of compromised devices using a Teamviewer plugin.
It also has support for keylogger, rootkit, Socks4/5 proxy server, and formgrabber plugins which allows it to look keystrokes, gain persistence, reroute malicious traffic, and steal web browser input data, respectively.
It’s also capable of modifying the computer’s settings, stealing user information and documents. PCs commonly get infected with Gamarue via previous infections, through exploit kits while browsing compromised websites, and via malicious email attachments.
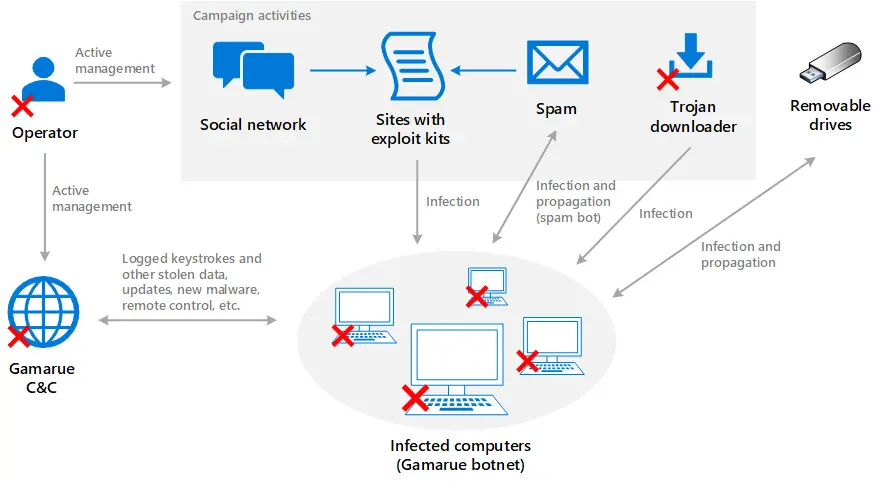
Some Gamarue variants have worm capabilities that enable the malware to spread to other devices via infected removable devices such as portable hard disks and USB flash drives.
However, since 2011 when the first samples were spotted in the wild, Gamarue has mainly been used to deliver a huge list of other malware payloads including but not limited to the Petya, Troldesh, and Cerber ransomware, the Kasidet malware (also known as Neutrino bot) used for DDoS attacks, the Lethic spam bot, as well as Ursnif, Carberp, and Fareit info-stealing malware.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
While Microsoft disrupted the Andromeda botnet by taking down its servers in a coordinated global operation with law enforcement and other partners in 2017, the malware still infects devices on a daily basis to this day using the removable drive spreader module.