KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Ransomware continues to run rampant this week, with well-known organizations getting hit with massive ransomware attacks.
The biggest news this week is the Clop ransomware attack against Software AG, where the attackers are demanding a $23 million ransom.
This week, we also learned that a New Jersey hospital paid a 670K ransom and that the Springfield Public School district got hit with ransomware this week.
Get those RDP servers off the Internet, upgrade edge devices, and be careful of phishing emails. All are prime vectors used in ransomware attack.
Contributors and those who provided new ransomware information and stories this week include: @malwareforme, @FourOctets, @Seifreed, @serghei, @DanielGallagher, @LawrenceAbrams, @Ionut_Ilascu, @demonslay335, @VK_Intel, @jorntvdw, @struppigel, @malwrhunterteam, @PolarToffee, @fwosar, @BleepinComputer, @LabsSentinel, @JakubKroustek, @siri_urz, @MsftSecIntel, @CheckPointSW, @IBMSecurity, and @cyb3rops.
University Hospital New Jersey in Newark, New Jersey, paid a $670,000 ransomware demand this month to prevent the publishing of 240 GB of stolen data, including patient info.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
Jakub Kroustek found a new Dharma ransomware variant that appends the .FLYU extension to encrypted files.
A new ransomware vaccine program has been created that terminates processes that try to delete volume shadow copies using Microsoft’s vssadmin.exe program,
Karsten Hahn tweeted about a new Babax variant called Osno Stealer that includes a ransomware module that appends the .osnoed.
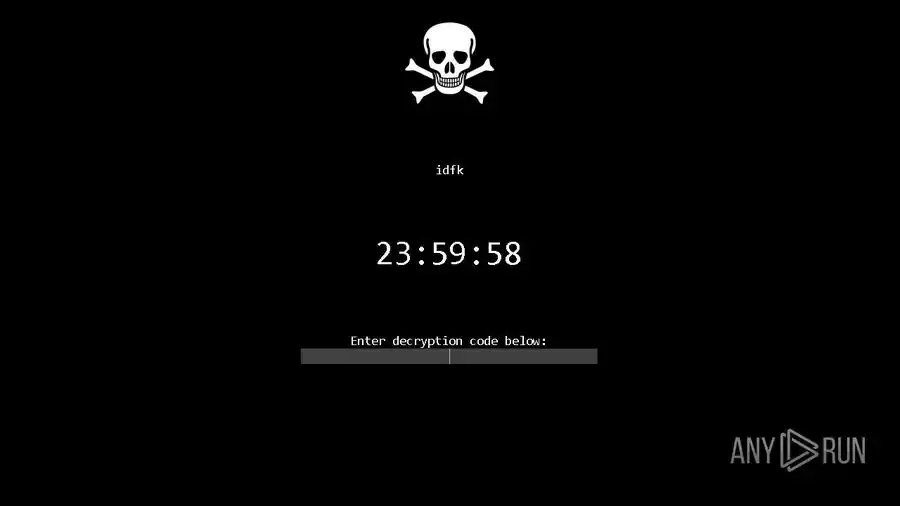
Michael Gillespie found a new STOP Djvu ransomware variant that appends the .moss extension to encrypted files.
Michael Gillespie a ransomware called EYECRY that is a customized version of the Petya ransomware/bootlocker.
Also Read: Contract for Service Template: 5 Important Sections
xXToffeeXx found a new ransomware dubbed SantaCrypt that appends the .$anta and drops a ransom note named HOW_TO_RECOVER_MY_FILES.TXT.
Malware researchers monitoring ransomware threats noticed a sharp increase in these attacks over the past months compared to the first six months of 2020.
FONIX Raas (Ransomware as a Service) is an offering that first came to attention in July of this year. It did not make much of a splash at the time, and even currently, we are only seeing small numbers of infections due to this ransomware family. However, RaaS that at first fly under the radar can quickly become rampant if defenders and security solutions remain unaware of them. Notably, FONIX varies somewhat from many other current RaaS offerings in that it employs four methods of encryption for each file and has an overly-complex post-infection engagement cycle. In this post, we dig a little deeper into these and other peculiarities of this new RaaS offering.
Michael Gillespie is looking for a new ransomware that appends the extension .CURATOR and drops a ransom note named !=HOW_TO_DECRYPT_FILES=!.txt.
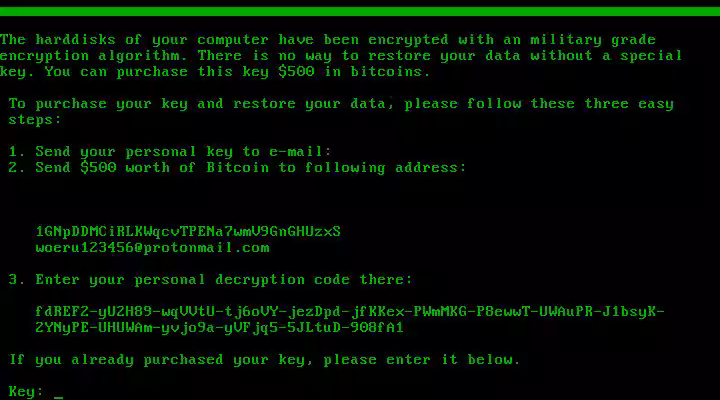
S!Ri found a new ransomware that appends .woodrat to encrypted files.
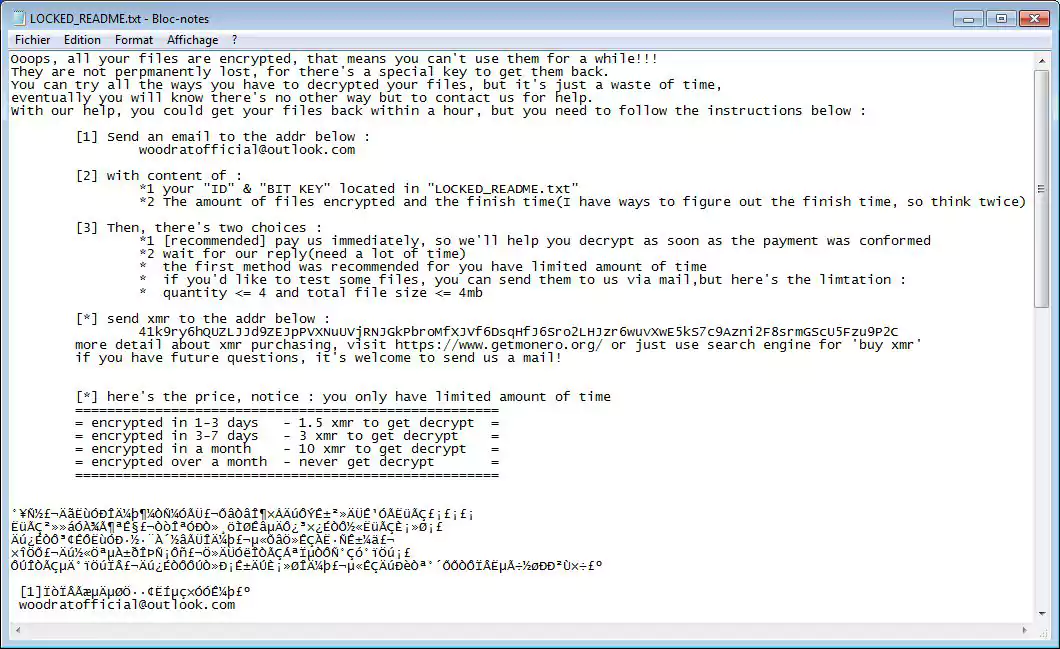
MalwareHunterTeam found a new Android ransomware called CyberSplitter that appends the .Dcry extension to encrypted files.
The Springfield Public Schools district in Massachusetts has become the victim of a ransomware attack that has caused the closure of schools while they investigate the cyberattack.
Microsoft is warning that cybercriminals have started to incorporate exploit code for the ZeroLogon vulnerability in their attacks. The alert comes after the company noticed ongoingattacks from cyber-espionage group MuddyWater (SeedWorm) in the second half of September.
The Clop ransomware gang hit the network of German enterprise software giant Software AG last Saturday, asking for a ransom of $23 million after stealing employee information and company documents.
Carnival Corporation, the world’s largest cruise line operator, has confirmed that the personal information of customers, employees, and ship crews was stolen during an August ransomware attack.
Jakub Kroustek found new Dharma ransomware variants that append the .gtsc or .dme extension to encrypted files.
S!Ri found a new in-development ransomware that appends .en extension to encrypted files.