KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Law enforcement continues to keep up the pressure on ransomware operations with infrastructure hacks and million-dollar rewards, leading to the shut down of criminal operations.
Due to this increased pressure by law enforcement, the BlackMatter (DarkSide) ransomware gang announced to affiliates that they were shutting down this week after members were missing.
BleepingComputer later discovered that BlackMatter began moving existing victims to LockBit ransomware’s infrastructure to continue extortion demands.
To keep pressure on the DarkSide gang and warn that rebranding to a new operation won’t stop law enforcement, the US Department of State announced a $10 million reward for identifying or locating key leaders in the organization. In addition, the US government is also offering $5 million for the arrest of any individuals participating in future attacks using DarkSide variants.
Also Read: 6 Simple Guides On PDPA Clause For Agreements Of Personal Data
The FBI also issued advisories this week warning that HelloKitty has added DDoS attacks to their arsenal, that ransomware gangs commonly conduct attacks “during time-sensitive financial events,” and that gangs are targeting tribal-owned businesses, including casinos.
Ransomware attacks we saw this week were against the UK Labour Party and the Newfoundland and Labrador health systems.
Contributors and those who provided new ransomware information and stories this week include: @serghei, @malwareforme, @LawrenceAbrams, @BleepinComputer, @fwosar, @DanielGallagher, @Ionut_Ilascu, @struppigel, @jorntvdw, @VK_Intel, @billtoulas, @malwrhunterteam, @FourOctets, @demonslay335, @PolarToffee, @Seifreed, @CofenseLabs, @TalosSecurity, @vxunderground, @pancak3lullz, @Fortinet, @GelosSnake, @nakashimae, @DDaltonBennett, @fbgwls245, @pcrisk, and @Amigo_A_.
The Chaos Ransomware gang encrypts gamers’ Windows devices through fake Minecraft alt lists promoted on gaming forums.
The U.S. Federal Bureau of Investigation (FBI) has sent out a flash alert warning private industry partners that the HelloKitty ransomware gang (aka FiveHands) has added distributed denial-of-service (DDoS) attacks to their arsenal of extortion tactics.
The BlackShadow hacking group attacked the Israeli hosting provider Cyberserve to steal client databases and disrupt the company’s services.
The Canadian province of Newfoundland and Labrador has suffered a cyberattack that has led to severe disruption to healthcare providers and hospitals.
Also Read: The Top 10 Primary GDPR Requirements PDF To Secure Business
dnwls0719 found a new Dharma ransomware variant that append the .MS extension to encrypted files.
PCrisk found new STOP ransomware variants that append the .cool and .palq extensions to encrypted files.
The Federal Bureau of Investigation (FBI) warns that ransomware gangs are targeting companies involved in “time-sensitive financial events” such as corporate mergers and acquisitions to make it easier to extort their victims.
The BlackMatter ransomware is allegedly shutting down its operation due to pressure from the authorities and recent law enforcement operations.
The U.K. Labour Party notified members that some of their information was impacted in a data breach after a ransomware attack hit a supplier managing the party’s data.
With the BlackMatter ransomware operation shutting down, existing affiliates are moving their victims to the competing LockBit ransomware site for continued extortion.
A major overseas ransomware group shut down last month after a pair of operations by U.S. Cyber Command and a foreign government targeting the criminals’ servers left its leaders too frightened of identification and arrest to stay in business, according to several U.S. officials familiar with the matter.
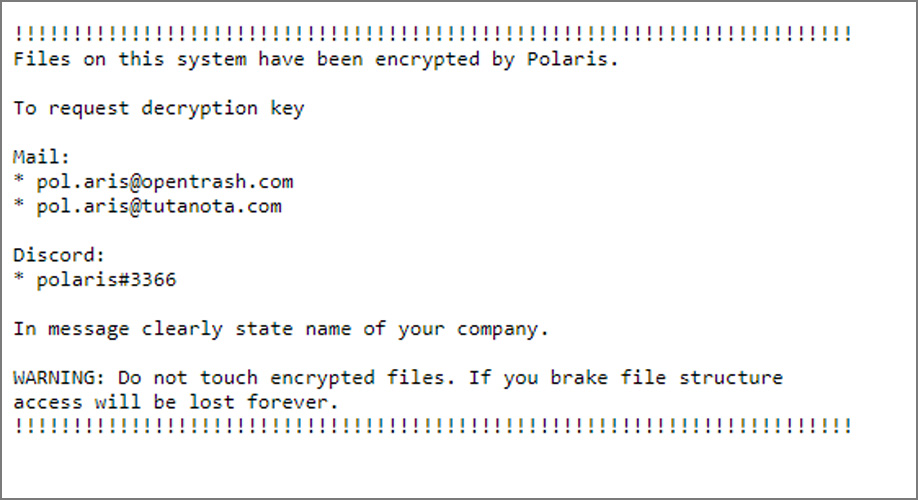
Amigo-A found a new Polaris ransomware that is targeting Linux and dropping ransom notes named WARNING.txt.
A new threat actor is hacking Microsoft Exchange servers and breaching corporate networks using the ProxyShell vulnerability to deploy the Babuk Ransomware.
A new phishing campaign pretending to be supply lists infects users with the MirCop ransomware that encrypts a target system in under fifteen minutes.
The US government is targeting the DarkSide ransomware and its rebrands with up to a $10,000,000 reward for information leading to the identification or arrest of members of the operation.
Details about the tools and tactics used by a ransomware affiliate group, now tracked as Lockean, have emerged today in a report from France’s Computer Emergency Response Team (CERT).
PCrisk found a new Dharma ransomware variant that append the .WORM extension to encrypted files.
PCrisk found new STOP ransomware variants that append the .stax and .irkf extensions to encrypted files.
dnwls0719 found a new Thanos ransomware variant that appends the .stepik extension.