KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Trust Wallet and MetaMask wallet users are being targeted in ongoing and aggressive Twitter phishing attacks to steal cryptocurrency funds.
MetaMask and Trust Wallet are mobile apps that let you create wallets to store, buy, send, and receive cryptocurrency and NFTs.
When users launch MetaMask or Trust Wallet apps for the first time, the app prompts them to create a new wallet. As part of this process, the app will show a recovery phrase consisting of 12 words and prompts users to save them somewhere safe.
The apps use this recovery phrase to create the private keys necessary to access your wallet. Anyone who has this recovery phrase can import your wallet and use the cryptocurrency funds stored in it.
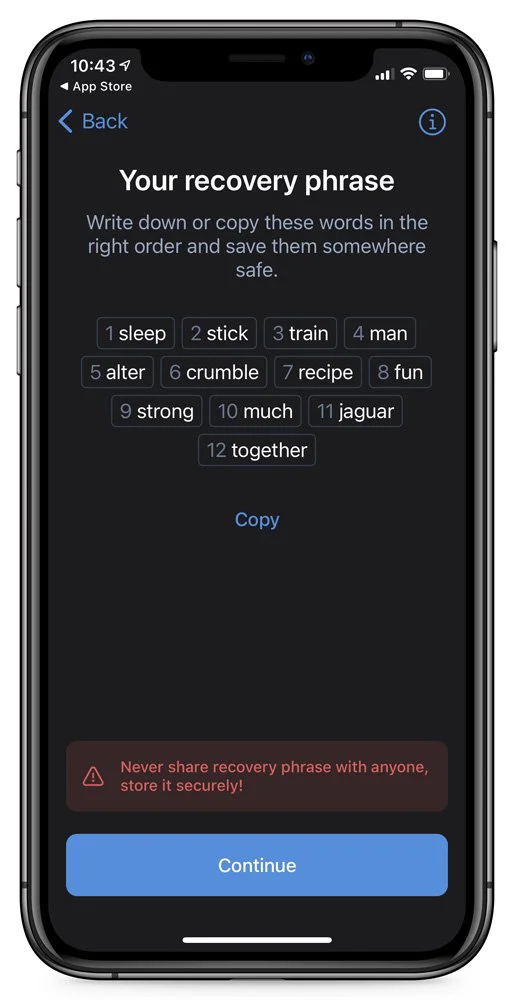
Readers should note that while we have shared a screenshot of a Trust Wallet recovery phrase above, we never created the above wallet. You should never share your recovery phrase with anyone.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
For approximately two weeks, BleepingComputer has been tracking a Twitter phishing scam targeting Trust Wallet and MetaMask users that steals cryptocurrency wallets by promoting fake technical support forms.
The phishing scam starts with legitimate MetaMask or Trust Wallet users tweeting about a problem they are having with their wallets. These issues range from stolen funds, problems accessing their wallets, or issues using the apps.
The scammers respond to these tweets pretending to be the apps’ support team or users who say “Instant support” helped them with the same problem. These tweets recommend that users visit the included docs.google.com or forms.app links to fill out a support form and receive help, as shown below.
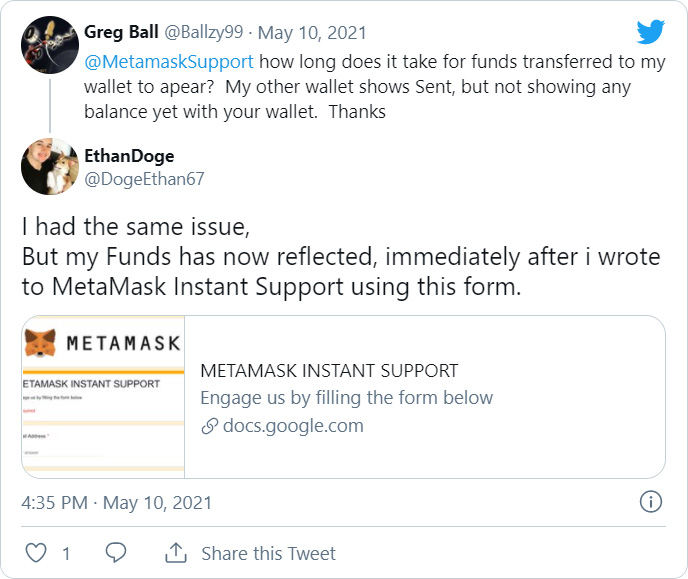
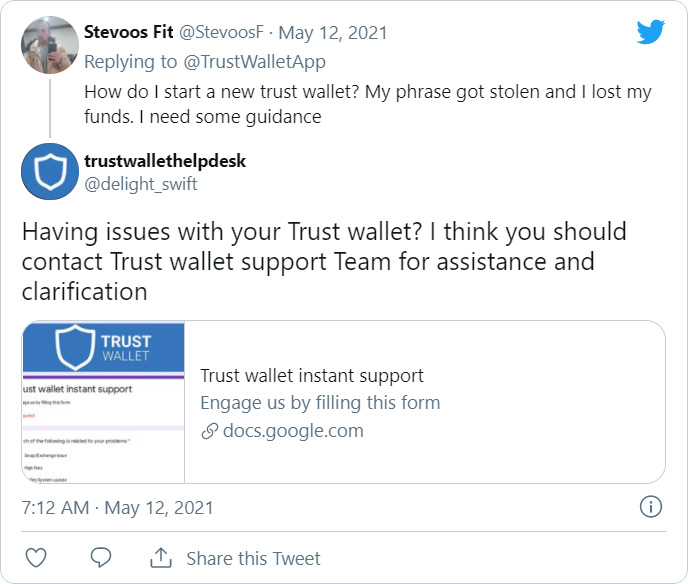
When users visit these links, they will be shown a page pretending to be a support form for Trust Wallet or MetaMask.
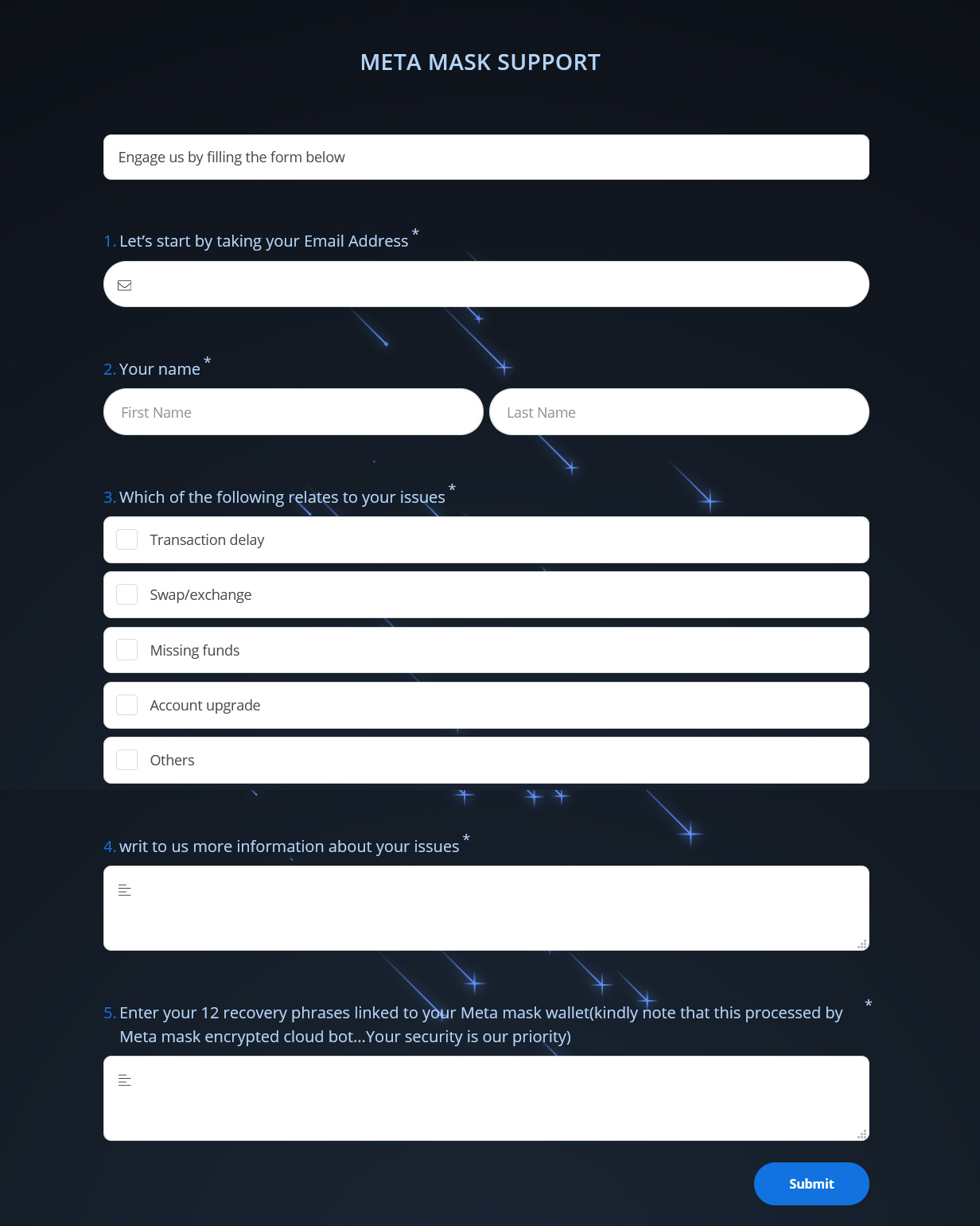 Fake MetaMask support form Fake MetaMask support formSource: BleepingComputer | 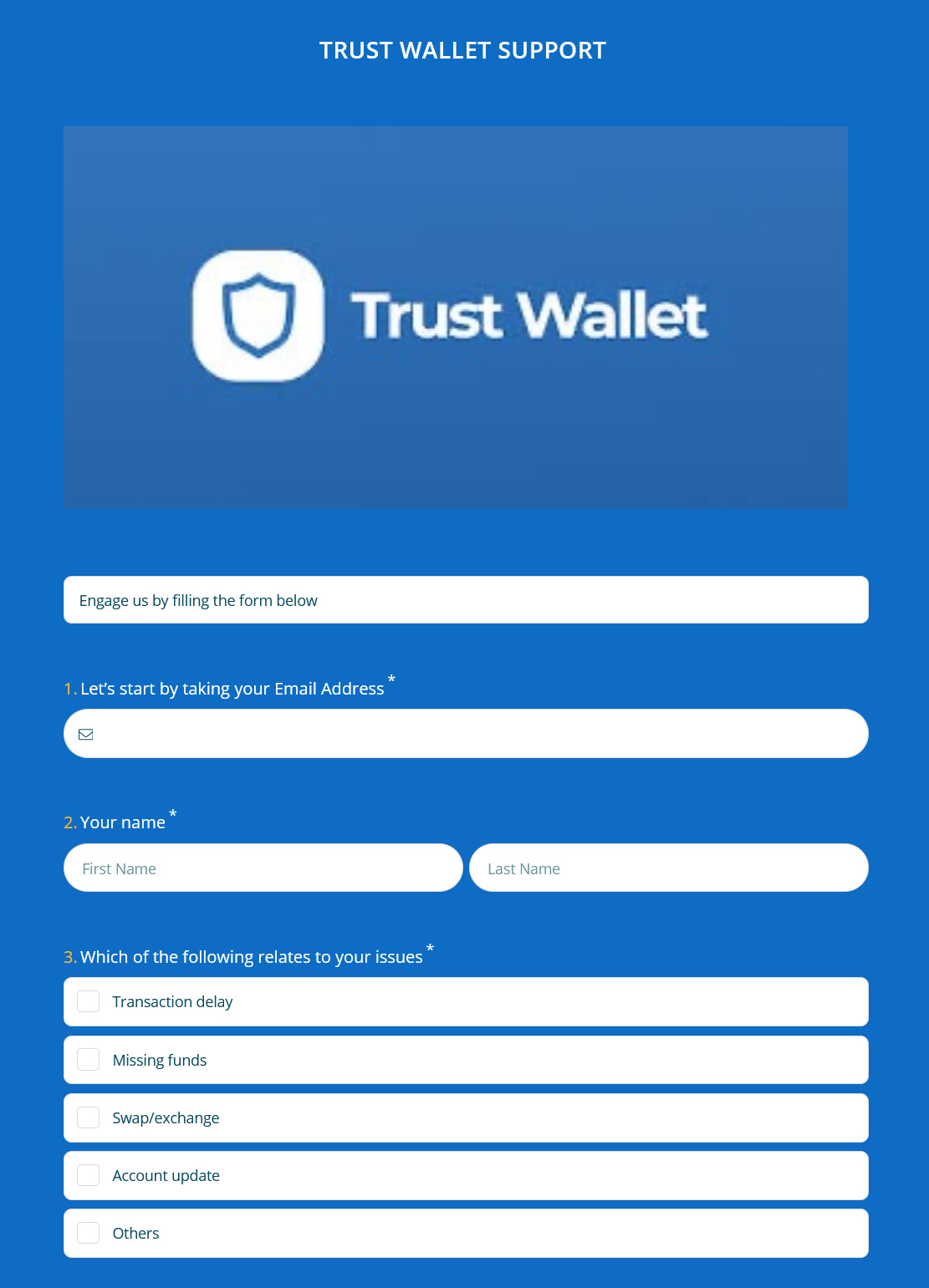 Fake Trust Wallet support form Fake Trust Wallet support formSource: BleepingComputer |
These forms request a visitor’s email address, name, the issue they are having, and then the crown jewel of the scam, the wallet’s 12 recovery phrases.
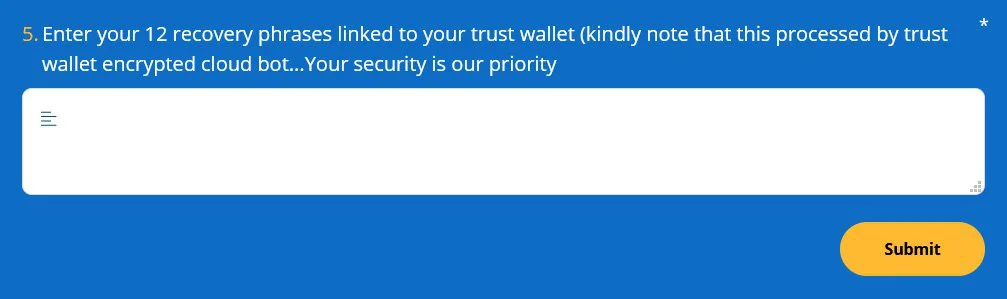
Once a Trust Wallet or MetaMask user submits their recovery phrase, the threat actors can use it to import the victim’s wallet on their own devices and steal all of the deposited cryptocurrency funds.
Unfortunately, once a threat actor steals the funds, there is little a user can do to recover them.
Cryptocurrency phishing scams like this have been extremely successful in the past, with one MetaMask user losing over $30,000 in cryptocurrency after sharing their recovery phrase.
Also Read: The DNC Singapore: Looking At 2 Sides Better
First and foremost, never enter your wallet’s recovery phrase in any app or website or share it with someone else. The only time you should ever use your recovery phrase is to import your wallet on a new device you own.
Furthermore, a legitimate company will not use Google Docs or online form-building sites for support requests. Only ask for support at the specific sites associated with the application or device you need help with.
Even then, NEVER provide your recovery phrase.
As it is easy to create lookalike domains that impersonate legitimate sites, when it comes to cryptocurrency and financial assets, always type the URL you wish to visit into your browser rather than relying on links in emails. This way, you can avoid mistakenly clicking on phishing sites that impersonate a legitimate service.