KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







While last week was full of arrests and law enforcement actions, this week has been much quieter, with mostly new research released.
Security firms released reports on the types of cryptomixers used by ransomware gangs, a detailed report on Conti, and how Russian ransomware gangs are starting to work with Chinese hackers.
Today, US regulators also ordered banks to report cyber attacks within 36 hours if they impact their operations, the ability to deliver banking products and services, or the US financial sector’s stability.
Finally, a Tor negotiation site for the Conti ransomware gang was taken down, likely due to the release of its IP address in the PRODAFT report.
Also Read: The Top 4W’s of Ethical Hacking
Contributors and those who provided new ransomware information and stories this week include: @DanielGallagher, @fwosar, @struppigel, @FourOctets, @malwrhunterteam, @billtoulas, @Seifreed, @Ionut_Ilascu, @serghei, @jorntvdw, @PolarToffee, @demonslay335, @VK_Intel, @LawrenceAbrams, @malwareforme, @BleepinComputer, @intel_bo7, @_aftrdrk, @thepacketrat, @SophosLabs, @FlashpointIntel, @sucurisecurity, @Intel471Inc, @_CPResearch_, @BrettCallow, @emsisoft, @PRODAFT, @joetidy, @RepMaloney, @siri_urz, @fbgwls245, @pcrisk, @Amigo_A_, and @AdvIntel.
dnwls0719 found a new ransomware that appends the .dst extension and expects users to use IRC over Tor to negotiate.
The US Department of Education and Department of Homeland Security (DHS) were urged this week to more aggressively strengthen cybersecurity protections at K-12 schools across the nation to keep up with a massive wave of attacks.
Amigo-A found a new ransomware in our forums called RansomNow that drops the HELP – README TO UNLOCK FILES.txt ransom note and does not append a new extension.
A new hacker group named Moses Staff has recently claimed responsibility for numerous attacks against Israeli entities, which appear politically motivated as they do not make any ransom payment demands.
PCrisk found a new STOP ransomware variant that appends the .futm extension.
Cryptomixers have always been at the epicenter of cybercrime activity, allowing hackers to “clean” cryptocurrency stolen from victims and making it hard for law enforcement to track them.
Also Read: What is Social Engineering and How Does it Work?
A new wave of attacks starting late last week has hacked close to 300 WordPress sites to display fake encryption notices, trying to trick the site owners into paying 0.1 bitcoin for restoration.
Many of the people on the FBI’s cyber most wanted list are Russian. While some allegedly work for the government earning a normal salary, others are accused of making a fortune from ransomware attacks and online theft. If they left Russia they’d be arrested – but at home they appear to be given free rein.
Today, Carolyn B. Maloney, Chairwoman of the Committee on Oversight and Reform, released a supplemental memo providing new insights into how the high-profile ransomware attacks on CNA Financial Corporation (CNA), Colonial Pipeline Company (Colonial), and JBS Foods USA (JBS) unfolded, and how legislation and policies responses may be developed to counter the threat of ransomware.
dnwls0719 found a new ransomware that appends the .chichi extension.
PCrisk found a new STOP ransomware variant that appends the .utjg extension.
?There’s some unusual activity brewing on Russian-speaking cybercrime forums, where hackers appear to be reaching out to Chinese counterparts for collaboration
PRODAFT Threat Intelligence (PTI) Team has obtained valuable insights on theinner workings of the Conti ransomware group. The PTI team accessed Conti’s infrastructure and identified the real IP addresses of the servers in question. This report provides unprecedented detail into the way the Conti ransomware gang works, how they select their targets, how many targets they’ve breached, and more.
A new ransomware group called Memento takes the unusual approach of locking files inside password-protected archives after their encryption method kept being detected by security software.
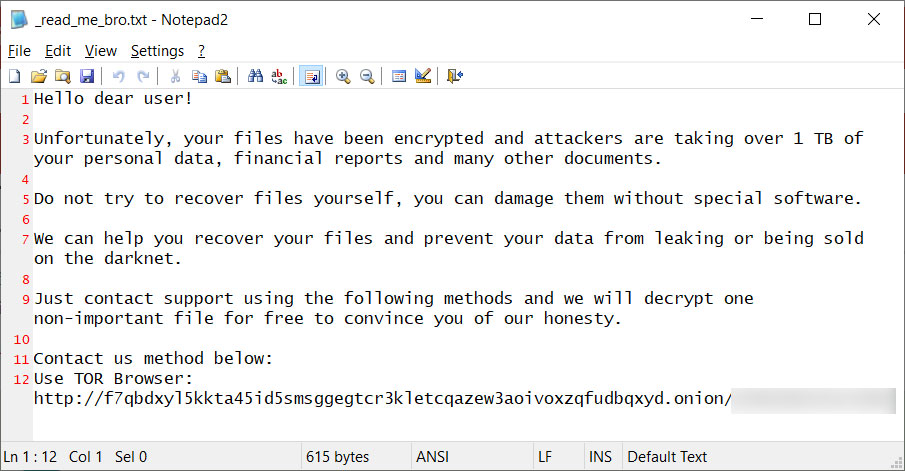
S!Ri found a new HelloKitty ransomware variant that appends the .boombye extension and drops a ransom note named _read_me_bro.txt.
US federal bank regulatory agencies have approved a new rule ordering banks to notify their primary federal regulators of significant computer-security incidents within 36 hours.
The Emotet botnet is back by popular demand, resurrected by its former operator, who was convinced by members of the Conti ransomware gang.
The Conti Tor negotiation sites were shut down for approximately 24 hours after the Prodaft report revealed its IP address, and law enforcement reportedly took the server offline.