KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A vulnerability in GNOME Display Manager (gdm) could allow a standard user to create accounts with increased privileges, giving a local attacker a path to run code with administrator permissions (root).
Although certain conditions are necessary, the bug is easy to exploit. The process involves running a few simple commands in the terminal and modifying general system settings that do not require increased rights.
Exploiting the bug in gdm3 takes advantage of crashing the AccountsService component, which keeps track of the users available on the system.
Besides handling the graphical display managers, gdm3 is also responsible for showing the user login interface on Unix-like operating systems.
GitHub’s security researcher Kevin Backhouse discovered a simple way to trick an already set up Ubuntu system into running the account configuration routine for a new system. This scenario requires an administrator account to set up the machine and install applications.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
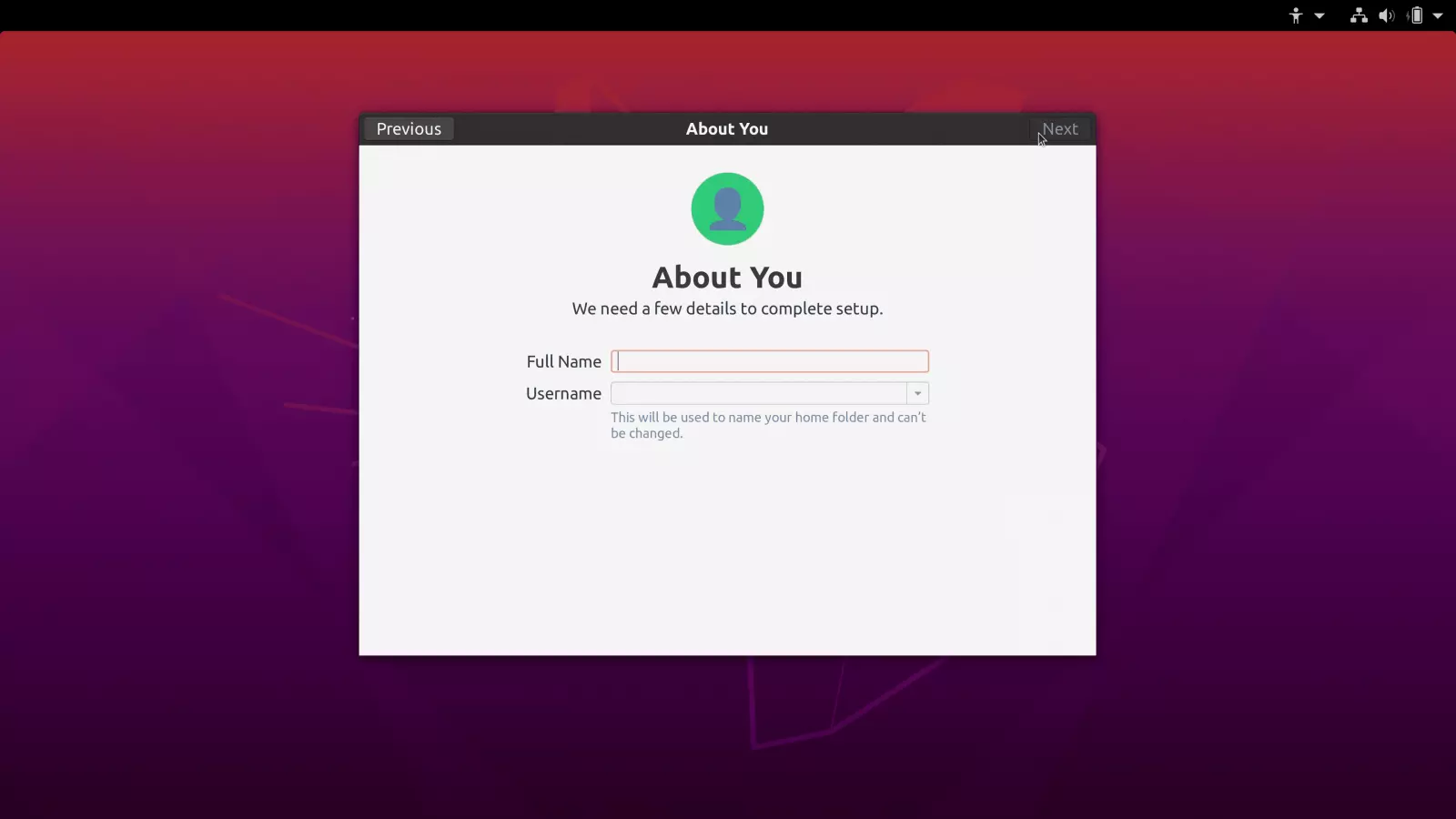
The researcher found that ‘gdm3’ triggered this sequence when the ‘accounts-daemon’ of the AccountsService component was not running. A standard user should not be able to stop it.
However, Backhouse discovered two vulnerabilities in AccountsService that caused the component to hang (CVE-2020-16127) and drop user account privileges (CVE-2020-16126), allowing a standard user to crash the daemon by sending it a delayed segmentation fault signal (kill -SIGSEGV).
The delay is necessary to give time to log out of the current session or the user is locked out.
These two vulnerabilities affect Ubuntu 20.10, Ubuntu 20.04, Ubuntu 18.04, and Ubuntu 16.04.
For CVE-2020-16127, the researcher explains in a blog post today that it was caused by code added to Ubuntu’s version of AccountService that does not exist in the upstream version maintained by freedesktop:
“Ubuntu’s patch adds a function named is_in_pam_environment, which looks for a file named .pam_environment in the user’s home directory and reads it. The denial of service vulnerability works by making .pam_environment a symlink to /dev/zero. /dev/zero is a special file that doesn’t actually exist on disk. It is provided by the operating system and behaves like an infinitely long file in which every byte is zero. When is_in_pam_environment tries to read .pam_environment, it gets redirected to /dev/zero by the symlink, and then gets stuck in an infinite loop because /dev/zero is infinitely long”
– Kevin Backhouse, GitHub Security Lab
Triggering it was possible by making a modification in the system Settings that did not require elevated privileges. Backhouse went with changing the language.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
Without the AccountsService running, gdm3 has no clue about the accounts present on the machine and provides the option to create a new one with root privileges, as in the case of a first-time setup.
This bug is now tracked as CVE-2020-16125 and rated with a high severity score of 7.2 out of 10. It affects Ubuntu 20.10, Ubuntu 20.04, and Ubuntu 18.04.
Backhouse created a video showing how easy it was for him to exploit the gdm3 vulnerability on Ubuntu 20.04:
Backhouse published on Monday separate reports for these three vulnerabilities [1, 2] offering technical details. He reported them to Ubuntu and GNOME maintainers on October 17, and fixes are available in the latest code.