KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A decryptor for the ThunderX ransomware has been released by cybersecurity firm Tesorion that lets victims recover their files for free.
ThunderX is a relatively new ransomware that became active towards the end of August 2020.
This week, Tesorion was able to find a flaw in the ransomware’s encryption so that victims can decrypt their files without paying a ransom.
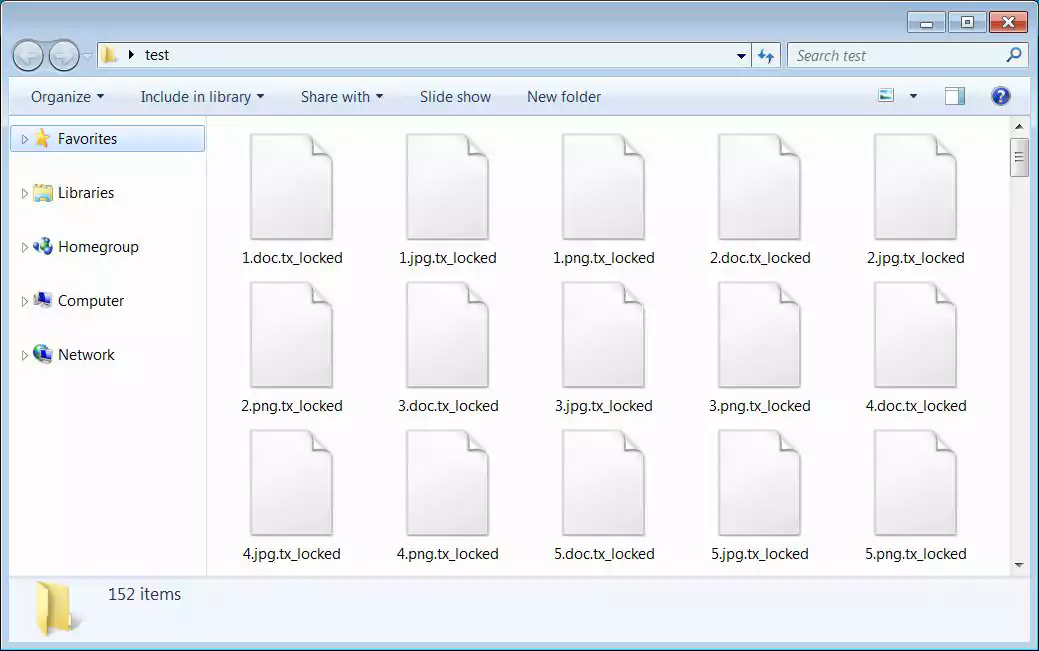
This decryptor can decrypt files encrypted by the ransomware’s current version and have the .tx_locked extension, as shown below.
To use the decryptor, you will also need to upload both a copy of the readme.txt ransom note and an encrypted file so that a decryption key can be generated.
To use the decryptor, you will need to upload both a copy of the readme.txt ransom note and an encrypted file to generate a decryption key.
Once you have the ransom note and encrypted files, download Tesorion’s ThunderX Ransomware decryptor and execute it. When prompted, agree with the license agreement, and you will see the following screen.
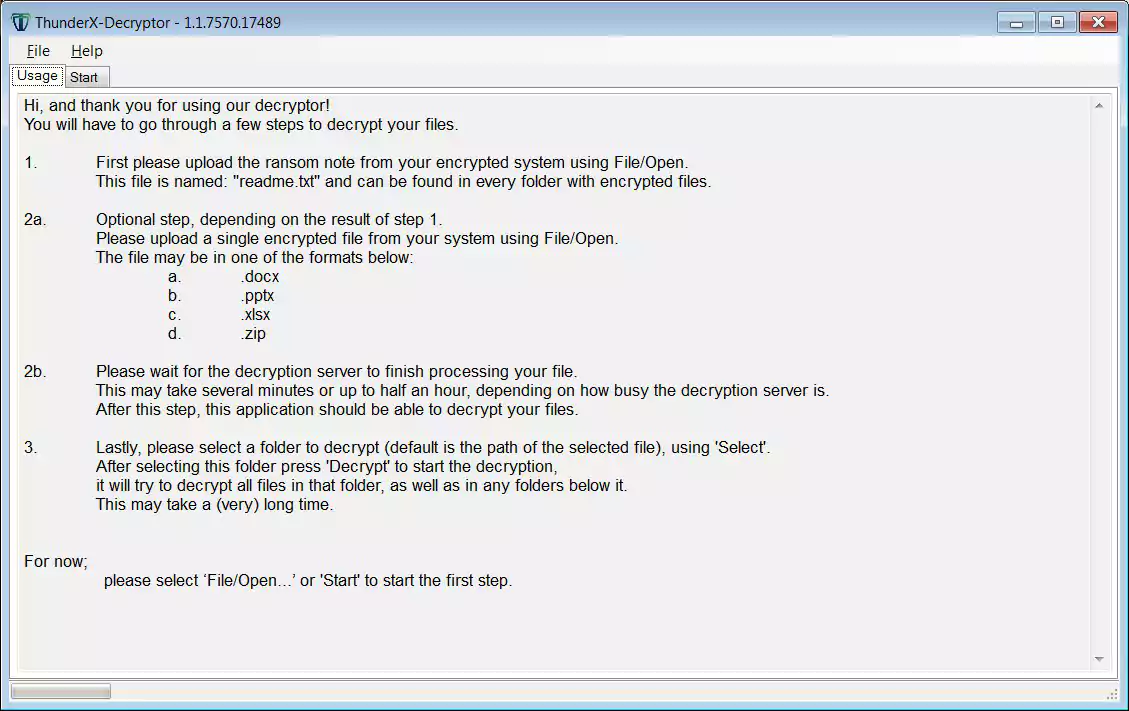
Click on File > Open and select the readme.txt ransom note. Then press ‘Send‘ to upload the ransom note to Tesorion.
Also Read: Digital Transformation – Do or Die in 2020
You will now be prompted to upload an encrypted file. Please follow the instructions and upload a PPTX, DOCX, XLSX, or ZIP file.
Once you send the files, Tesorion’s servers will attempt to determine your decryption key. This process can take quite a while, so please be patient.
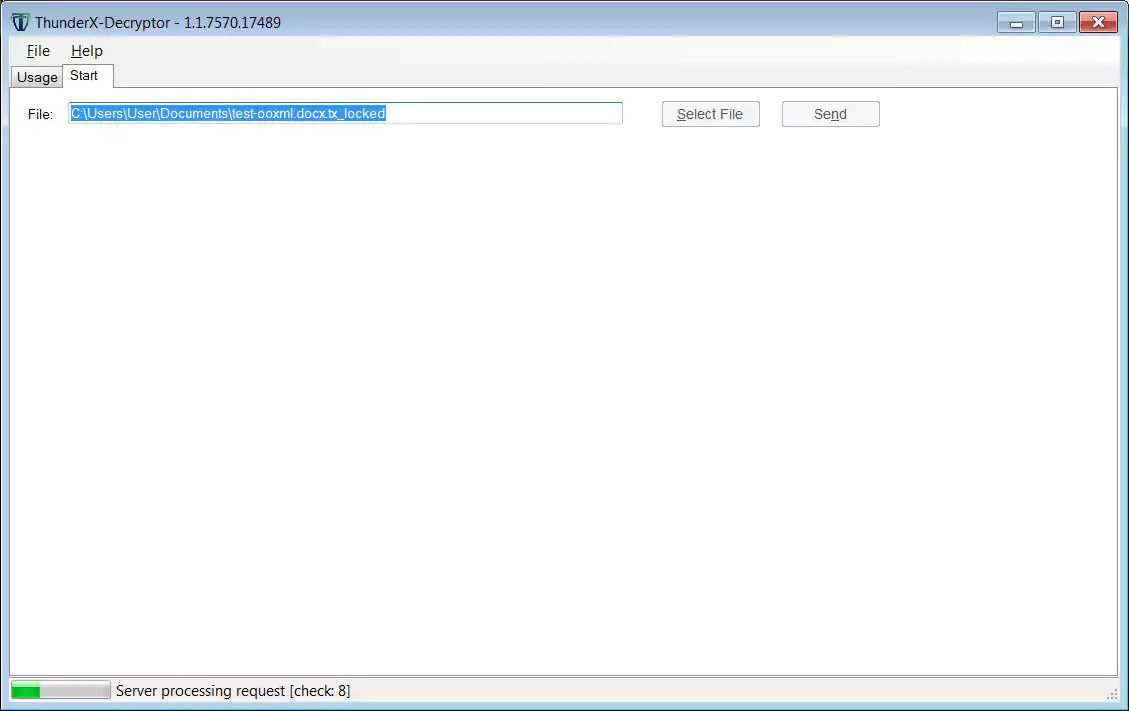
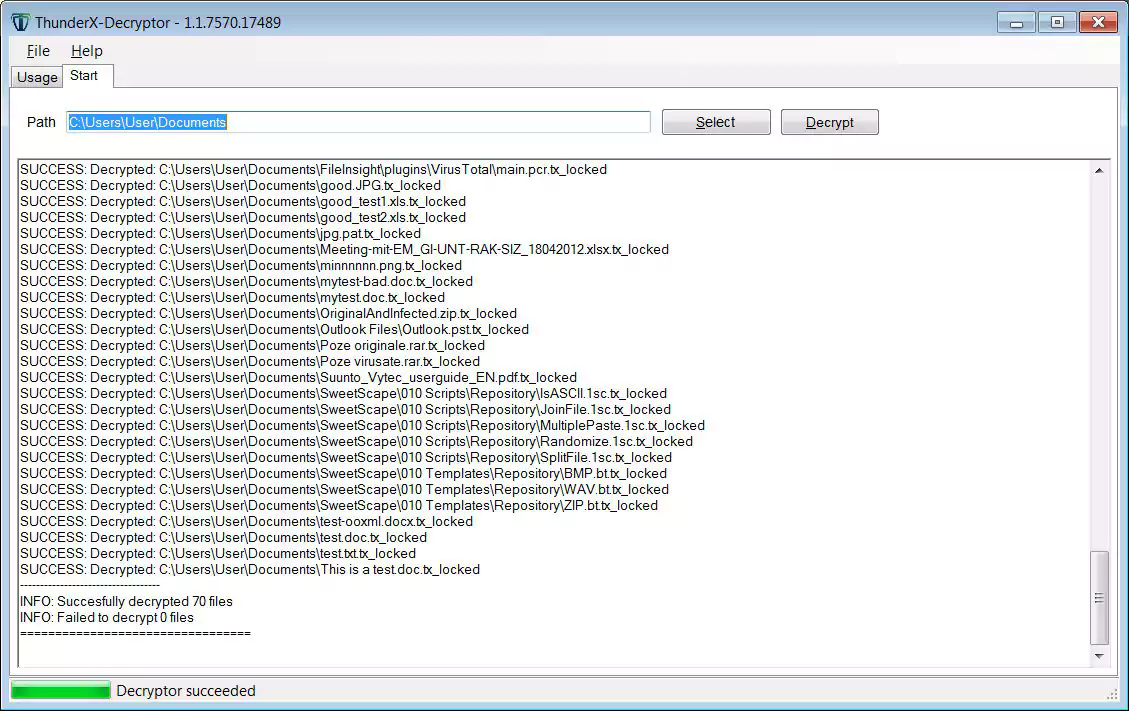
When done, a decryption key will be downloaded to the decryptor automatically, and you will be prompted to select a folder to decrypt.
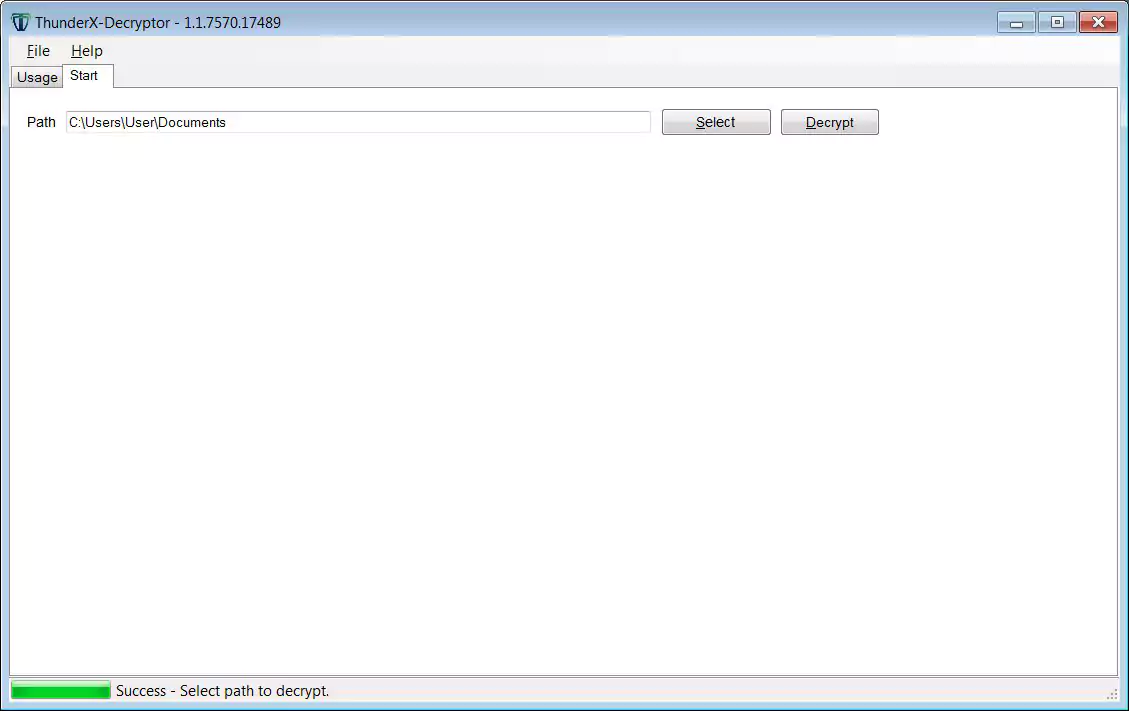
To select a folder, click on the select button and select the root folder of a drive (C:, D:, etc) or a particular folder.
Then press the ‘Decrypt‘ button to decrypt all the files in that folder and its subfolders.
When finished decrypting, you will see a summary showing the number of files decrypted and those with problems.
If you have any questions or need help using the decryptor, you can ask in our dedicated Ransomware Help and Tech Support forum.
Also Read: Free Privacy Policy Compliance Review