KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Researchers set up 320 honeypots to see how quickly threat actors would target exposed cloud services and report that 80% of them were compromised in under 24 hours.
Malicious actors are constantly scanning the Internet for exposed services that could be exploited to access internal networks or perform other malicious activity.
To track what software and services are targeted by threat actors, researchers create publicly accessible honeypots. Honeypots are servers configured to appear as if they are running various software as lures to monitor threat actors’ tactics.
Also Read: Got A Notice of Data Breach? Don’t Panic!
In a new study conducted by Palo Altos Networks’ Unit 42, researchers set up 320 honeypots and found that 80% of the honeypots were compromised within the first 24 hours.
The deployed honeypots included ones with remote desktop protocol (RDP), secure shell protocol (SSH), server message block (SMB), and Postgres database services and were kept alive from July to August 2021.
These honeypots were deployed worldwide, with instances in North America, Asian Pacific, and Europe.
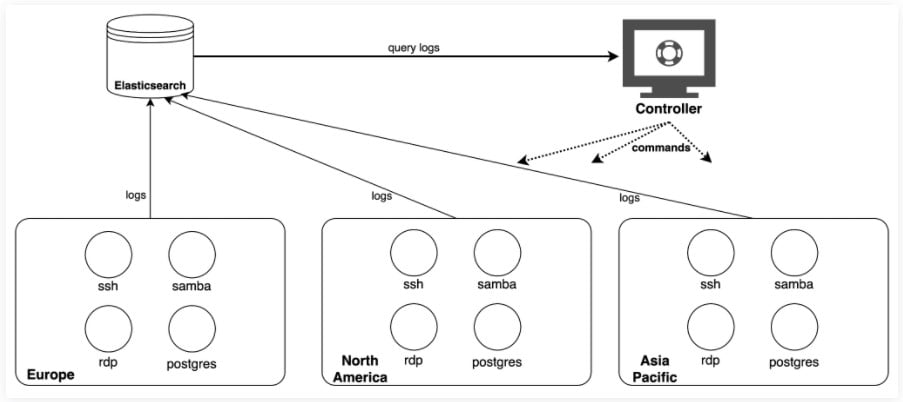
The time to first compromise is analogous to how much the service type is targeted.
For SSH honeypots which were the most targeted, the mean time for the first compromise was three hours, and the mean time between two consecutive attacks was about 2 hours.
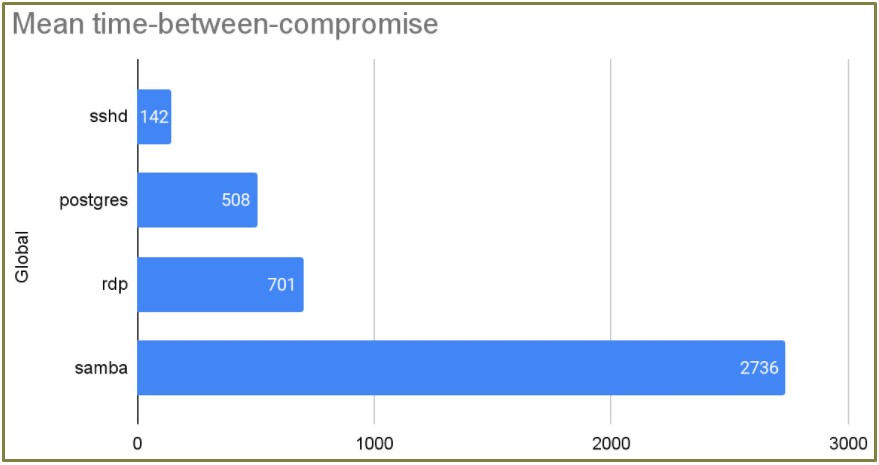
Unit 42 also observed a notable case of a threat actor compromising 96% of the experiment’s 80 Postgres honeypots in just 30 seconds.
This finding is very concerning as it could take days, if not longer, to deploy new security updates as they are released, while threat actors just need hours to exploit exposed services.
Finally, regarding whether the location makes any difference, the APAC region received the most attention from threat actors.
Also Read: A Review of PDPC Undertakings July 2021 Cases
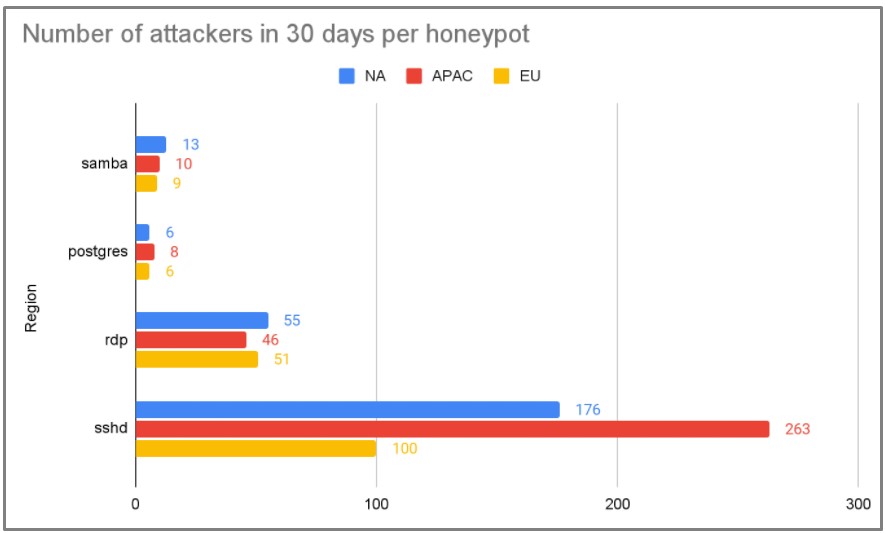
The vast majority (85%) of attacker IPs were observed on a single day, which means that actors rarely (15%) reuse the same IP on subsequent attacks.
This constant IP change makes ‘layer 3’ firewall rules ineffective against the majority of threat actors.
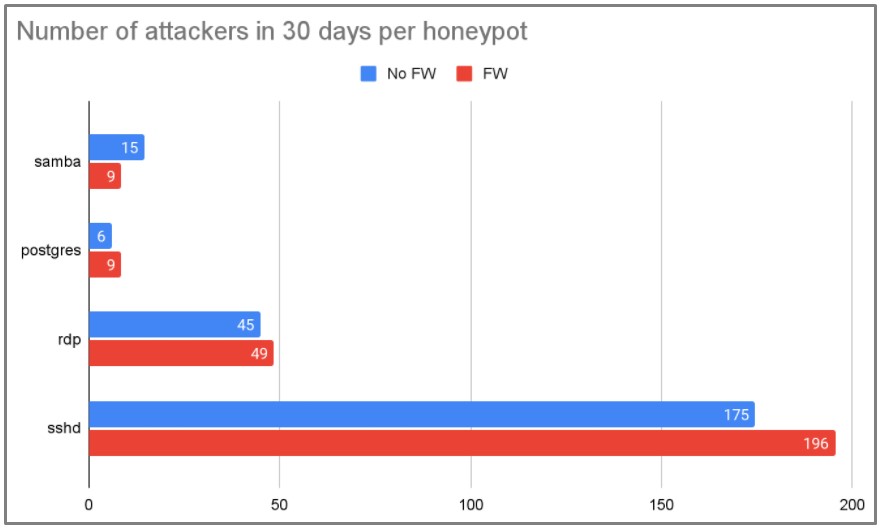
What could have better chances of mitigating the attacks is to block IPs by drawing data from network scanning projects which identify hundreds of thousands of malicious IPs daily.
However, Unit 42 tested this hypothesis on a sub-group of 48 honeypots and found that blocking over 700,000 IPs had no significant difference in the number of attacks between the sub-group and the control group.
To protect cloud services effectively, Unit 42 recommends that admins do the following:
Finally, always install the latest security updates as they become available as threat actors rush to utilize exploits for new vulnerabilities as they are published.