KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Online surveys and form building software as a service Typeform has patched an information hijacking vulnerability.
The flaw which existed in Typeform’s Zendesk Sell app integration could let attackers quietly redirect form submissions with potentially sensitive data to themselves.
Online survey and form creation tool Typeform lets users create webpages for easy data collection from users.
Every such form created on the platform has a unique “form ID,” such as hHXhmf, which in the case of publicly accessible surveys may be indexed by search engines, as observed by BleepingComputer.
Behind the scenes, Typeform’s systems use this form ID throughout workflows to keep track of form submissions and transmit collected data between different parts of the application.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
Under normal circumstances, knowledge of this form ID would merely let any user access and fill the corresponding survey.
However, a severe vulnerability in Typeform meant, attackers could covertly gather responses submitted by respondents for virtually any form, should they have knowledge of this ID.
Without explicitly naming Typeform, bug bounty hunter Ronak Patel recently provided details on an Insecure Direct Object Reference (IDOR) bug that impacted “an app [used] to generate forms for surveys, quiz and more.”
On further investigation, BleepingComputer identified the flaw had existed in Typeform.
IDOR vulnerabilities occur when a system object which has a reference can be accessed in an unauthorized manner directly by users.
In this case, the object refers to a Typeform form/survey and the reference is the “form_id” that can let attackers tap into the data submitted for a form.
Typeform allows integration of apps and web services like Google Analytics and Zendesk Sell to help enhance the processing of form submissions.
For example, survey creators can use the Zendesk Sell app and map the survey response fields to the Zendesk Sell fields in their account for data analysis.
Zendesk Sell is a sales CRM and leads conversion software which explains why Typeform survey creators from certain business areas may find it helpful.
Patel created a test Zendesk Sell account and integrated it with his Typeform account.
He observed the network requests, including the GET and POST fields, being exchanged between Typeform and Zendesk Sell throughout the integration workflow.
The “form_id” field, shown below, caught his attention.
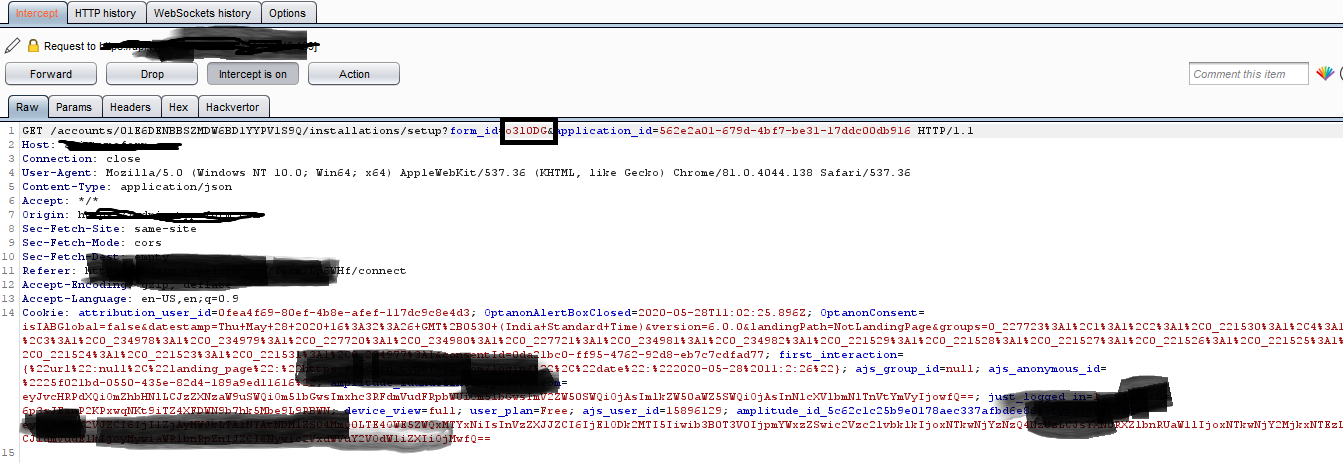
The researcher additionally created an “attacker’s” Zendesk Sell account for testing and noticed it was possible to tamper with the “form_id” field being transmitted in the integration request to an arbitrary value, such as the form_ID of a Typeform survey belonging to the victim.
This means threat actors could casually keep looking up Typeform form IDs being indexed by search engines from time to time.
But now. by exploiting this app integration flaw, the actors could harvest the collected survey responses within their Zendesk Sell accounts, with the survey creator having no knowledge of the illicit activity taking place.
“Summing up, using IDOR in this integration process, attacker could integrate his Zendesk sell account with any form without any kind of user interaction and could fetch all sensitive data received as a form response,” said Patel.
Patel states the vulnerability was discovered by him about six months ago and patched two months ago by the platform.
Also Read: How To Secure Your WiFi Camera: 4 Points To Consider
BleepingComputer reached out to Typeform who ran an investigation and confirmed that they had patched the flaw earlier in a statement:
“We can confirm that all data submitted through typeforms [sic] is encrypted in transit and at rest. The fix to the vulnerability in this integration was implemented in July 2020,” a Typeform spokesperson told BleepingComputer.
The researcher’s detailed findings on the integration vulnerability can be found in his blog post.