KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







It has been quite the week when it comes to ransomware, with ransoms being paid, ransoms being taken back, and a ransomware gang shutting down.
This week’s biggest news was the FBI announcing that they were able to recover the majority of the $4.4 million ransom payment paid by Colonial Pipeline. It is not entirely clear how they obtained the private key for the cryptocurrency wallet, but it is believed DarkSide stored it on a seized server.
We also learned that JBS paid $11 million to the REvil ransomware operation to retrieve a decryptor and prevent stolen files from being leaked.
In a bit of good news, the Avaddon ransomware operation shut down and released the decryption keys of close to 3,000 victims to BleepingComputer. Using these, cybersecurity firm Emsisoft was able to release a free decryptor.
Finally, news broke this week that memory maker ADATA and food services supplier Edward Don suffered ransomware attacks.
Contributors and those who provided new ransomware information and stories this week include: @Ionut_Ilascu, @demonslay335, @FourOctets, @Seifreed, @fwosar, @jorntvdw, @BleepinComputer, @struppigel, @malwrhunterteam, @PolarToffee, @serghei, @DanielGallagher, @LawrenceAbrams, @VK_Intel, @malwareforme, @jonallendc, @kevincollier, @RobertScammell, @KimZetter, @RakeshKrish12, @fbgwls245, @Jirehlov, @SecurityJoes, @Kangxiaopao, and @GrujaRS.
dnwls0719 found a new ransomware named BigLock that appends the .nermer extension and drops a ransom note named PROTECT_INFO.TXT.

The new PayloadBIN ransomware has been attributed to the Evil Corp cybercrime gang, rebranding to evade sanctions imposed by the US Treasury Department’s Office of Foreign Assets Control (OFAC).
Jirehlov Solace found a new Findnotefile ransomware variant that appends the .reddot extension.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
Michael Gillespie is looking for a ransomware that appends the .ramsome.encrypt(rsw).nat extension and drops a note named readme-instructions.txt. The ransomware turns files into password-protected RAR archives.
The US Department of Justice has recovered the majority of the $4.4 million ransom payment paid by Colonial Pipeline to the DarkSide ransomware operation.
Japanese multinational conglomerate Fujifilm said it has refused to pay a ransom demand to the cyber gang that attacked its network in Japan last week and is instead relying on backups to restore operations.
Taiwan-based leading memory and storage manufacturer ADATA says that a ransomware attack forced it to take systems offline after hitting its network in late May.
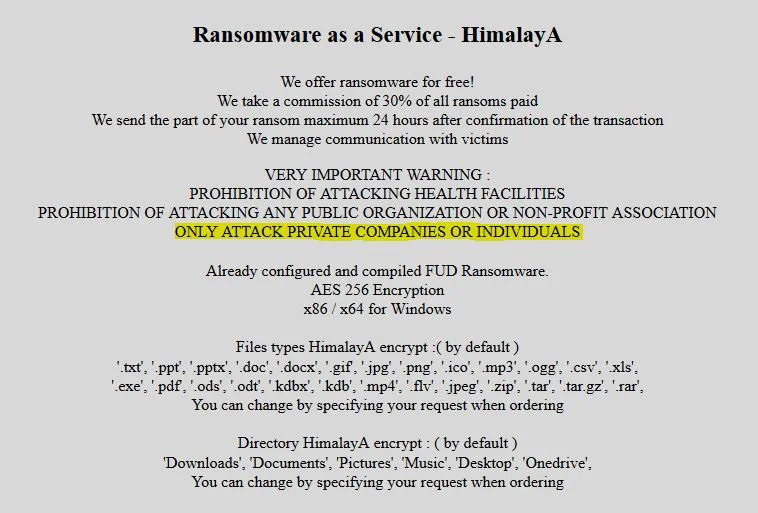
RAKESH KRISHNAN found a new RaaS named HimalayA advertised on the darkweb.
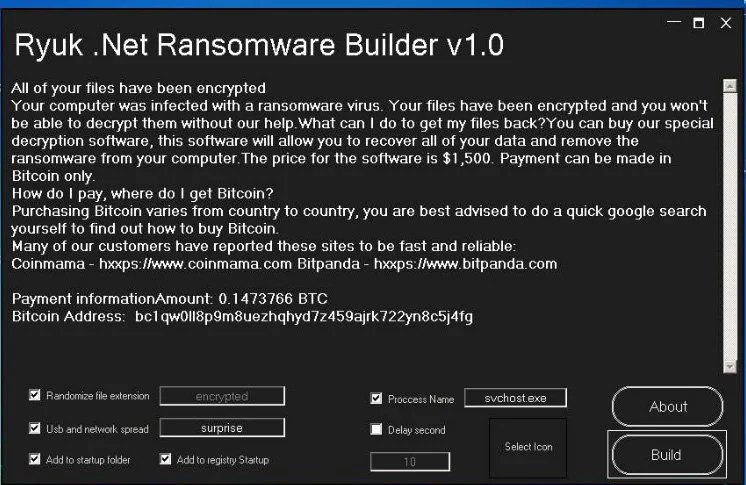
Security Joes found a .NET Ryuk impersonator that can be customized with a ransomware builder.
JBS, the world’s largest beef producer, has confirmed that they paid an $11 million ransom after the REvil ransomware operation initially demanded $22.5 million.
CD Projekt is warning today that internal data stolen during their February ransomware attack is circulating on the Internet.
Foodservice supplier Edward Don has suffered a ransomware attack that has caused the company to shut down portions of the network to prevent the attack’s spread.
Michael Gillespie found a new Vice Society ransomware that appends the .v-society extension when encrypting Linux machines. Appears to be a spin-off of HelloKitty.
xiaopao found a new Anubis ransomware variant that appends the .ChupaCabra extension.
The Avaddon ransomware gang has shut down operation and released the decryption keys for their victims to BleepingComputer.com.
One of the ransomware-as-a-service (RaaS) we encounter most frequently, known alternately as Sodinokibi or REvil, is as conventional a ransomware as we’ve seen: Its routines, configuration, and behavior what we’ve come to expect from a mature family that’s, obviously, well used in the criminal underground.
When the Teamsters were hit by a ransomware attack over Labor Day weekend in 2019, the hackers asked for a seven-figure payment.
Also Read: How to Comply with PDPA: A Checklist for Businesses
An interview with the CEO of Coveware, which negotiates payments on behalf of ransomware victims.