KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





The Trickbot malware has been upgraded with a network reconnaissance module designed to survey local networks after infecting a victim’s computer.
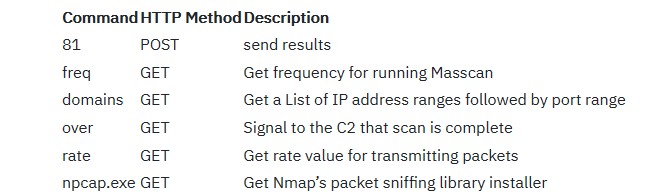
This new module, dubbed masrv, uses the open-source masscan tool, a mass port scanner with its own TCP/IP stack and capable of scanning large swaths of the Internet in a matter of minutes.
Trickbot uses the network scanner module to map the victims’ networks and send home information on any devices with open ports.
The module is deployed as a Windows DLL file, with a 32-bit or 64-bit architecture depending on the system the malware has infected.
“Both DLLs we observed are debug builds and log their execution into standard output,” as Kryptos Logic Vantage Team said in a report published on Monday.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
This hints at the module being in a test phase, with Trickbot gang still testing waters to see if using a network mapping could help them boost the number of infected devices and their malware’s efficiency.
All the info on network devices with open ports is exfiltrated to the malware’s command-and-control server for the malware operators to decide if the discovered machines are worth adding to the botnet.
The TrickBot gang has previously released a standalone reconnaissance tool known as LightBot in the form of a PowerShell script used for scoping out an infected victim’s network for high-value targets.
“This new module is an indication of the actor’s continued investment in improving their network reconnaissance toolkit, even after recent disruption efforts,” the Kryptos Logic researchers added.
Microsoft and other security firms disrupted the Trickbot botnet following a coordinated operation that led to the takedown of Trickbot C2 servers in October 2020.
Even though this operation managed to disable roughly 94% of Trickbot’s critical infrastructure, the tough to kill botnet bounced back in January 2021 with a new series of phishing emails and lures.
Trickbot is a malware strain that surfaced in October 2016 as modular banking malware. Since then, it was continuously upgraded with new modules and features.
Although initially used only for harvesting sensitive data, Trickbot has evolved into a highly dangerous and prevalent malware dropper that will deliver additional, usually a lot more dangerous, malware payloads.
This usually happens after all useful information — including system info, credentials, and any interesting files — has been already collected and exfiltrated.
Also Read: Personal Data Websites: 3 Things That You Must Be Informed
Trickbot is particularly dangerous to enterprises since it propagates through corporate networks and, if it gets admin access to a domain controller, it will steal the Active Directory database to collect more network credentials.
Last month, Trickbot’s developers have added another new module designed to probe infected devices for UEFI vulnerabilities, which would give the malware ultimate control over compromised machines.
With access to the UEFI firmware, the Trickbot gang would be able to establish persistence that can’t be removed even after operating system reinstalls or storage drives replacements.