KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







In this action-packed two-week edition of the ‘Week in Ransomware’, we see many new variants, with some being actively distributed. We have also seen some recent reports regarding existing ransomware, such as Conti and Dharma.
Over the past two weeks, we have seen SunCrypt becoming more active since we first reported on them last week. We also saw Conti release a new data leak site as the TrickBot actors favorite this ransomware, and Ryuk slowly fades away.
One of the longest-running ransomware operations, Dharma, continues to be extremely active and a favorite among Iranian hackers who are targeting exposed RDP servers.
Today, the FBI issued a second alert about the ProLock Ransomware stealing data from victims.
Finally, on the lighter side, we saw Thanos attempt to implement an MBR Locker component to their ransomware, which fails to work every time.
It’s a holiday weekend in the USA, so be sure to stay alert, pay extra attention to your monitoring logs, and tighten up exposed servers as its a prime time for a ransomware attack.
Contributors and those who provided new ransomware information and stories this week include: @jorntvdw, @FourOctets, @demonslay335, @BleepinComputer, @VK_Intel, @serghei, @PolarToffee, @DanielGallagher, @malwareforme, @LawrenceAbrams, @Ionut_Ilascu, @struppigel, @malwrhunterteam, @Seifreed, @fwosar, @Unit42_Intel, @GroupIB_GIB, @GDATA, @campuscodi, @Kangxiaopao, @fuscator, @JAMESWT_MHT, @fbgwls245, and @GrujaRS.
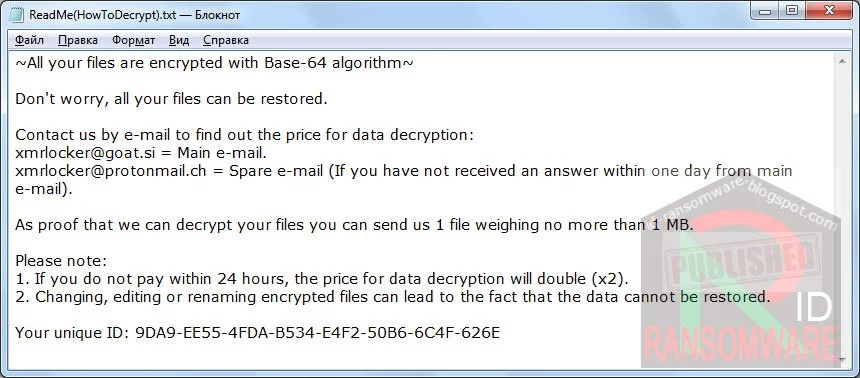
Amigo-A found the new XMRLocker Ransomware that appends the .[XMRLocker] and drops a ransom note named ReadMe(HowToDecrypt).txt.
Iranian hackers attack exposed RDP servers to deploy Dharma ransomware
Low-skilled hackers likely from Iran have joined the ransomware business targeting companies in Russia, India, China, and Japan. They are going after easy hits, using publicly available tools in their activity.
Top exploits used by ransomware gangs are VPN bugs, but RDP still reigns supreme
While ransomware groups each operate based on their own skillset, most of the ransomware incidents in H1 2020 can be attributed to a handful of intrusion vectors that gangs appear to have prioritized this year.
New BOOP STOP ransomware variant
Michael Gillespie found a new STOP Ransomware variant that appends the .boop extension.
JAMESWT found a new ransomware called ViluciWare that appends the .locked extension.
Ryuk successor Conti Ransomware releases data leak site
Conti ransomware, the successor of the notorious Ryuk, has released a data leak site as part of their extortion strategy to force victims into paying a ransom.
DarkSide Ransomware hits North American real estate developer
North American land developer and home builder Brookfield Residential is one of the first victims of the new DarkSide Ransomware.
Michael Gillespie found a new ransomware dubbed ‘Gladius’ that appends the string ‘gladius’ to encrypted file names and drops a ransom note named Your files are encrypted.txt.
SunCrypt Ransomware sheds light on the Maze ransomware cartel
A ransomware named SunCrypt has joined the ‘Maze cartel,’ and with their membership, we get insight into how these groups are working together.
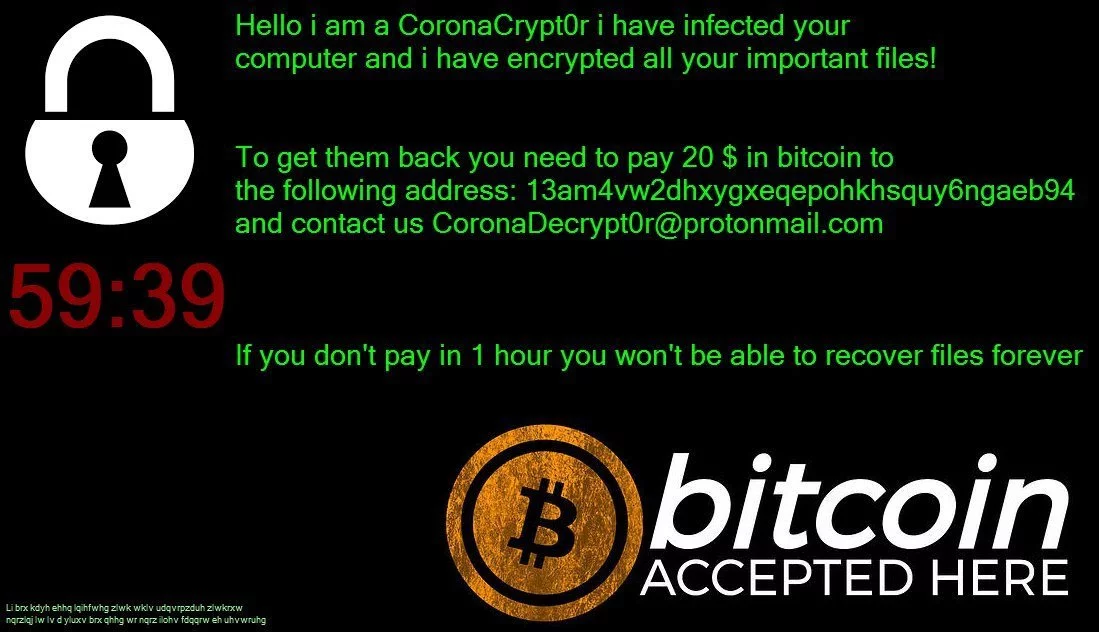
MalwareHunterTeam found the CoronaCrypt0r ransomware that appends the .locked extension.
Elon Musk confirmed Russian’s plans to extort Tesla
The FBI thwarted the plans of 27-year-old Russian national Egor Igorevich Kriuchkov to recruit an insider within Tesla’s Nevada Gigafactory, persuade him to plant malware on the company’s network, and then ransom Tesla under threat that he would leak data stolen from their systems.
New BlackHeart Ransomware variant
MalwareHunterTeam found a new variant of the BlackHeart Ransomware.
Zorab ransomware impersonates a decryptor
MalwareHunterTeam found the Zorab Ransomware impersonating a STOP Djvu decryptor.
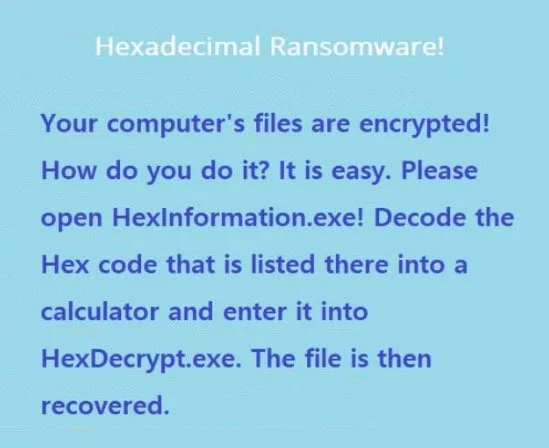
dnwls0719 found the new Hexadecimal Ransomware that prepends Lock. to the encrypted file names.
New VashSorena v4 Ransomware variant
dnwls0719 found a new variant of the VashSorena v4 Ransomware that appends the .Id-xxxxxxxx.secure extension and drops ransom notes named HELP_DECRYPT_YOUR_FILES.html and HELP_DECRYPT_YOUR_FILES.txt.
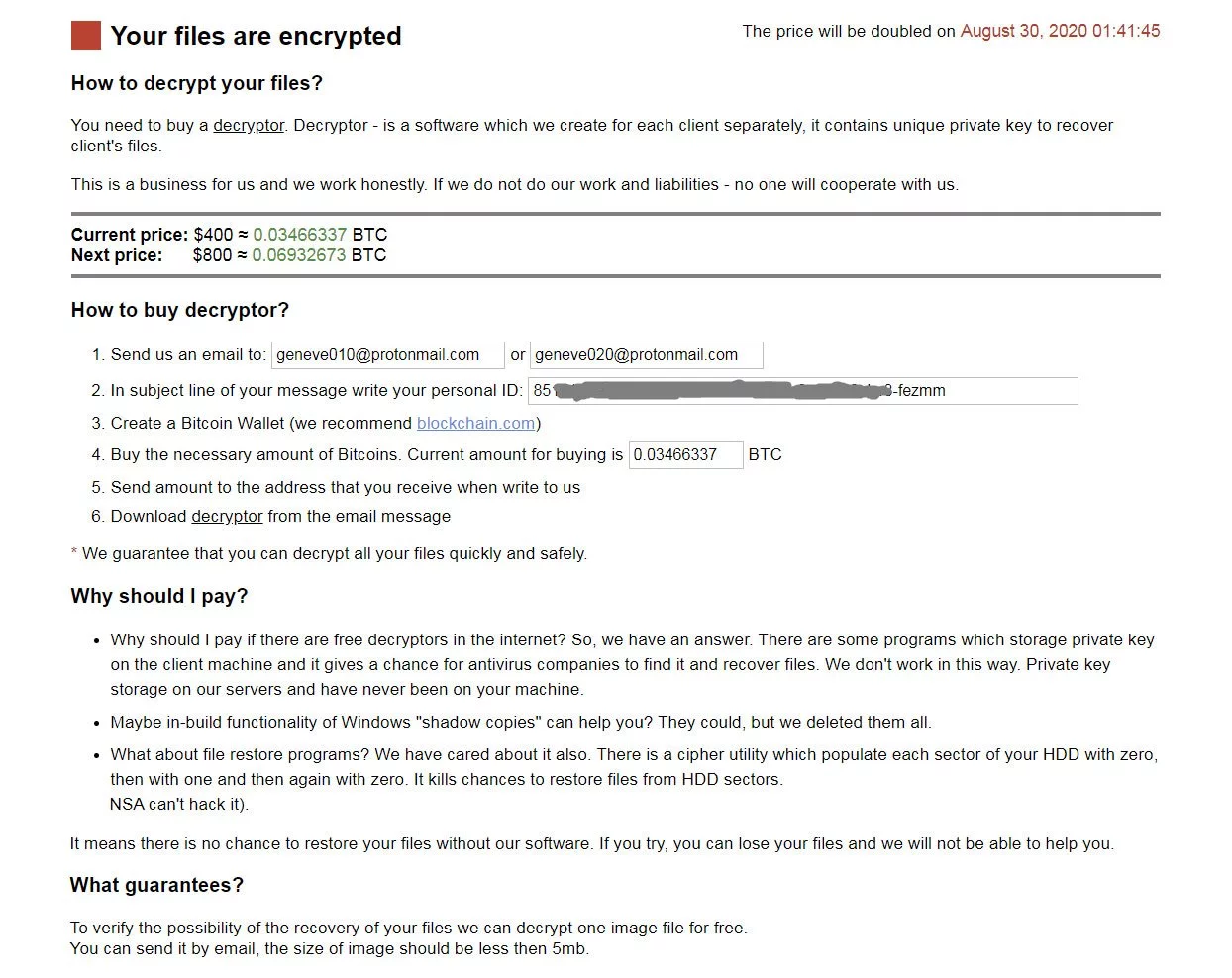
Amigo-A found a new ransomware named Geneve that appends a random extension and drops a ransom note named DECRYPT.html.
Also read: Personal Data Websites: 3 Things That You Must Be Informed
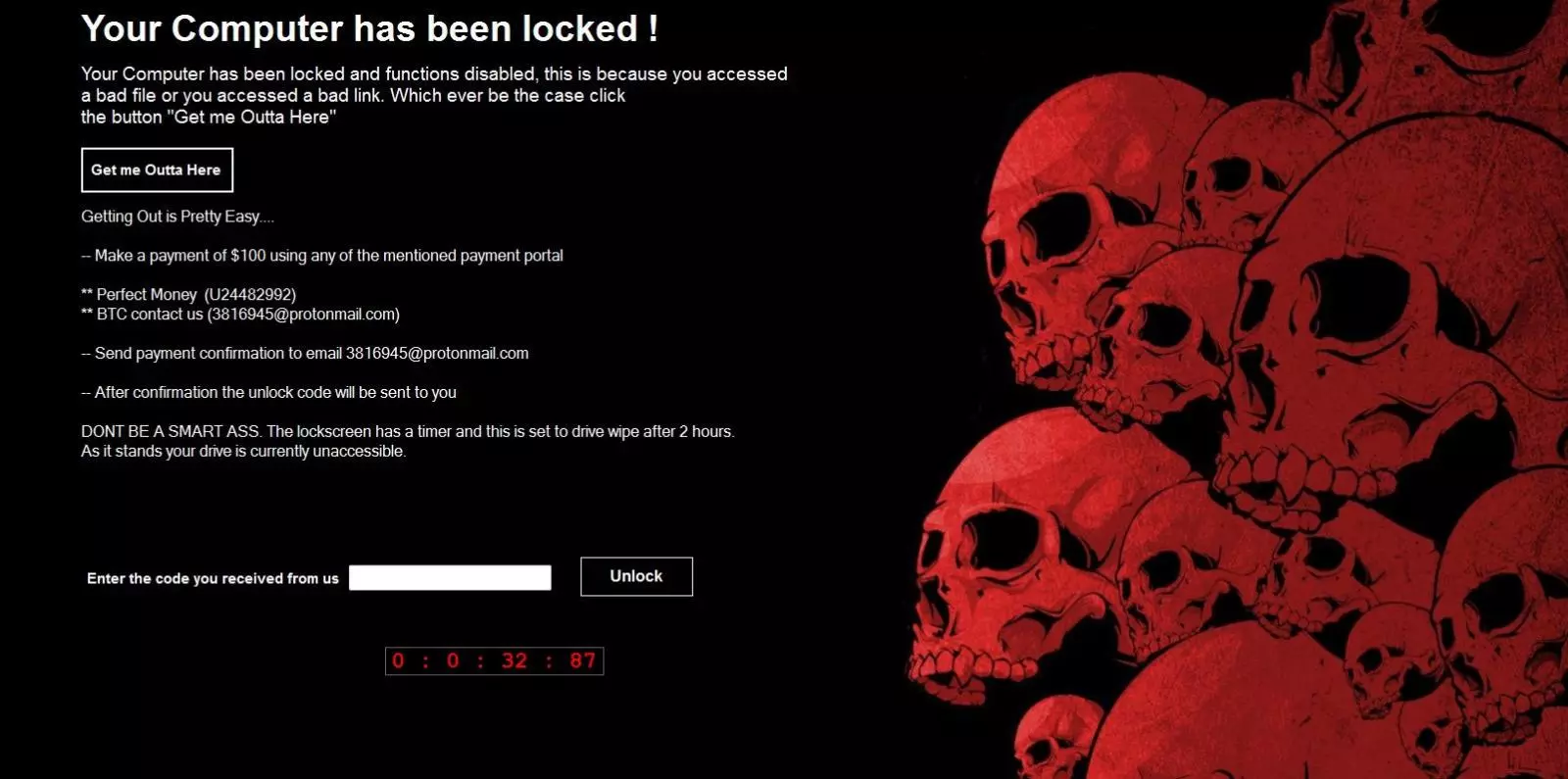
xiaopao found the BlackKnight screenlocker that requires you to enter a password to get access to the Windows desktop.
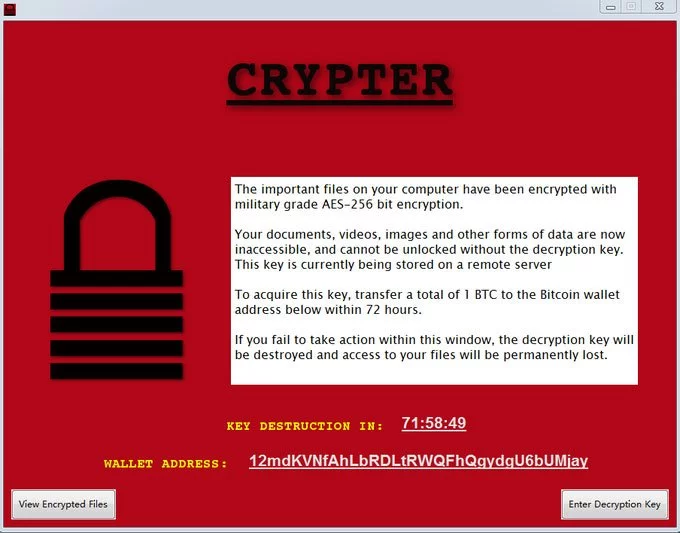
Xiaopao found a new Matrix Ransomware variant that appends the .FDFK22 extension and drops a ransom note named FDFK22_INFO.rtf.
Xiaopao found a new ransomware that appends the .locked extension.
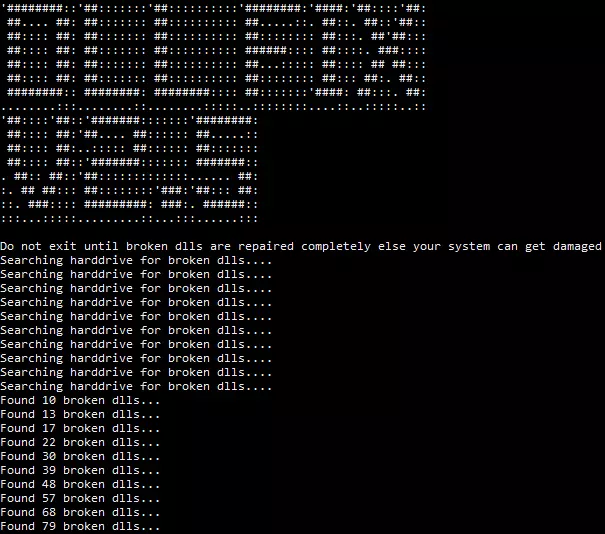
DLL Fixer leads to Cyrat Ransomware
The malware disguises as DLL fixer 2.5 (see image below). Upon execution it will display a randomly created number of corrupted DLLs it pretends to have found on the system. After the system has been encrypted, a success message for fixing the DLLs is shown.
New HiddenTear Ransomware variant
Xiaopao found a new HiddenTear variant that appends the .UGMH extension.
Onyx Mods LLC found a new HiddenTear variant that appends the .klavins extension to encrypted files.
Amigo-A found a new ransomware dubbed AESMewLocker that appends the .locked extension and drops a ransom note named READ_IT.txt.

S!Ri found a new ransomware that appends the .z3enc extension to encrypted files.
S!Ri found a new HiddenTear ransomware variant that appends the .Fappy extension to encrypted files.

Xiaopao found a new Dharma Ransomware variant that appends the .gold extension.
GrujaRS found a new ransomware named AIDS_NT that drops a ransom note named AIDS_NT_Instructions.txt.
Thanos Ransomware adds Windows MBR locker that fails every time
A new Thanos ransomware strain is trying and failing to deliver the ransom note onto compromised systems by overwriting the computers’ Windows master boot record (MBR).
FBI issues second alert about ProLock ransomware stealing data
The FBI issued a second warning this week to alert US companies of ProLock ransomware operators stealing data from compromised networks before encrypting their victims’ systems.
SunCrypt Ransomware shuts down North Carolina school district
A school district in North Carolina has suffered a data breach after having unencrypted files stolen during an attack by the SunCrypt Ransomware operators, BleepingComputer has discovered.
That’s it for this week! Hope everyone has a nice weekend!
Also read: Computer Misuse Act Singapore: The Truth And Its Offenses