KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Over the past two weeks, it has been busy with ransomware news ranging from a gang shutting down and releasing a master decryption key to threat actors turning to Microsoft Exchange exploits to breach networks.
The biggest news is the Ragnarok ransomware operation shutting down and releasing a master decryptor on their site. Using the released keys, Emsisoft was able to create its own decryptor.
We have also seen ransomware gangs, such as LockFile and Conti, begin to use the recently disclosed Microsoft Exchange ProxyShell vulnerabilities.
The FBI and CISA have also been busy, releasing advisories warning of ransomware attacks over holiday weekends, gangs targeting food and agriculture organizations, information about the 1% group, and IOCs for the Hive Ransomware.
A threat actor released the complete source code for the Babuk Ransomware, allowing any wannabe threat actor to start their own ransomware operation. Unfortunately, this leak will lead to many threat actors worldwide creating their own Ransomware-as-a-Service.
Also Read: 5 ways on how to destroy documents securely to prevent data breach
Finally, leaked Conti training material and a Pysa data exfiltration script have given us insight into how ransomware gangs conduct their attacks and what data they are targeting.
Contributors and those who provided new ransomware information and stories this week include: @VK_Intel, @fwosar, @struppigel, @malwrhunterteam, @PolarToffee, @Ionut_Ilascu,
The FBI and CISA have also been busy, releasing advisories warning of ransomware attacks over holiday weekends, gangs targeting food and agriculture organizations, information about the 1% group, and IOCs for the Hive Ransomware.
A threat actor released the complete source code for the Babuk Ransomware, allowing any wannabe threat actor to start their own ransomware operation. Unfortunately, this leak will lead to many threat actors worldwide creating their own Ransomware-as-a-Service.
Finally, leaked Conti training material and a Pysa data exfiltration script have given us insight into how ransomware gangs conduct their attacks and what data they are targeting.
Contributors and those who provided new ransomware information and stories this week include: @VK_Intel, @fwosar, @struppigel, @malwrhunterteam, @PolarToffee, @Ionut_Ilascu, @BleepinComputer, @demonslay335, @LawrenceAbrams, @jorntvdw, @FourOctets, @DanielGallagher, @Seifreed, @serghei, @malwareforme, @vxunderground, @AltShiftPrtScn, @thepacketrat, @TalosSecurity, @GossiTheDog, @pcrisk, @fbgwls245, @ddd1ms, and @darktracer_int.
A new ransomware gang known as LockFile encrypts Windows domains after hacking into Microsoft Exchange servers using the recently disclosed ProxyShell vulnerabilities.
The Federal Bureau of Investigation (FBI) has shared info about a threat actor known as OnePercent Group that has been actively targeting US organizations in ransomware attacks since at least November 2020.
SAC Wireless, a US-based Nokia subsidiary, has disclosed a data breach following a ransomware attack where Conti operators were able to successfully breach its network, steal data, and encrypt systems.
PCRisk found a new STOP ransomware variant that appends the .orkf extension.
PCRisk found a new Dharma ransomware variant that appends the .dts extension.
A PowerShell script used by the Pysa ransomware operation gives us a sneak peek at the types of data they attempt to steal during a cyberattack.
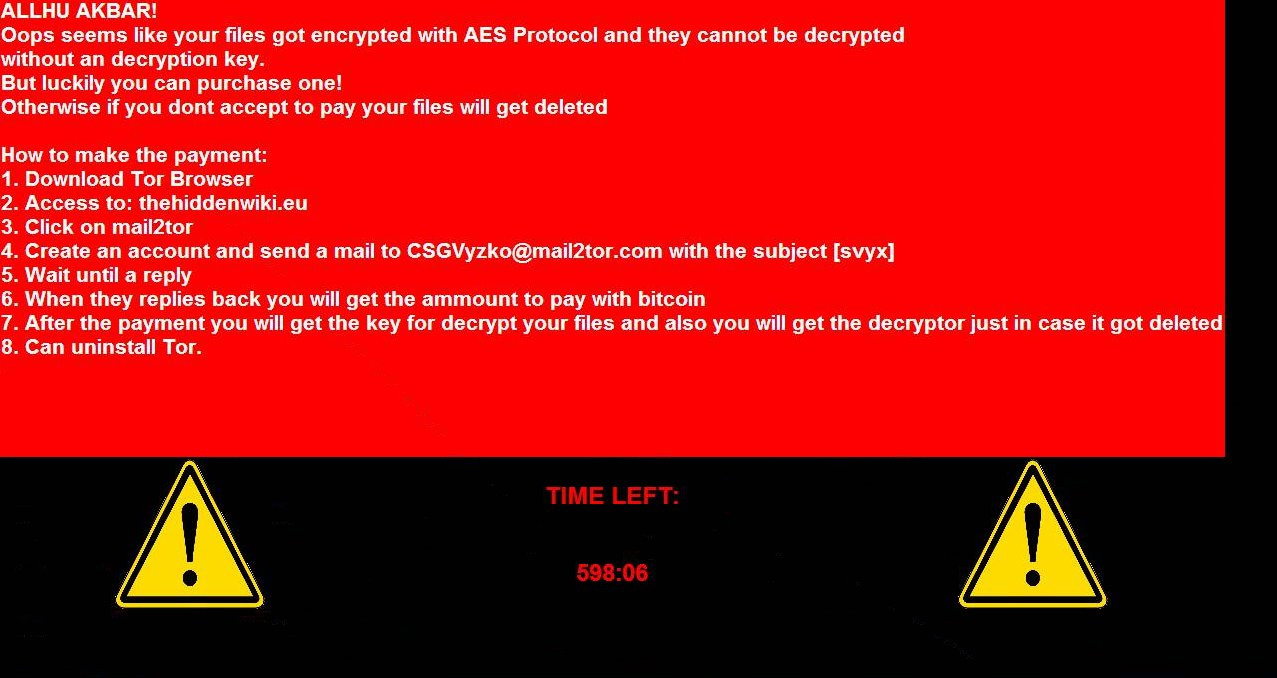
dnwls0719 found a BlackKingdom variant that appends the .svyx extension.
Ragnarok ransomware gang appears to have called it quits and released the master key that can decrypt files locked with their malware.
The Federal Bureau of Investigation (FBI) has released some technical details and indicators of compromise associated with Hive ransomware attacks.
PCRisk found new Dharma ransomware variants that appends the .6ix9and .TCYO extensions.
PCRisk found a new Phobos ransomware variant that appends the .PERDAK extension.
Also Read: 6 Ways to Protect Your Business From Employee Data Theft
The Boston Public Library (BPL) has disclosed today that its network was hit by a cyberattack on Wednesday, leading to a system-wide technical outage.
PCRisk found a new Dharma ransomware variant that appends the .RZA extension.
dnwls0719 found a new ransomware called HQ_52_42 that appends the .HQ_52_42 extension.
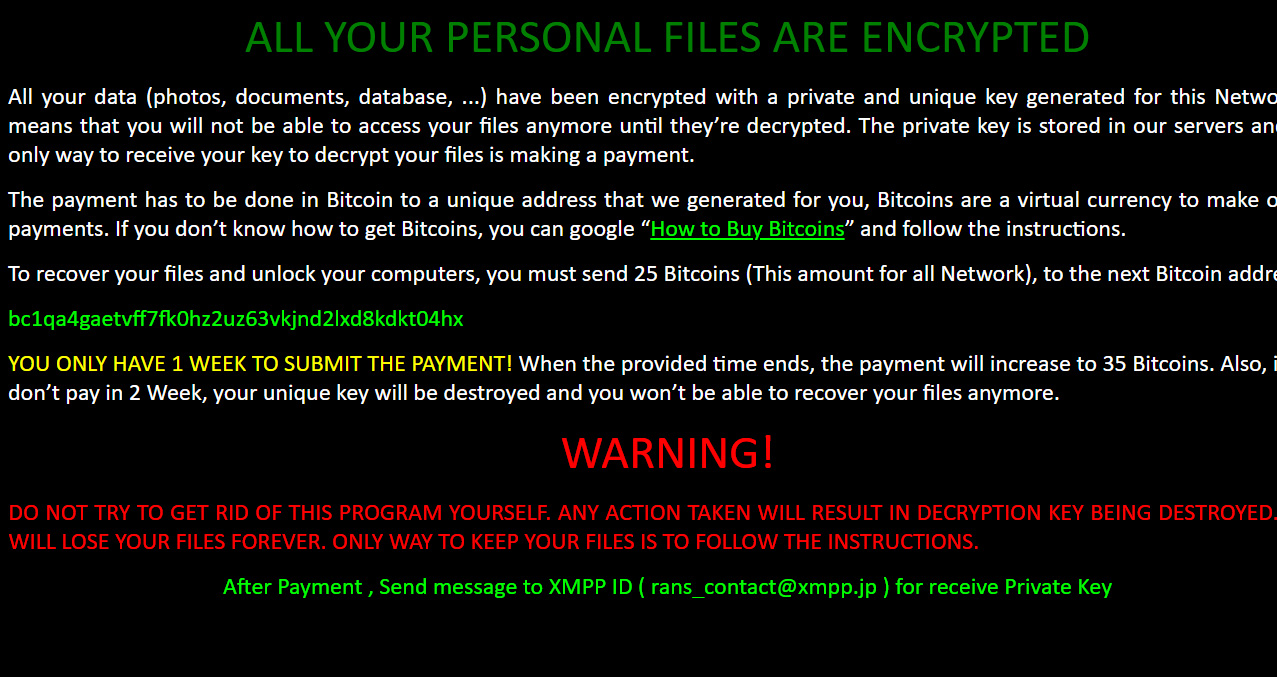
dnwls0719 found a new ransomware called SanwaiWare 2021 that appends the .sanwai extension.
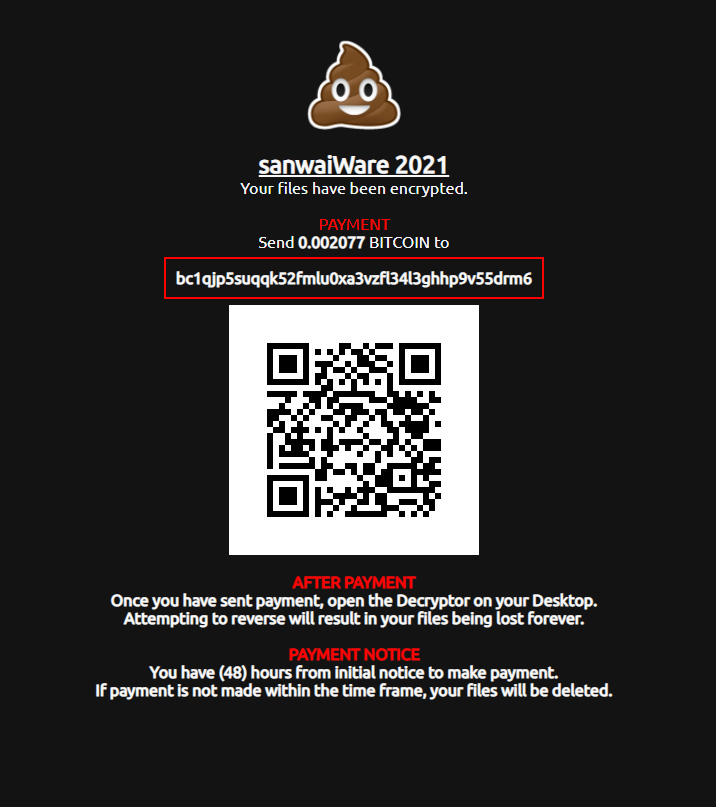
PCRisk found a new STOP ransomware variant that appends the .lqqw extension.
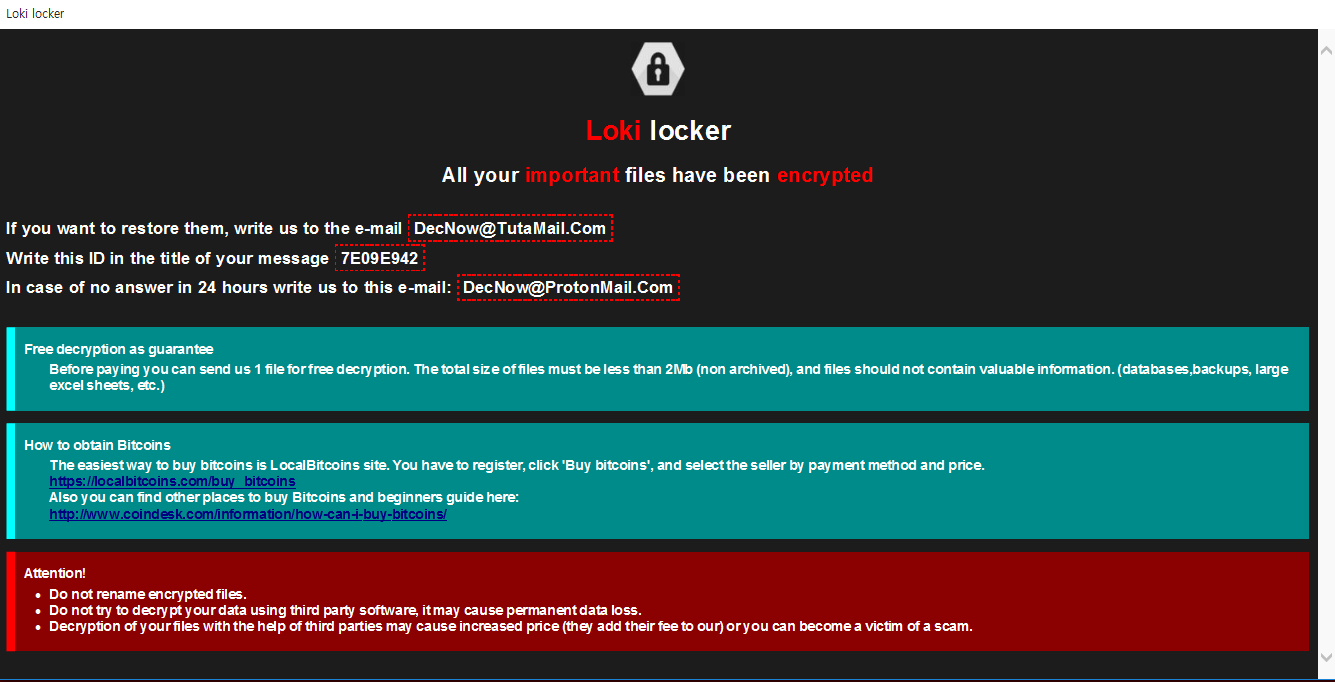
dnwls0719 found a new ransomware called Loki Locker that appends the .Loki extension.
The FBI and CISA urged organizations not to let down their defenses against ransomware attacks during weekends or holidays in a joint cybersecurity advisory issued earlier today.
Bangkok Airways, a major airline company in Thailand, confirmed it was the victim of a cyberattack earlier this month that compromised personal data of passengers.
In this post, we mentioned the fact of BlackMatter and Babuk using the same web server for sharing the leaked files.
Almost a month after a disgruntled Conti affiliate leaked the gang’s attack playbook, security researchers shared a translated variant that clarifies any misinterpretation caused by automated translation.
The FBI says ransomware gangs are actively targeting and disrupting the operations of organizations in the food and agriculture sector, causing financial loss and directly affecting the food supply chain.
The Conti ransomware gang is hacking into Microsoft Exchange servers and breaching corporate networks using recently disclosed ProxyShell vulnerability exploits.
A threat actor has leaked the complete source code for the Babuk ransomware on a Russian-speaking hacking forum.
DarkTracer found that all three ransomware groups are utilizing the same Tor data leak site. They are not believed to be affiliated, other than possible being part of the same cartel.
DarkTracer found that Astro Team, Mount Locker, and XING Locker are sharing the same Tor network infrastructure. Astro Team and MountLocker are believed to be affiliated with each other.
Dmitry Smilyanets noted that threat actors worldwide will likely launch their own ransomware operations based on the leaked Babuk ransomware source code.
PCRisk found a new STOP ransomware variant that appends the .efdc extension.