KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







TrickBot, one of the most active botnets on the planet, recently has suffered some strong blows from actors in the cybersecurity industry aiming at disrupting its operations.
The damaging actions hold the signature of the U.S. Cyber Command branch of the Department of Defense and multiple security companies united by the same goal: pulling the breaks on TrickBot infections.
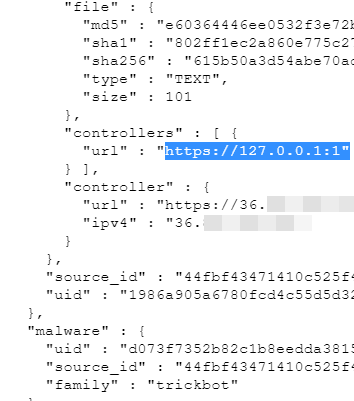
The Trickbot operation started hitting serious snags towards the end of September when enslaved computers received an update that cut them off from the botnet by changing the command and control server address to 127.0.0.1 (localhost).
According to information from Intel471, the liberating configuration file of unknown origin reached Trickbot-infected systems again on October 1, reports Brian Krebs.
On October 10, The Washington Post reported that the U.S. Cyber Command carried out a campaign seeking to disrupt the Trickbot botnet ahead of the presidential elections.
It is unclear, though, if the above actions were the work of the U.S. Cyber Command as the DoD branch did not offer a comment.
In announcements today, Microsoft and ESET said that together with cybersecurity and telecommunications companies initiated activities meant to disrupt Trickbot.
In a statement to BleepingComputer, ESET threat research chief Jean-Ian Boutin said that the efforts started several months ago and that multiple disruption actions occurred during this period.
Their activities aim for long-term effects, an objective that requires careful analysis of the gathered data, and the best way to use it against Trickbot.
Up to this point, the partners took down an undisclosed number of C2 servers, most of them IP-based, by following the legal procedures to cut their communication with the bots (sinkholing or firewalling at ISP level).
Also Read: 6 Simple Tips on Cyber Safety at Home
The action started at Microsoft’s initiative, after the U.S. District Court for the Eastern District of Virginia granted the company’s request for a court order to stop Trickbot activity.
In a post today, Microsoft says that it formed a global network of partners led by its Digital Crimes Unit (DCU). The partnership included ESET, Lumen’s Black Lotus Labs, NTT Ltd, Broadcom’s Symantec enterprise business, the Financial Services Information Sharing and Analysis Center (FS-ISAC), and the Microsoft Defender team.
Boutin told us that the partners were in contact with law enforcement and sent them technical data. However, the researcher is not aware of any connection between their operation and the one carried out by the Cyber Command.
The USDOD branch may have run its operation using information received indirectly from the cybersecurity organizations and unbeknownst of the same efforts from their part.
The endeavor from ESET and partners against Trickbot, while significant, has no guarantee of success. The threat actor has fallback mechanisms that allow them to maintain the botnet and could recover lost computers infected with Trickbot; it is not an easy task, though.
The researcher sees this operation “as a rolling disruption effort” because of Trickbot infrastructure’s resilience to takedown attempts.
“At this point, it’s impossible to know how Trickbot’s operators will react. What we know is that a portion of the C&C servers used to send commands and updates to bots will become unresponsive. They will have to work hard to re-establish control over the entirety of the Trickbot’s compromised hosts” – Jean-Ian Boutin, Head of Threat Research at ESET
Advanced Intel‘s Vitali Kremez, who tracks TrickBot’s operation, told BleepingComputer that US Cyber Command’s operation led to a short term disruption of the botnet, but it quickly recovered.
“While the botnet disruption did impact the normal flow of the TrickBot infections, it seems like the group was able to recover and adapt quickly resuming their regular activity,” – Vitali Kremez
Lumen’s Black Lotus Labs notes the same in their blog post today, saying that the disruption did not prevent new Trickbot infections “because the botnet infrastructure remained intact.”
To get an idea of the complexity of the operation and why it is so difficult to bring it to an end, ESET’s automatic systems examined more than 125,000 Trickbot samples with over 40,000 configuration files for at least 28 individual plugins used by the malware to steal passwords, modify traffic, or self-propagate. These components are likely written by different developers and some connect to their own servers for updates.
Also Read: The Impact of GDPR and PDPA in Singapore
In the configuration file of a main module that determines which plugins should be installed there is a list of hardcoded C2 server addresses. After connecting to one of the, it retrieves a second list of C2 servers to download the default components.
On top of these, the threat actor also relies on dedicated C2 servers to control the plugins and to exfiltrate stolen data.
This setup enabled the threat actor to maintain its grip on computers in almost every country of the world, allowing them to quickly bounce back into business when disruption attempts occur.
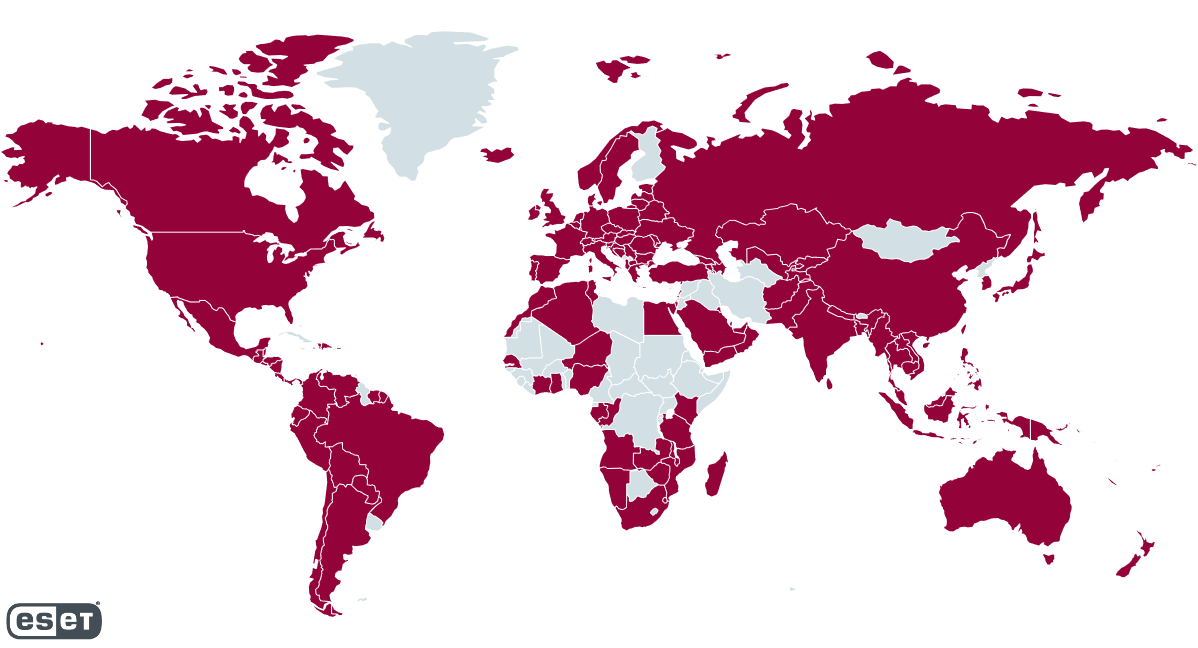
For the past four years, TrickBot infected more than one million computers in all regions of the world, according to telemetry data from ESET, one of the companies involved in the operation.
Initially a banking trojan, Trickbot turned into a botnet that distributed various malware. In April 2019, security company Cybereason reported that the malware was using the Emotet botnet for distribution and further delivered Ryuk ransomware.
A few months later, Deep Instinct announced that they were able to recover a database of 250 million email accounts from a Trickbot module used for spreading the malware over email.
Besides its role to drop ransomware, Trickbot also ran reconnaissance activity on the compromised network, stealing sensitive information before letting Ryuk deal the final blow.
The US government considers ransomware a top threat to the US 2020 elections as attacks can hold voter information and election results hostage and impact election systems.
“For elections, a ransomware attack could deny access to voter registration data, election results, and other sensitive information. It could also inhibit access to important election systems during critical operational periods such as registration and candidate filing deadlines,” the US govt’s Cybersecurity & Infrastructure Security Agency (CISA) stated in a report.
Both the Ryuk and Conti ransomware gangs have partnered with TrickBot to gain access to compromised networks.
When a computer becomes infected with TrickBot, the trojan will eventually provide remote access to one of the ransomware gangs. These attackers will then use the infected computer as a launching pad to compromise the entire network and deploy their ransomware.
By disrupting the TrickBot botnet, ransomware operations would also be impacted as they could no longer utilize the botnet to gain access to corporate networks.
Unfortunately, attacks continued unabated, as shown by the wide-scale Ryuk ransomware attack on Universal Health Services (UHS) in September.
The actors behind Emotet, Trickbot, and Ryuk are professional cybercriminals running operations with a global reach and aiming for big money.