KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







This week we saw two massive attacks that had a signifcant impact on the food supply industry, as well as a demonstration of Egregor’s annoying ransom note print bombs.
Last weekend, Latin American retail giant Cencosud suffered an attack by the Egregor ransomware gang that caused technical difficulties at numerous retail stores, including supermarkets and grocery stores. During this attack we also got a demonstration of Egregor’s annoying tactic of print bombing printers with ransom notes.
Cold storage warehouse operator Americold was also hit with a ransomware attack this weekend that caused significant food distribution problems for numerous supermarkets who utilize them in the USA. One food distribution logistics operator who was having trouble picking up food deliveries told BleepingComputer that this attack came at the worst time as they gear up for Thanksgiving.
Finally, the TrickBot gang has started spamming out a new lightweight reconnaissance tool called LightBot to collect information about a victim’s network before potentially deploying ransomware. Just one more thing to keep an eye out for as we come to the weekend.
Contributors and those who provided new ransomware information and stories this week include: @demonslay335, @malwareforme, @malwrhunterteam, @jorntvdw, @struppigel, @fwosar, @serghei, @PolarToffee, @LawrenceAbrams, @VK_Intel, @Seifreed, @FourOctets, @BleepinComputer, @DanielGallagher, @Ionut_Ilascu, @GroupIB_GIB, @Intel471Inc, @coveware, @juanbrodersen, @identidadrobada, @Kangxiaopao, @fbgwls245, @TalosSecurity, @0x4143, @JakubKroustek, @campuscodi, @siri_urz, and the @FBI.
Chilean-based multinational retail company Cencosud has suffered a cyberattack by the Egregor ransomware operation that impacts services at stores.
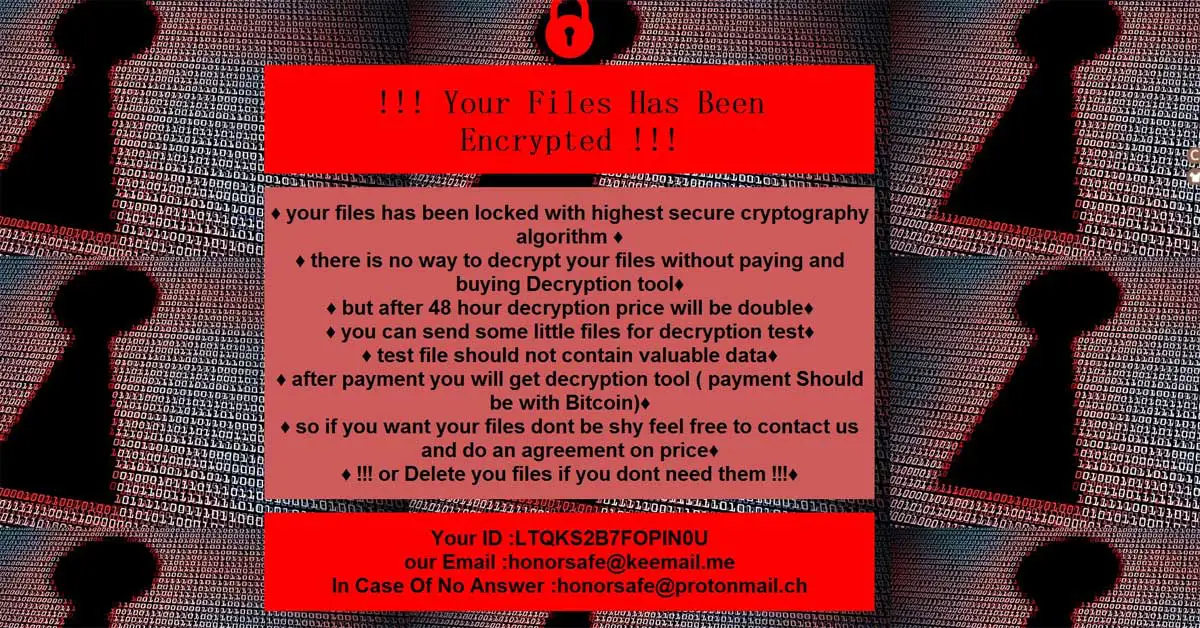
Michael Gillespie found a new STOP Djvu ransomware variant that appends the .vvoa extension.
dnwls0719 found a new HiddenTear variant that appends the .ZqVIkE extension and drops a ransom note named @[email protected].
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
Ransomware negotiation firm Coveware has placed the DarkSide operation on an internal restricted list after the threat actors announced plans to host infrastructure in Iran.
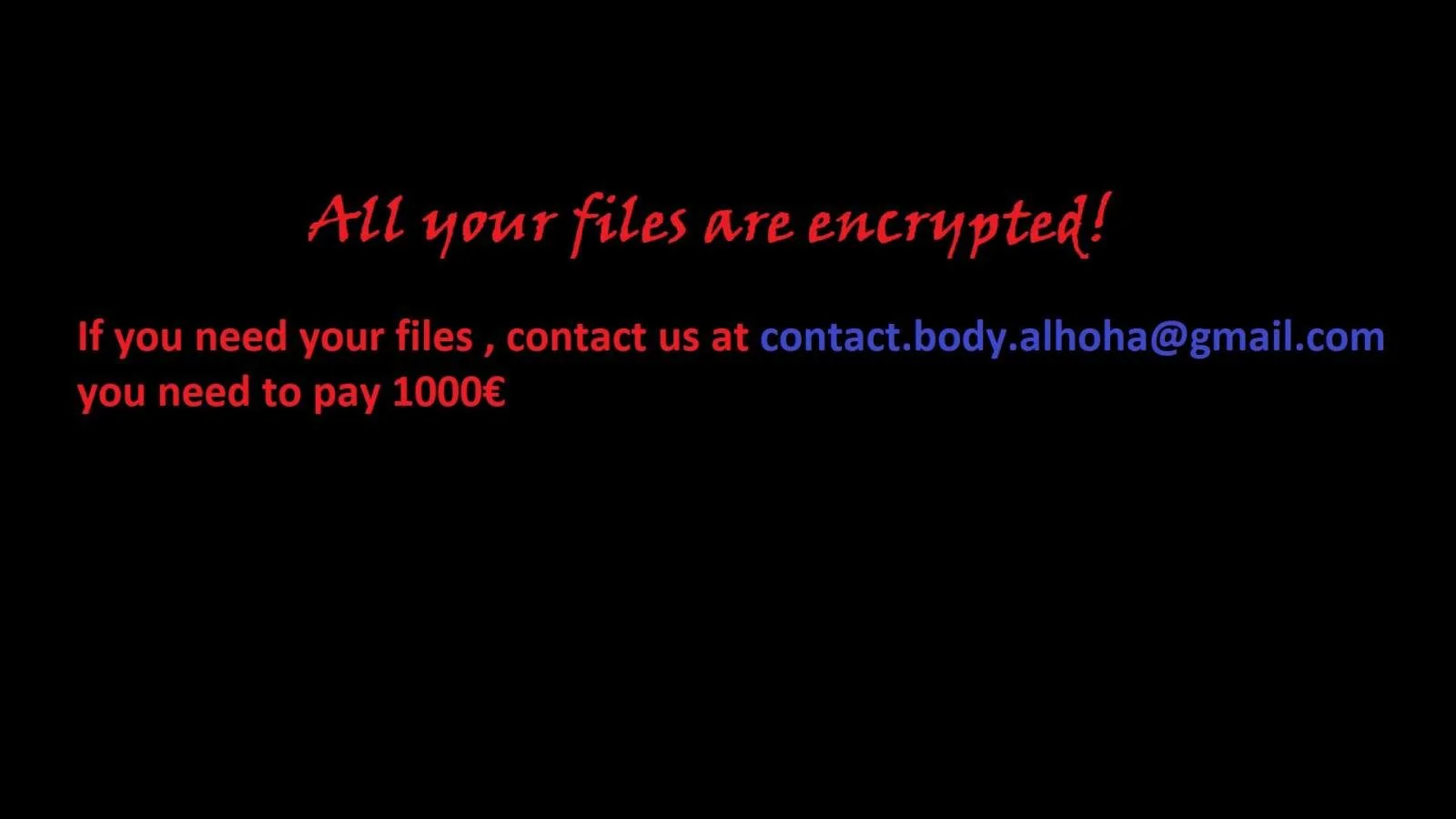
xiaopao found a new variant of the VoidCrypt Ransomware that appends the .honor extension.
Japanese game giant Capcom has announced a data breach after confirming that attackers stole sensitive customer and employee information during a recent ransomware attack.
Ransomware-as-a-service (RaaS) crews are actively looking for affiliates to split profits obtained in outsourced ransomware attacks targeting high profile public and private organizations.
Cold storage giant Americold is currently dealing with a cyberattack impacting their operations, including phone systems, email, inventory management, and order fulfillment.
Michael Gillespie found a new STOP Djvu ransomware variant that appends the .epor extension.
Michael Gillespie spotted a new Flamingo Ransomware variant that appends the .LIZARD extension and drops a ransom note named #READ ME.TXT.
Michael Gillespie spotted a new unidentified ransomware that appends the .MXX extension and drops a ransom note named How To Recover Your Files!!!!.txt.
xXToffeeXx spotted a new Phobos ransomware variant that appends the .ELDAOLSA extension.
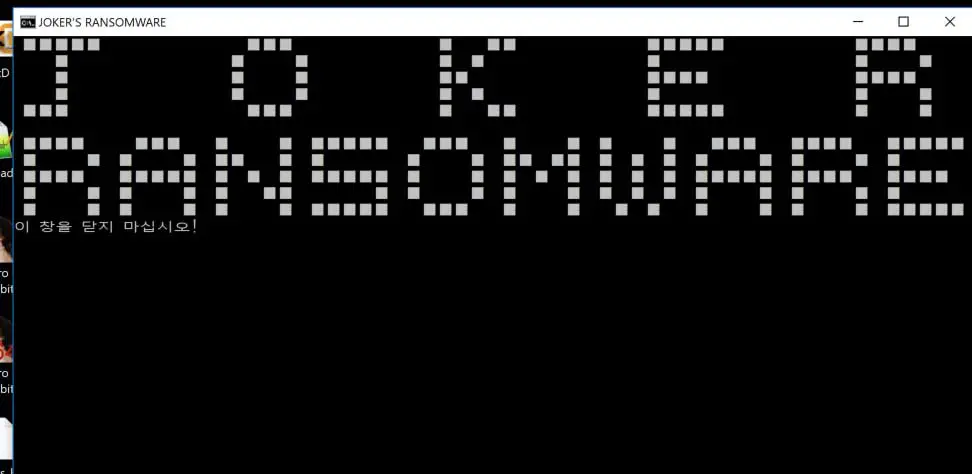
@0x4143 found the new Joker’s Ransomware that appends the .joker extension and drops a ransom note named POWER-JOKER-PASSWORD.txt.
Jakub Kroustek found a bunch of Dharma Ransomware variants that append the .dex, .sss, .zimba, and .help extensions.
The Nibiru ransomware is a .NET-based malware family. It traverses directories in the local disks, encrypts files with Rijndael-256 and gives them a .Nibiru extension. Rijndael-256 is a secure encryption algorithm. However, Nibiru uses a hard-coded string “Nibiru” to compute the 32-byte key and 16-byte IV values. The decryptor program leverages this weakness to decrypt files encrypted by this variant.
xiaopao found a new Matrix Ransomware variant that appends the .TG33 extension.
xiaopao found a new HiddenTear ransomware variant that appends the .r2block extension.

xiaopao found a new Dharma Ransomware variant that appends the .ZIN extension.
Siri found a new ransomware that appends .pulpit extension.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
Managed web hosting provider Managed.com has taken their servers and web hosting systems offline as they struggle to recover from a weekend REvil ransomware attack.
The Egregor ransomware uses a novel approach to get a victim’s attention after an attack – shoot ransom notes from all available printers.
MalwareHunterTeam found a new ransomware pretending to be a Blockchain Generator that appends the .lola extension and drops a ransom note named Please_Read.txt.
The Mount Locker ransomware operation is gearing up for the tax season by specifically targeting TurboTax returns for encryption.
Michael Gillespie found a new STOP Djvu ransomware variant that appends the .sglh extension.
MalwareHunterTeam found a new ransomware that appends the .REDROMAN and drops ransom notes names RR_README.html, OPENTHIS.html, and README.html.
The Qbot banking trojan has dropped the ProLock ransomware in favor of the Egregor ransomware who burst into activity in September.
The notorious TrickBot has gang has released a new lightweight reconnaissance tool used to scope out an infected victim’s network for high-value targets.
The U.S. Federal Bureau of Investigation (FBI) Cyber Division has warned private industry partners of increased Ragnar Locker ransomware activity following a confirmed attack from April 2020.
Michael Gillespie spotted a new unidentified ransomware that appends the .esexz and drops a ransom note named readme.txt.
xiaopao found a new Dharma Ransomware variant that appends the .SWP extension.
This article focuses on the known malware strains that have been used over the past two years to install ransomware.
During the lock down of the past two weeks, we were hit by an IT failure caused by a computer virus (ransomware). As a result, we are difficult to reach and we have to deal with systems that do not work.
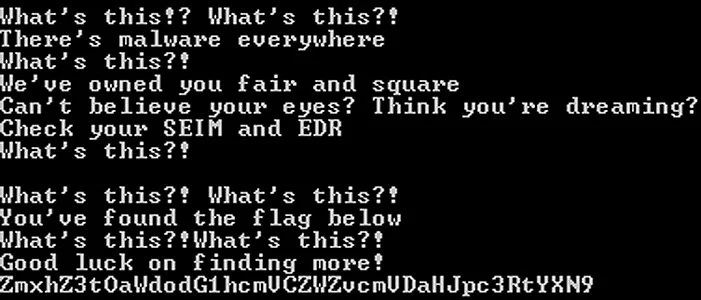
MalwareHunterTeam found a ransomware with an interesting hidden message.
Michael Gillespie found that a hospital was hit with a custom ransomware.
Jakub Kroustek found a bunch of Dharma Ransomware variants that append the .cvc extension.