KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







While ransomware attacks continued throughout the week, for the most part, it has been quieter than usual, with only a few new variants released.
The biggest news was the attack on health care giant Scripps Health whose operations were severely impacted by a ransomware attack.
We also saw a new ransomware called N3TW0RM targeting Israeli companies using an interesting client-server encryption method.
Finally, we learned that Cuba Ransomware is now partnered with Hancitor to compromise and encrypt corporate networks more quickly.
Contributors and those who provided new ransomware information and stories this week include: @jorntvdw, @Ionut_Ilascu, @malwareforme, @LawrenceAbrams, @PolarToffee, @serghei, @demonslay335, @DanielGallagher, @malwrhunterteam, @FourOctets, @struppigel, @VK_Intel, @fwosar, @BleepinComputer, @Seifreed, @Intel_by_KELA, @AndreGironda, @GroupIB_GIB, @SophosLabs, @AltShiftPrtScn, @M0teki, @fbgwls245, @pcrisk, @chum1ng0, @PogoWasRight, @3xp0rtblog, @ProferoSec, @SecurityJoes, @cPeterr, and @y_advintel.
Nonprofit health care provider Scripps Health in San Diego is currently dealing with a ransomware attack that forced the organization to suspend user access to its online portal and switch to alternative methods for patient care operations.
A new ransomware gang known as ‘N3TW0RM’ is targeting Israeli companies in a wave of cyberattacks starting last week.
Also Read: How To Comply With PDPA: A Checklist For Businesses
MalwareHunterTeam found a new Nitro Ransomware variant calling itself ‘ArchAngel Ransomware.’
Yelisey Boguslavskiy discovered that a new Galaxy Ransomware operation was getting ready to launch and would be stealing data from victims.
dnwls0719 found the new Henry Ransomware that appends the .henry217 extension.
dnwls0719 found a WastedLocker variant that appends the .saverswasted extension.
3xp0rt noticed that a new Toxin Ransomware was being promoted on hacking forums.May 5th 2021
Michael Gillespie has found a new STOP Ransomware variant that appends the .rejg extension.
At the end of 2020, our team, made up of SecurityJoes and Profero incident responders, led an investigation into a complex attack in which hundreds of machines were encrypted, knocking the victim company offline completely. The threat actors behind the attack deployed the Cuba ransomware across the corporate network, using a mixture of PowerShell scripts, SystemBC, and Cobalt Strike to propagate it. Cuba Ransomware utilizes the symmetric ChaCha20 algorithm for encrypting files, and the asymmetric RSA algorithm for encrypting key information
“If we receive €200 worth of Bitcoin within 24 hours, your information will be permanently deleted from our servers,” the email said in Finnish. If Jere missed the first deadline, he’d have another 48 hours to fork over €500, or about $600. After that, “your information will be published for all to see.”
A student’s attempt to pirate an expensive data visualization software led to a full-blown Ryuk ransomware attack at a European biomolecular research institute.
This is my report for one of the latest Windows samples of Darkside Ransomware v1.8.6.2!
Cybercriminals are embracing data-theft extortion by creating dark web marketplaces that exist solely to sell stolen data.
The Cuba Ransomware gang has teamed up with the spam operators of the Hancitor malware to gain easier access to compromised corporate networks.
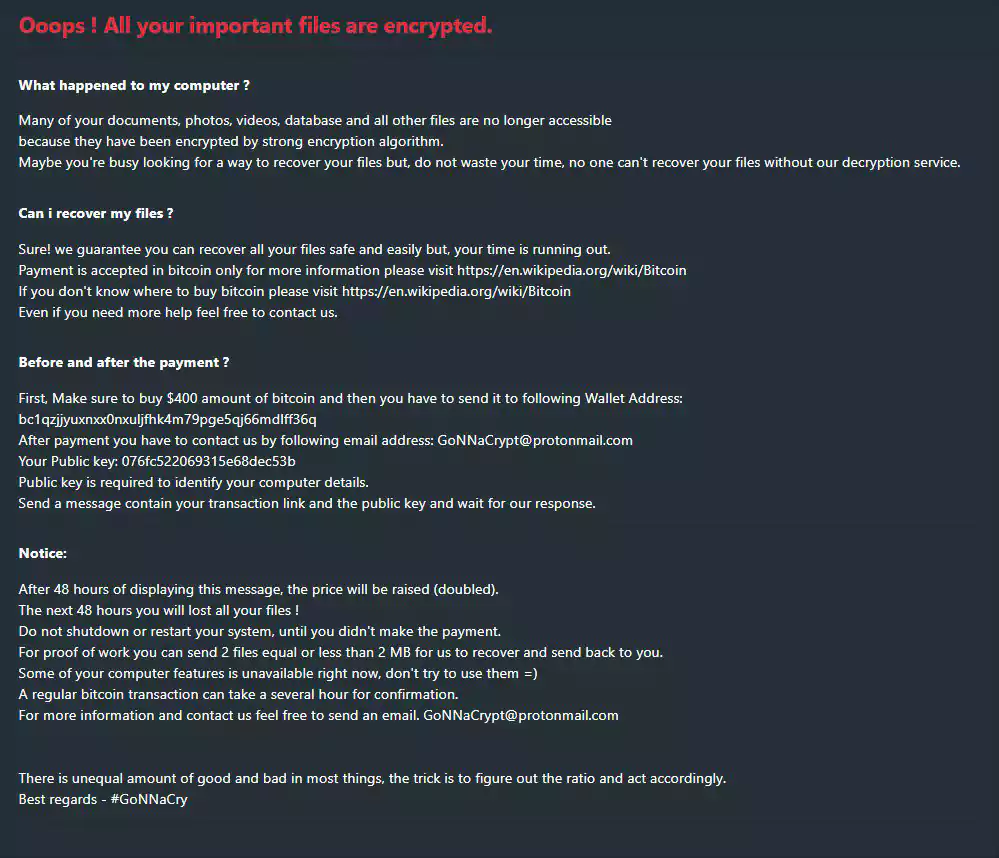
dnwls0719 found a ransomware that appends the .GoNNaCry extension.
In an apparent industry first, the global insurance company AXA said Thursday it will stop writing cyber-insurance policies in France that reimburse customers for extortion payments made to ransomware criminals.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing