KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Trucking and freight logistics company Forward Air has suffered a ransomware attack by a new ransomware gang that has impacted the company’s business operations.
Forward Air is a leading trucking and air freight logistics company based out of Tennessee, USA. The company generated $1.4 billion in revenue for 2019 and employs over 4,300 people.
Last week, FreightWaves reported that Forward Air suffered a cyberattack that forced them to take their systems offline to prevent the attack’s spread. Forward Air later confirmed this attack in a statement to BleepingComputer.
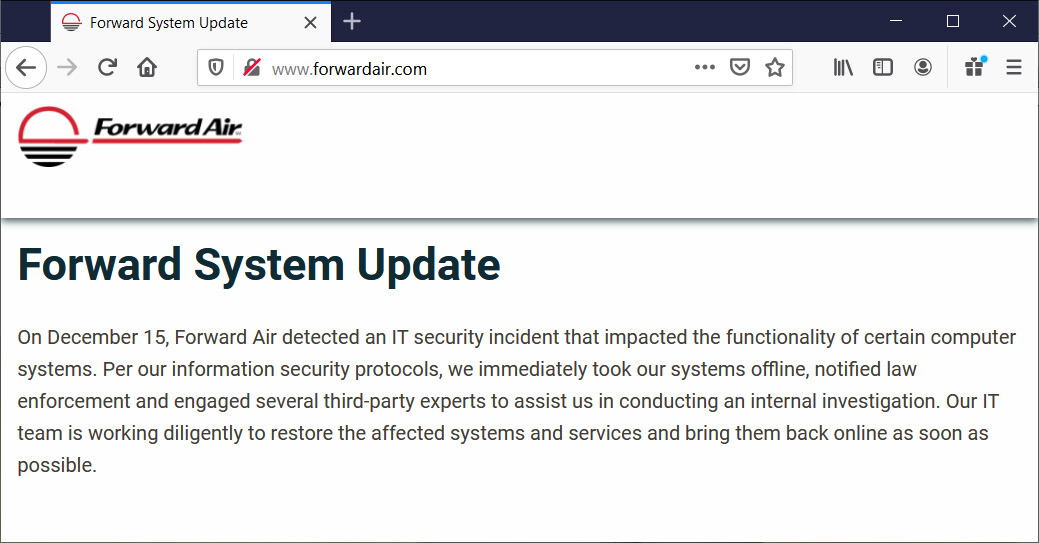
“On December 15, Forward Air detected an IT security incident that impacted the functionality of certain computer systems. Per our information security protocols, we immediately took our systems offline, notified law enforcement and engaged several third-party experts to assist us in conducting an internal investigation. Our IT team is working diligently to restore the affected systems and services and bring them back online as soon as possible,” Forward Air shared in a statement to BleepingComputer.
According to FreightWaves, the attack has led to business disruption as the paperwork required to release freight from customs was stored on the shutdown systems and is not available.
Also Read: Personal Data Websites: 3 Things That You Must Be Informed
At this time, Forward Air’s website is down and just displays a message about the “IT security incident” and that the site is down while they restore affected systems.
Sources have told BleepingComputer today that Forward Air suffered a cyberattack by a new ransomware operation known as Hades.
Update 12/21/20 6:37 PM EST: After we published our story, Forward Air filed a Form 8-K with the Securities and Exchange Commission disclosing that they suffered a ransomware attack.
“On December 15, 2020, Forward Air Corporation (the “Company”) detected a ransomware incident impacting its operational and information technology systems, which has caused service delays for many of its customers. Promptly upon its detection of the incident, the Company initiated response protocols, launched an investigation and engaged the services of cybersecurity and forensics professionals. The Company has also engaged with the appropriate law enforcement authorities,” the Form 8-K states.
The Hades ransomware gang behind this attack began operating about a week ago in human-operated attacks against the enterprise.
When encrypting a victim, it will create a ransom note named ‘HOW-TO-DECRYPT-[extension].txt’ that resembles notes used by the REvil ransomware group, as can be seen below.
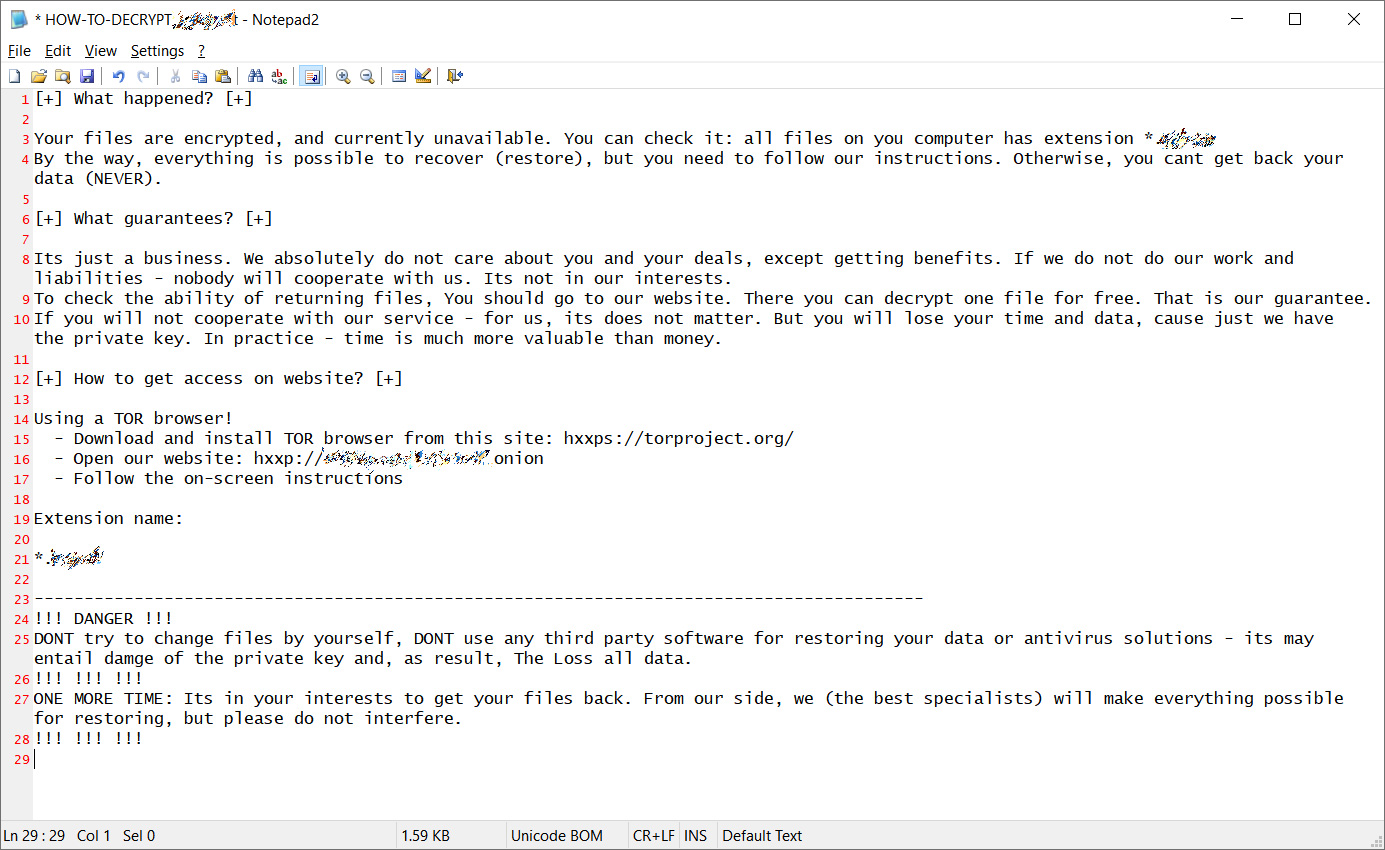
Enclosed in the ransom notes is a Tor site URL that is unique to each victim. This URL brings you to a Tor site containing information about the attack and a Tox messenger address that victims can use to contact the attackers, which is the same for all victims.
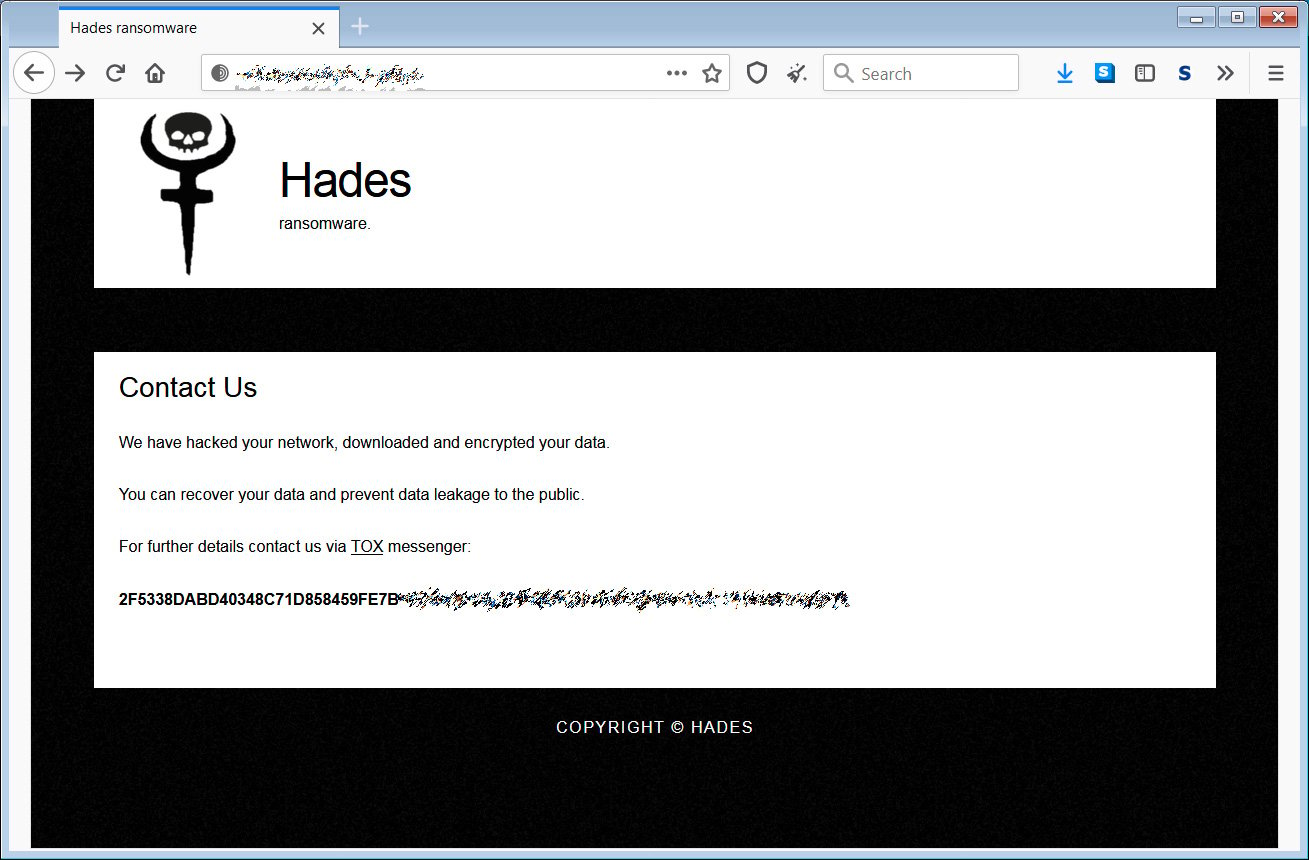
When we reached out via Tox to the ransomware actors, they were unwilling to provide any information about their attacks. They did, though, share a Twitter account whose name indicates they will use it to leak files stolen during attacks.
Also Read: PDPA For Companies: Compliance Guide For Singapore Business
It is not known how much money is demanded to recover files, and a sample of the ransomware has not been found.