KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







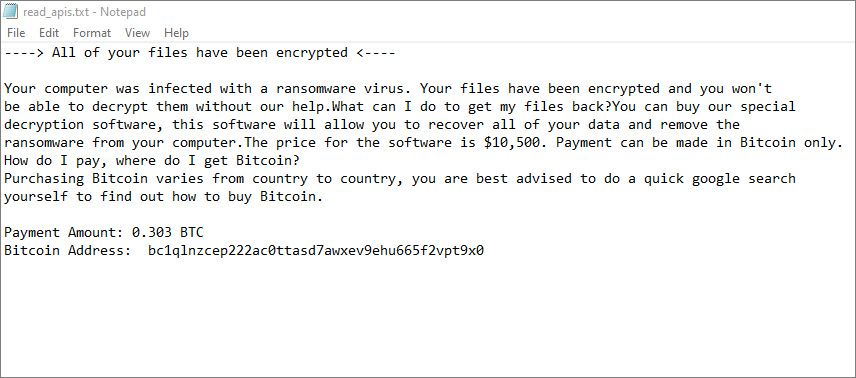
It has been relatively quiet this week, with few attacks revealed and few new ransomware variants released. However, some interesting information came out that we have summarized below.
Last week, a law enforcement operation arrestest numerous Clop Ransomware gang members, assisted by the Binance cryptocurrency exchange which helped track the threat actors performing money laundering for the Clop ransomware.
However, this did not seem to stop the ransomware gang for long as they continued to release the data of new victims this week.
The City of Tulsa also reported a data breach this week after the Conti ransomware gang began leaking stolen police citations online on their data leak site.
This week’s most significant attack was against Brazilian medical diagnostics giant Grupo Fleury who was hit with an REvil ransomware attack.
Contributors and those who provided new ransomware information and stories this week include: @malwrhunterteam, @demonslay335, @BleepinComputer, @FourOctets, @jorntvdw, @fwosar, @DanielGallagher, @VK_Intel, @Ionut_Ilascu, @LawrenceAbrams, @Seifreed, @serghei, @malwareforme, @PolarToffee, @struppigel, @GelosSnake, @ProferoSec, @SecurityJoes, @RansomAlert, @JakubKroustek, @GrujaRS, @fbgwls245, @coveware, @pcrisk, @Amigo_A_, @BlackBerry, and @symantec.
GrujaRS found a wiper that pretends to be the APIS ransomware.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
Amigo-A found a new ransomware called 0XXX that is encrypted Western Digital NAS devices and appending the .0xxx extension and dropping a ransom note named !0XXX_DECRYPTION_README.TXT.
The Marketo data theft marketplace is applying maximum pressure on victims by emailing their competitors and offering sample packs of the stolen data.
The Ragnar Locker ransomware gang have published download links for more than 700GB of archived data stolen from Taiwanese memory and storage chip maker ADATA.
A ransomware targeting an Israeli company has led researchers to track a portion of a ransom payment to a website promoting sensual massages.
Brazilian medical diagnostic company Grupo Fleury has suffered a ransomware attack that has disrupted business operations after the company took its systems offline.
dnwls0719 found a new variant of the Rapid ransomware that appends the .snoopdog extension.
The Clop ransomware operation is back in business after recent arrests and has begun listing new victims on their data leak site again.
The City of Tulsa, Oklahoma, is warning residents that their personal data may have been exposed after a ransomware gang published police citations online.
The PYSA ransomware gang has been using a remote access Trojan (RAT) dubbed ChaChi to backdoor the systems of healthcare and education organizations and steal data that later gets leveraged in double extortion ransom schemes.
Jakub Kroustek found new Dharma Ransomware variants that append the .nmc or .ZEUS extension to encrypted files.
Symantec has found evidence that an increasing number of ransomware attackers are using virtual machines (VMs) in order to run their ransomware payloads on compromised computers. The motivation behind the tactic is stealth. In order to avoid raising suspicions or triggering antivirus software, the ransomware payload will “hide” within a VM while encrypting files on the host computer.
Cryptocurrency exchange service Binance played an important part in the recent arrests of Clop ransomware group members, helping law enforcement in their effort to identify, and ultimately detain the suspects.
Luckily, some threat actors are more forthcoming. What follows are several case studies from real ransomware negotiations wherein the threat actor provided granular details on the full attack lifecycle, including usernames and passwords of compromised accounts and specific CVE’s leveraged to gain entry. Please note that these reports have not been edited or spell checked and that we redacted identifying information. Additionally, the tactics described by the threat actors herein were validated following thorough forensic investigation.
Also Read: Data Protection Officer Singapore | 10 FAQs
PCrisk found a new STOP ransomware variant that appends the .ddsg extension.
Amigo-A found the new Spyro Ransomware that appends the .Spyro extension and drops the Decrypt-info.txt ransom note.