KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Ransomware operations have been quieter this week as the White House engages in talks with the Russian government about cracking down on cybercriminals believed to be operating in Russia.
This increased scrutiny by law enforcement and the growing fear that Russia is no longer a safe haven for cybercriminals has led to what is believed to be the shutdown of the notorious REvil ransomware operation.
Earlier this week, all of the infrastructures for the REvil ransomware operation shut down with no word from the public-facing representative ‘Unknown’ or the group’s affiliates.
This shutdown is not believed to be caused by law enforcement, and it is likely we will see this group rebrand as a new operation in the future.
This week’s other news includes finding a Linux version of the HelloKitty ransomware used to target VMware ESXi servers and its virtual machines.
Finally, the US government launched the StopRansomware site that includes information on protecting, mitigating, and recovering from ransomware attacks.
The US government announced a new initiative under the Rewards for Justice programs that will reward up to $10 million for information about state-sponsored hackers targeting critical infrastructure and US interests.
Contributors and those who provided new ransomware information and stories this week include: @malwrhunterteam, @fwosar, @PolarToffee, @VK_Intel, @FourOctets, @serghei, @demonslay335, @LawrenceAbrams, @Ionut_Ilascu, @BleepinComputer, @Seifreed, @DanielGallagher, @malwareforme, @struppigel, @jorntvdw, @uuallan, @pcrisk, @Artilllerie, @Unit42_Intel, @AuCyble, and @fbgwls245.
President Biden asked Russian President Putin during a phone call today to disrupt ransomware groups operating within Russia’s borders behind the ongoing wave of attacks impacting the United States and other countries worldwide.
dnwls0719 found a new Phobos Ransomware variant that appends the .LOWPRICE extension to encrypted files.
Also Read: When to Appoint a Data Protection Officer
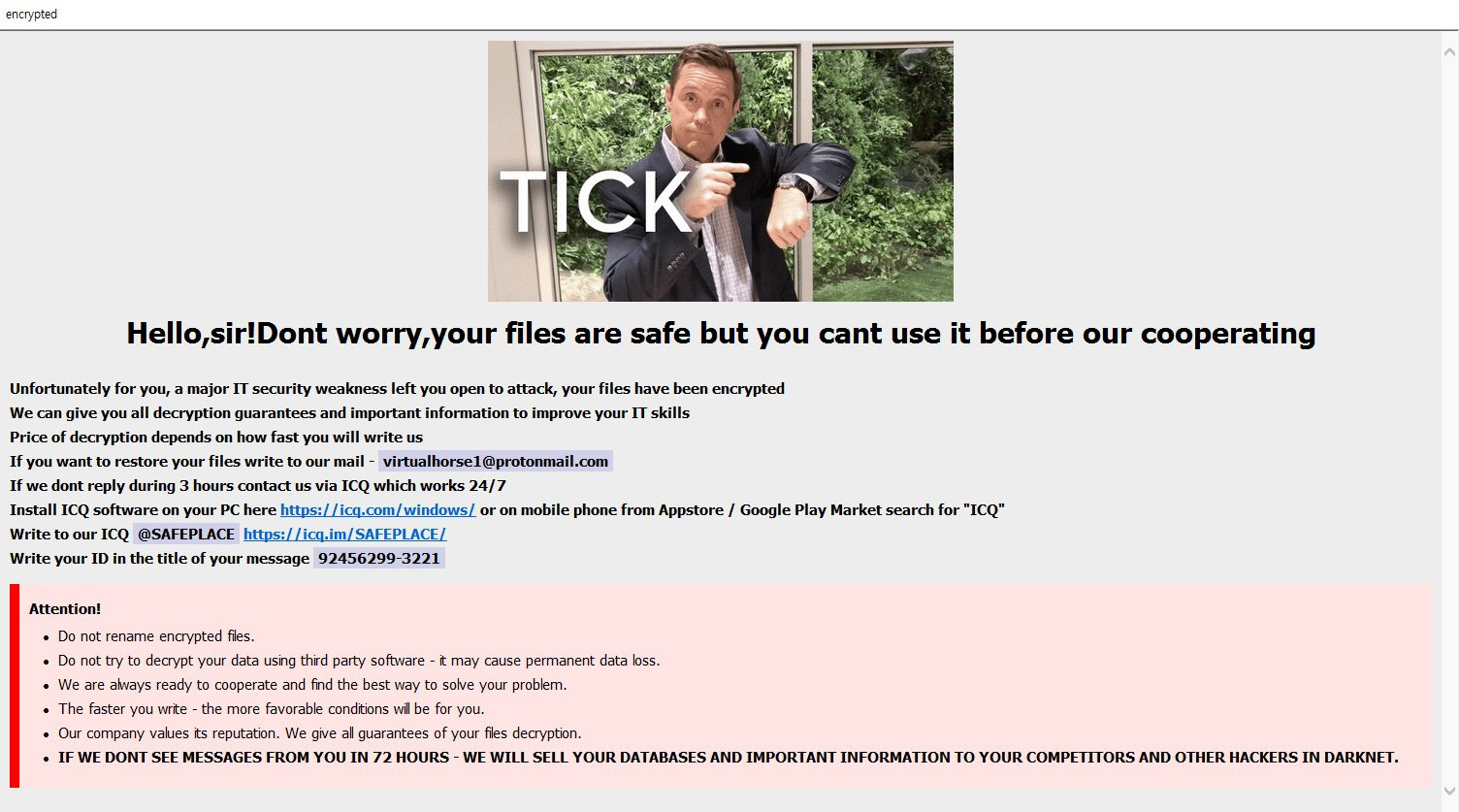
PCrisk found a new STOP ransomware variant that appends the .wwka extension.
Kaseya has released a security update for the VSA zero-day vulnerabilities used by the REvil ransomware gang to attack MSPs and their customers.
American fashion brand and retailer Guess is notifying affected customers of a data breach following a February ransomware attack that led to data theft.
Interpol (International Criminal Police Organisation) Secretary General Jürgen Stock urged police agencies and industry partners to work together to prevent what looks like a future ransomware pandemic.
The infrastructure and websites for the REvil ransomware operation have mysteriously gone offline as of last night.
PCrisk found a new STOP ransomware variant that appends the .gujd extension.
SonicWall has issued an “urgent security notice” warning customers of ransomware attacks targeting unpatched end-of-life (EoL) Secure Mobile Access (SMA) 100 series and Secure Remote Access (SRA) products.
PCrisk found a new Dharma ransomware variant that appends the .PcS extension.
?The ransomware gang behind the highly publicized attack on CD Projekt Red uses a Linux variant that targets VMware’s ESXi virtual machine platform for maximum damage.
PCrisk found new Dharma ransomware variants that appends the .OFF and .pause extensions.
As cyber extortion flourishes, ransomware gangs are constantly changing tactics and business models to increase the chances that victims will pay increasingly large ransoms. As these criminal organizations become more sophisticated, they are increasingly taking on the appearance of professional enterprises. One good example is Mespinoza ransomware, which is run by a prolific group with a penchant for using whimsical terms to name its hacking tools.
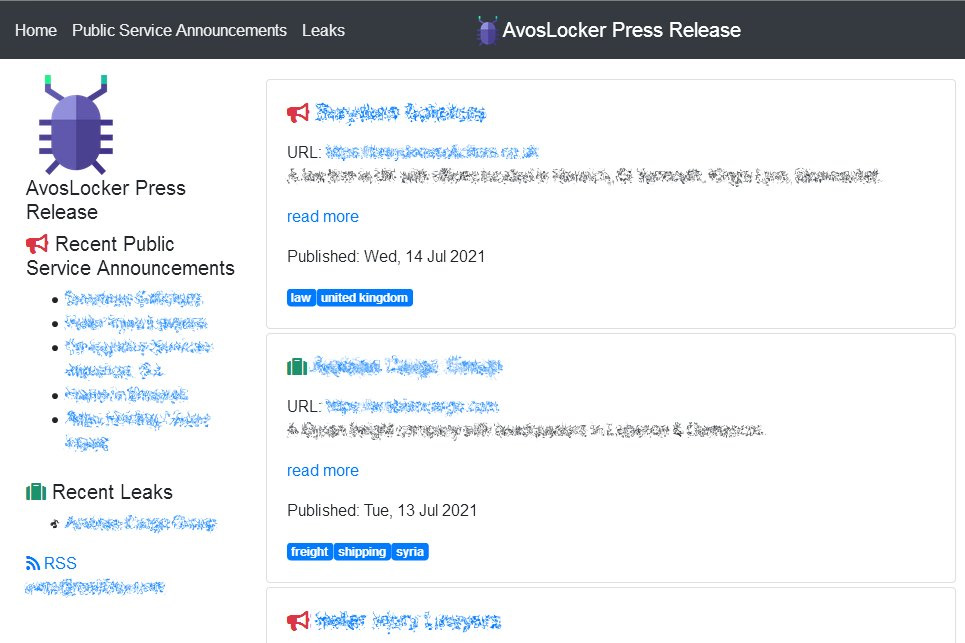
During our routine Open-source Intelligence (OSINT) research, we came across a new ransomware group named AvosLocker. It is a malicious program that infects Windows machines to encrypt document files of the victim and asks for ransom as part of its extortion program. AvosLocker appends the encrypted files with the extension .avos and forces victims to pay ransom for the decryption tool for recovering their data. The AvosLocker ransomware group uses spam email campaigns or distrustful advertisements as the primary delivery mechanisms for the malware. It uses a customized Advanced Encryption Standard (AES) with block size 256 to encrypt the data.
Artilllerie noted that the AvosLocker ransomware launched a data leak site.
Also Read: 4 Things to Know When Installing CCTVs Legally
The United States government has taken two more active measures to fight and defend against malicious cyber activities affecting the country’s business and critical infrastructure sectors.
Many victims of the Kaseya ransomware attack are still in the process of recovering but one victim is facing a particularly difficult issue.