KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







It has been another quiet week for ransomware, though we did have some interesting stories come out this week.
By far, the most interesting is the news about ChastityLocker – ransomware that exploits vulnerabilities in men’s chastity belts (not joking) so that they can’t unlock them.
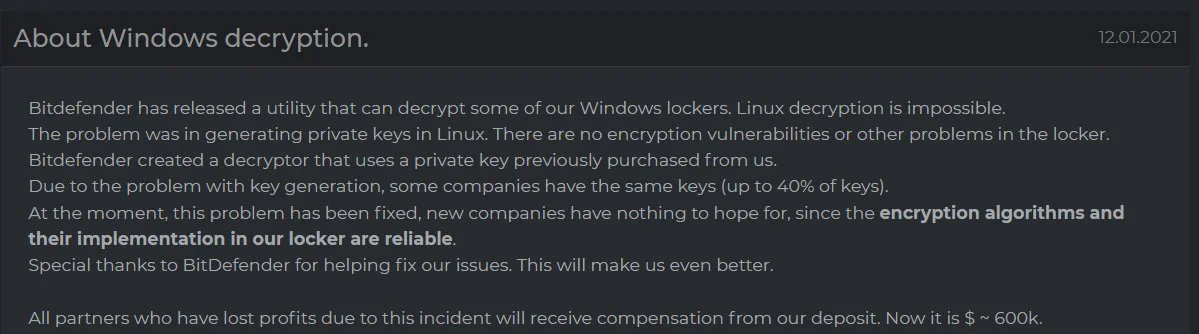
Other interesting news is Intel’s announcement that their new vPro chips will have built-in hardware ransomware detection and BitDefender released a decryptor for the DarkSide ransomware.
Unfortunately, after the decryptor was released, the DarkSide operation announced that they fixed the weakness allowing the decryptor to work.
Contributors and those who provided new ransomware information and stories this week include: @struppigel, @Ionut_Ilascu, @VK_Intel, @BleepinComputer, @FourOctets, @serghei, @Seifreed, @malwrhunterteam, @demonslay335, @DanielGallagher, @fwosar, @malwareforme, @jorntvdw, @PolarToffee, @LawrenceAbrams, @Telekom_group, @LukasStefanko, @GrujaRS, @Bitdefender, @vxunderground, @JakubKroustek, @M_Shahpasandi, @Kangxiaopao, @ExtendedRaavan, and @Amigo_A_.
Also Read: What Is A Governance Framework? The Importance And How It Works
The source code for the ChastityLock ransomware that targeted male users of a specific adult toy is now publicly available for research purposes.
Jakub Kroustek found three new Dharma ransomware variants that append the .hub, .aol, or .14x extension to encrypted files.
Intel announced today at CES 2021 that they have added hardware-based ransomware detection to their newly announced 11th generation Core vPro business-class processors.
Romanian cybersecurity firm Bitdefender has released a free decryptor for the DarkSide ransomware to allow victims to recover their files without paying a ransom.
Raavan Extended found a new STOP Ransomware variant that appends the .qlkm extension.
Amigo-A found a new STOP Ransomware variant that appends the .coos extension.
Amigo-A found a new variant of the Flamingo Ransomware variant that appends the .LIZARDextension and drops a ransom note named ReadThis.txt.
Also Read: Website Ownership Laws: Your Rights And What These Protect
Capcom has released a new update for their data breach investigation and state that up to 390,000 people may now be affected by their November ransomware attack.
xiaopao found a new ransomware that appends the .judge exension and drops a ransom note named info.txt.
TA505 (also known as FIN11) is a financially motivated cybercrime actor. They conduct Big Game Hunting operations, such as deployment of ransomware and extortion of large ransom payment. In the past, I explained how they operate and I scrutinized their tools. If you are not familiar with TA505 and CL0P then I recommend you to read our threat actor profile of TA505 first.
MalwareHunterTeam found a new malicious Android app that includes ransomware capabilities. Lukas Stefanko states that this is a new variant of the Lucy Ransomware.
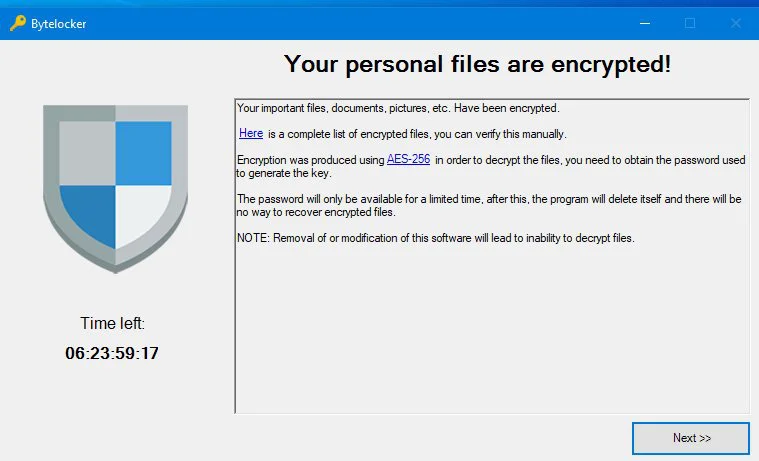
GrujaRS found a new HiddenTear variant called ByteLocker that encrypts files without adding an extension.
Vitali Kremez analyzed a new sample of REvil and found it be very similar to the DarkSide ransomware.
The Scottish Environment Protection Agency (SEPA) confirmed on Thursday that some of its contact center, internal systems, processes and internal communications were affected following a ransomware attack that took place on Christmas Eve.
GrujaRS found a new BlackHeel HiddenTear variant that appends the .a extension to encrypted files.
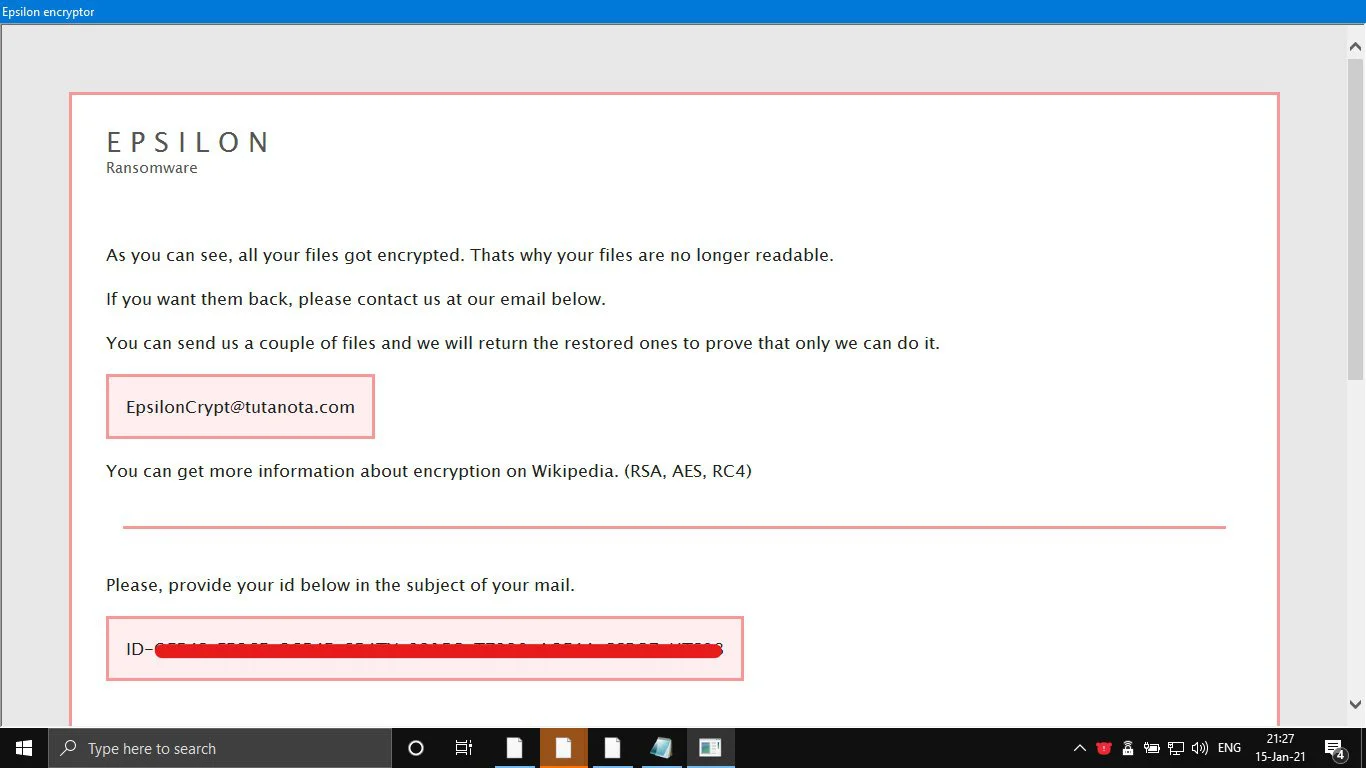
GrujaRS found a new Epsilon Ransomware that appends the .boom extension and drops a ransom note named READ_ME.hta.