KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






This week we have seen ransomware attacks targeting online service providers and MSPs to not only encrypt the victim but also cause significant outages for their customers.
HR and payroll platform PrismHR suffered a ransomware attack this weekend that caused an outage for PEOs and their clients that utilize the system. We also saw CompuCom, a large US MSP, get hit with a DarkSide ransomware attack that led to significant outages for most of their customers.
Clop Ransomware continues to publish the stolen data of victims whose data was stolen from breached Accellion FTA devices in December. Unfortunately, due to the number of organizations that used this service, we will likely continue seeing Accellion-related breaches announced.
Finally, Universal Health Services, which suffered a massive Ryuk ransomware attack in September 2020, reported that the cyberattacks had an estimated cost of $67 million.
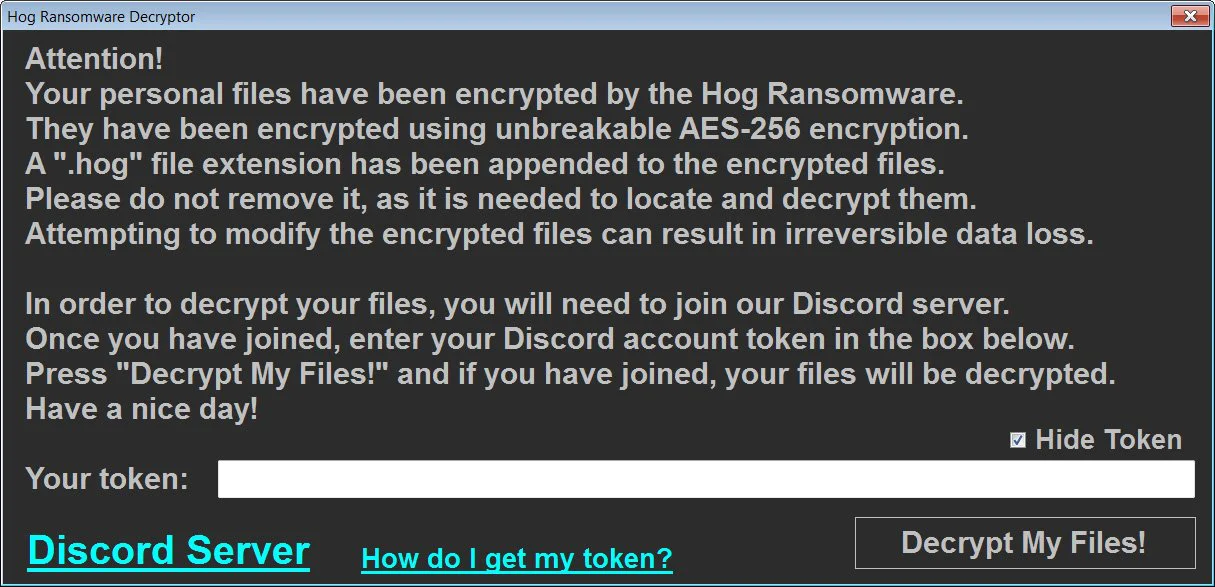
As for new ransomware, we continue to see new variants released and new in-development threats, such as a strange one that only decrypts victims if they join the threat actor’s Discord server.
Contributors and those who provided new ransomware information and stories this week include: @PolarToffee, @VK_Intel, @malwareforme, @Seifreed, @jorntvdw, @fwosar, @LawrenceAbrams, @FourOctets, @BleepinComputer, @DanielGallagher, @demonslay335, @struppigel, @malwrhunterteam, @serghei, @Ionut_Ilascu, @GroupIB, @Sophos, @kjkwak12, @JakubKroustek, @siri_urz, @Kangxiaopao, @Amigo_A_, @petrovic082, @IntezerLabs, @emsisoft, and @BrettCallow.
Also Read: Limiting Location Data Exposure: 8 Best Practices
The delivery system for the Gootkit information stealer has evolved into a complex and stealthy framework, which earned it the name Gootloader, and is now pushing a wider variety of malware via hacked WordPress sites and malicious SEO techniques for Google results.
Universal Health Services (UHS) said that the Ryuk ransomware attack it suffered during September 2020 had an estimated impact of $67 million.
The transport system for the Australian state of New South Wales has suffered a data breach after the Clop ransomware exploited a vulnerability to steal files.
Jakub Kroustek found new Dharma ransomware variants that appends the .oral and .urs extension to encrypted files.
Michael Gillespie found a new STOP ransomware variant that appends the .ribd extension to encrypted files.
Leading payroll company PrismHR is suffering a massive outage after suffering a cyberattack this weekend that looks like a ransomware attack from conversations with customers.
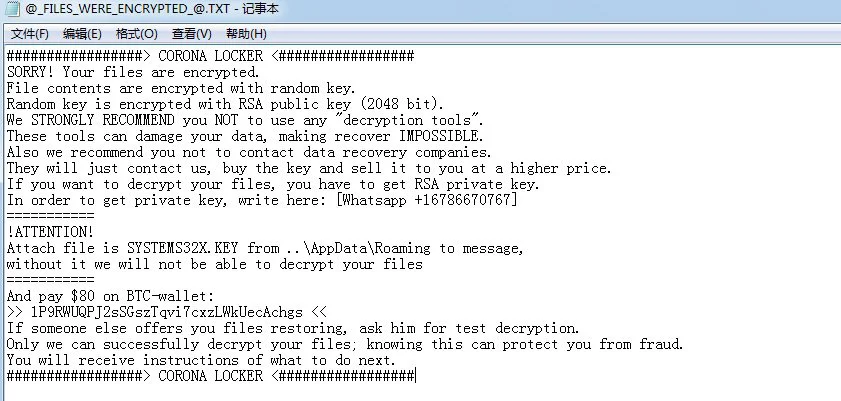
xiaopao found a new variant of the Aurora ransomware that calls itself ‘Corona Locker’ and appends the .systems32x extension.
Petrovic found a new Makop ransomware variant that appends the .vassago extension to encrypted files.
This report uses both dark web research and malware analysis to investigate the connection between the affiliate ransomware service known as SunCrypt and the QNAPCrypt ransomware, the latter of which was used against QNAP and Synology devices back in 2019. While the two ransomware are operated by distinct different threat actors on the dark web, there are strong technical connections in code reuse and techniques, linking the two ransomware to the same author. Just because a malware is a derivative of another malware does not mean it will be deployed in exactly the same way. A new operator may use different targets, tactics, techniques and procedures (TTPs), which can include new evasion techniques. Defenders must remain vigilant.
S!ri found a new ransomware that appends the .RansomTrojanLock extension to encrypted files.
S!ri found a new ransomware that we will let the screenshot speak for itself.
xiaopao found a new ransomware that appends the .IQ_IQ and drops a ransom note named HOW_TO_RECOVERY_FILES.txt.
Also Read: 10 Practical Benefits of Managed IT Services
Emsisoft has updated their Aurora decryptor to support the .systems32x extension.
US managed service provider CompuCom has suffered a DarkSide ransomware attack leading to service outages and customers disconnecting from the MSP’s network to prevent the spread of malware.
An analysis from global cybersecurity company Group-IB reveals that ransomware attacks more than doubled last year and increased in both scale and sophistication.
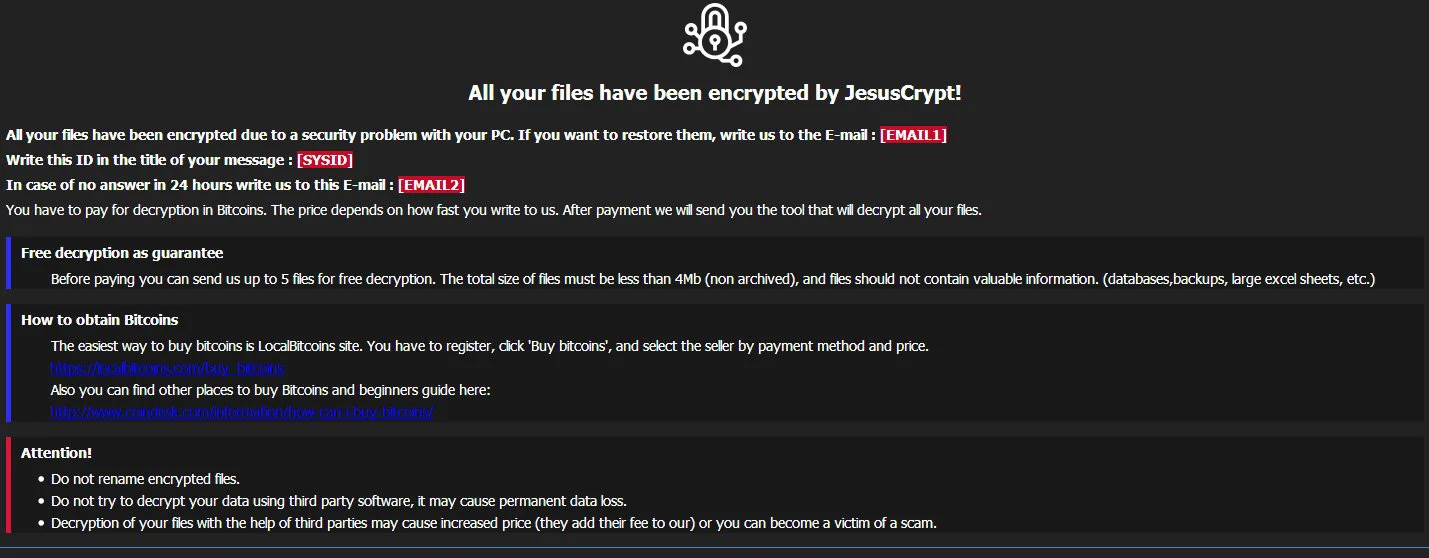
MalwareHunterTeam found a new in-development ransomware called JesusCrypt.
A new ransomware called ‘Hog’ encrypts users’ devices and only decrypts them if they join the developer’s Discord server.