KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Scammers are estimated to have made $80 million per month by impersonating popular brands asking people to participate in fake surveys or giveaways.
Researchers warn of this new trend in global fraud schemes involving targeted links to make investigation and take-down increasingly challenging.
According to current estimates, these massive campaigns resulted in an estimated $80,000,000 per month, stolen from 10 million people in 91 countries.
The scam themes are the typical and “trustworthy” fake surveys and giveaways from popular brands with the holiday season making targets more susceptible to fraudulent gift offerings.
Also Read: New Licensing Requirements For Cyber-Security Service Providers in 2022
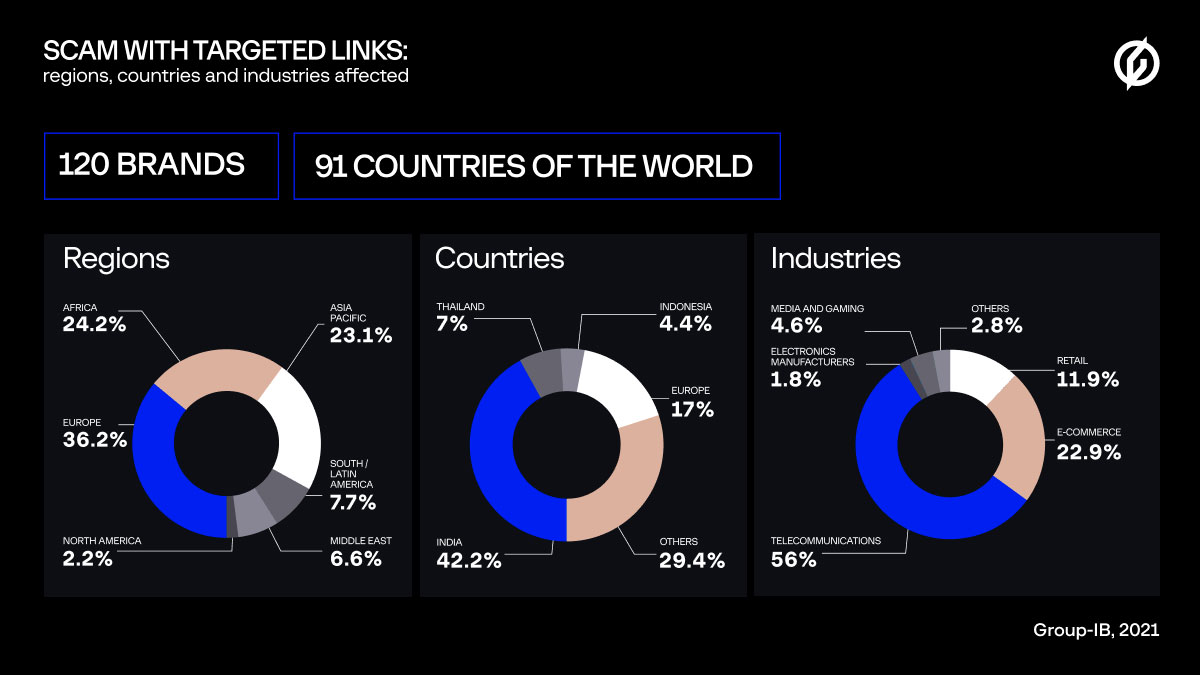
According to a report by Group-IB, there are currently 60 known scam networks that use targeted links in their campaigns, impersonating 121 brands in false giveaways.
Each network uses an average of 70 different Internet domain names as part of their campaigns, but some find great success with fewer domains, which indicates that quality beats quantity when it comes to scams.
“For each specific website that hosts fraudulent content, Group-IB researchers were able to analyze where the visitors came from.”
“The main sources of traffic for targeted links operators are India (42.2%), Thailand (7%), and Indonesia (4.4%), among others.”
However, Group-IB told BleepingComputer that more domains do not always equate to more traffic for a campaign.
“The largest detected network in terms of the number of domain names included 232 domain names, according to the findings of Group-IB’s DRP team. It is possible that not all of the websites remain active. Such a large number of domains is created to make it possible to redirect the traffic to a related resource as soon as possible if an active one is blocked. This way, the fraudsters ensure continuous operation of their scamming scheme.
However, very often, a large number of domain names on the network does not mean that this network is the most visited. Group-IB, for instance, has recorded a network of resources containing 51 domain names with targeted links but was one of the largest networks in terms of the traffic attracted.
Judging from the number of visitors, almost 10 million people can fall victim to the scamming scheme per month on the above mentioned network alone, while the traffic attracted to the largest network in terms of the number of domain names was about 2-fold less.” – Group-IB.
The scammers target their victims via contextual advertising, advertising on legal and completely rogue sites, social media posts, forum posts, SMS, mailouts, and pop-up notifications.
Also Read: A Closer Look: The Personal Information Protection Law in China
The goal is to direct them all to scam sites that are clones of the official sites of the impersonated brands.
While Group-IB did not share a list of brands targeted by these campaigns, BleepingComputer has seen fake surveys and giveaways impersonating Google, Target, Amazon, Microsoft, Apple, and Samsung in the past.
Clicking on the first URL triggers a lengthy string of redirects, during which the actors gather information about the prospective victim, like their language, IP, browser, location, etc.
This process is essential for delivering a page that matches each victim’s demographic and potential interests.
.jpg)
Simultaneously, this process severely hampers the investigation and take-down of these fraudulent sites, especially when the scam networks are so large and use many sites.
In most cases, the victim will be presented with a prize-winning opportunity that is only a step away from being delivered on their location.
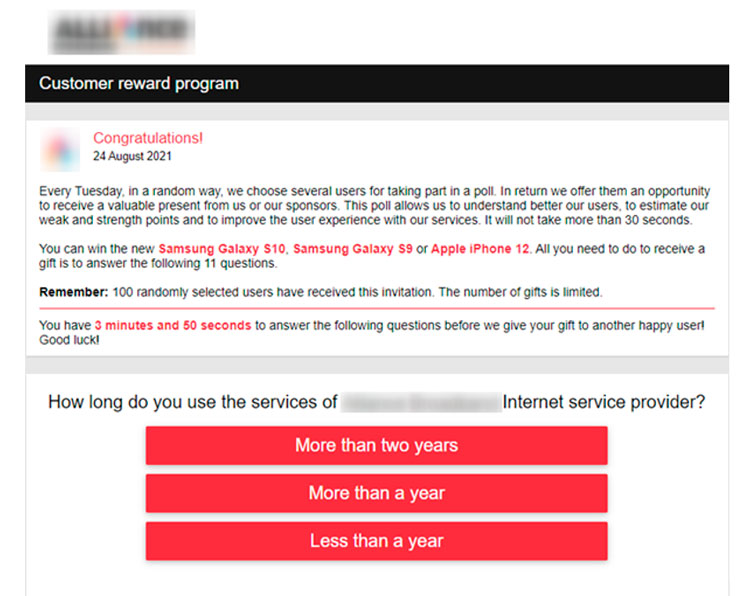
At this final step, the actors request full personal details, bank card data (including expiration date and CVV) and sometimes even ask victims to perform a small “test payment” to allegedly verify themselves.
These details are then used for fraudulent online purchases, the registration of fake accounts, and the assumption of counterfeit identities. In most cases, they are sold to multiple actors on the dark web.
Big brands offer Christmas gifts these days, and they also run giveaways or surveys with prizes, which is precisely what the scammers aim to exploit.
To ensure the legitimacy of a giveaway, check the email account and confirm that the website address is an official domain of the brand.
If a brand runs a campaign, it should be easy to find a relevant post on their official social media channels, and even there, make sure you’re checking the verified accounts.
Finally, check the domain on the giveaway page you’ve landed and confirm it belongs to the claimed brand.
Under no circumstances would any prize winner have to share their banking details or any other personal data besides their name and postal address.