KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Tyler Technologies has paid a ransom for a decryption key to recover files encrypted in a recent ransomware attack.
Tyler Technologies states that they are the largest software company in North America devoted to the public sector, with over $1.2 billion in revenue for 2020 and 5,500 employees.
On September 23rd, Tyler Technologies suffered a cyberattack by the RansomExx ransomware operators, who were also behind recent attacks on Konica Minolta and IPG Photonics.
In response to the attack, Tyler Technologies immediately disconnected portions of their network to contain the ransomware’s spread and limit their clients’ exposure.
Also Read: MAS Technology Risk Management Guidelines
“Early this morning, we became aware that an unauthorized intruder had disrupted access to some of our internal systems. Upon discovery and out of an abundance of caution, we shut down points of access to external systems and immediately began investigating and remediating the problem,” Tyler Technologies CIO Matt Bieri emailed clients.
The attack caused significant disruption to Tyler Technologies operations, it was contained locally and did not spread to their clients.
Sources in the public sector have told BleepingComputer that the ransomware attack severely impacted Tyler Technologies and that the company expected it would take thirty days to recover operations fully.
A source told BleepingComputer that Tyler Technologies paid the RansomExx ransom demand to recover encrypted data.
It is not unknown, though, how much was paid to receive a decryption key.
When the ransomware encrypted Tyler Technologies’ files, they appended an extension similar to ‘.tylertech911-f1e1a2ac.’
To prove that the decryptor was valid, BleepingComputer was able to decrypt encrypted files [1, 2] uploaded to VirusTotal at the time of the ransomware attack.
Also Read: How Does Do Not Call (DNC Registry) Affect Marketing 2020
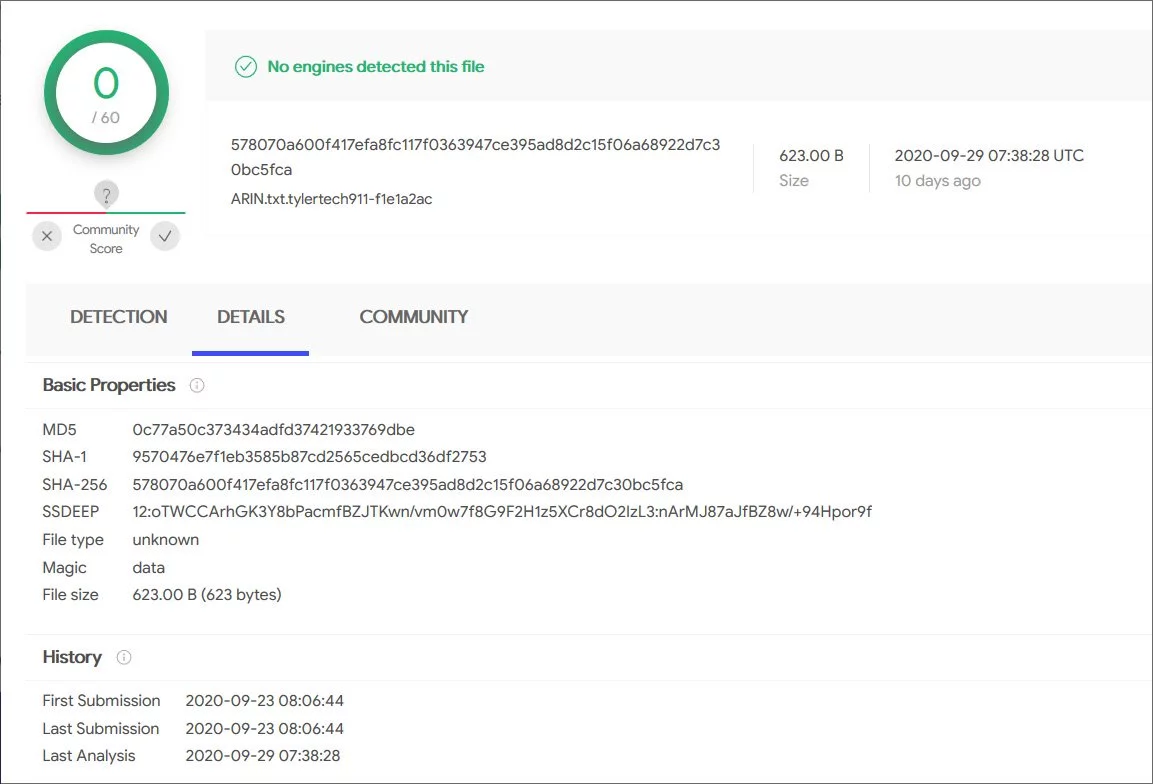
When decrypted, the Arin.txt file contained a list of IP ranges used by the company.
RansomExx is also known to steal data before encrypting devices on a network. The ransomware operators then threaten to release this stolen data unless a victim paid the ransom.
As many school districts, court systems, and local and statement governments in the United States are Tyler Technologies customers, the risks of the public leaking of sensitive information and source code is concerning.
This concern may have been a driving factor in the decision to pay the ransom.
When asked about the decryptor, Tyler Technologies did not dispute the ransom payment, but told BleepingComputer that they could not disclose any further information at this time.
“Given the sensitivities around the incident and our investigation of it, and our active cooperation with law enforcement, we are not at liberty to disclose additional details at this time.”

Established in 2018, Privacy Ninja is a Singapore-based IT security company specialising in data protection and cybersecurity solutions for businesses. We offer services like vulnerability assessments, penetration testing, and outsourced Data Protection Officer support, helping organisations comply with regulations and safeguard their data.
Singapore
7 Temasek Boulevard,
#12-07, Suntec Tower One,
Singapore 038987
Latest resources sent to your inbox weekly
© 2025 Privacy Ninja. All rights reserved
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!

Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!
