KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Critical infrastructure suffered ransomware attacks, with threat actors targeting an oil petrol distributor and oil terminals in major ports in different attacks.
Earlier this week, German petrol distributor Oiltanking suffered a ransomware attack allegedly by the new ALPHV/BlackCat ransomware operation.
Soon after, oil terminals in major ports disclosed that they too suffered ransomware attacks. However, officials do not believe the attacks are linked.
If critical infrastructure was not bad enough, the Conti ransomware gang attacked British snacks giant KP Snacks, causing disruptions in the supply chain.
The UK’s HHS released a summary of the findings from the attack on Ireland’s HSE and said that 80% of the IT systems were encrypted during the attack.
Also Read: 4 Trends on data protection strategy in 2022 to watch for
Finally, RecordedFuture conducted an interview with the ALPHV ransomware gang, which provides some interesting insights into their new operation.
Contributors and those who provided new ransomware information and stories this week include: @jorntvdw, @demonslay335, @PolarToffee, @malwrhunterteam, @struppigel, @serghei, @billtoulas, @Ionut_Ilascu, @FourOctets, @malwareforme, @VK_Intel, @LawrenceAbrams, @fwosar, @DanielGallagher, @BleepinComputer, @Seifreed, @cybereason, @Ax_Sharma, @Walmarttech, @JakubKroustek, @Amigo_A_, @mattburgess1, @fbgwls245, @pcrisk, @ddd1ms, @AdamJanofsky, and @BrettCallow.
Taiwan-based network-attached storage (NAS) maker QNAP urges customers to enable firmware auto-updating on their devices to defend against active attacks.
PCrisk found a Phobos ransomware variant that appends the .makop extension. Makop is the name of a different ransomware operation.
Oiltanking GmbH, a German petrol distributor who supplies Shell gas stations in the country, has fallen victim to a cyberattack that severely impacted its operations.
An Iranian state-backed hacking group tracked as APT35 (aka Phosphorus or Charming Kitten) is now deploying a new backdoor called PowerLess and developed using PowerShell.
Internal messages WIRED has viewed shed new light on the operators of one of the world’s biggest botnets.
Amigo-A found a new STOP ransomware variant that appends the .bbbw extension.
KP Snacks, a major producer of popular British snacks has been hit by the Conti ransomware group affecting distribution to leading supermarkets.
Also Read: Top 5 cybersecurity and data protection articles you loved in 2021
Morley Companies Inc. disclosed a data breach after suffering a ransomware attack on August 1st, 2021, allowing threat actors to steal data before encrypting files.
Jakub Kroustek found two new STOP ransomware variants that append the .bbbr or .bbbe extensions.
PCRisk found a new STOP ransomware variant that appends the .maiv extension.
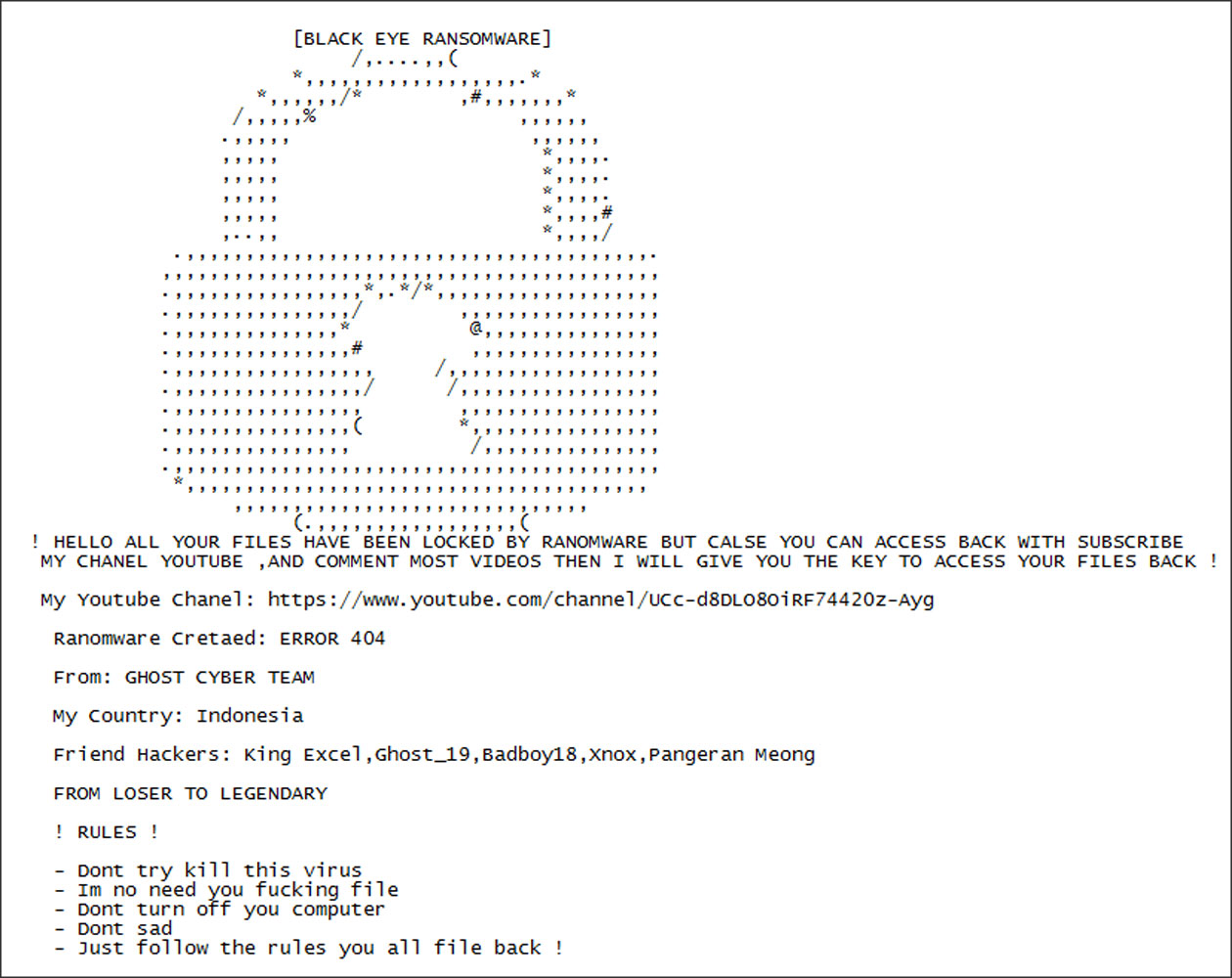
MalwareHunterTeam found a new ransomware that requires you to subscribe to a YouTube channel to decrypt your files. Seems more like a joke.
PCRisk found a new STOP ransomware variant that appends the .qqqr extension.
Major oil terminals in some of Western Europe’s biggest ports have fallen victim to a cyberattack at a time when energy prices are already soaring, sources confirmed on Thursday.
The attacks targeted organizations in Belgium, the Netherlands, and Germany, including some of the largest ports in the region. Cybersecurity officials from those countries on Thursday said they do not have reason to believe that the attacks are linked to one another.
Aviation services company Swissport International has disclosed a ransomware attack that has impacted its IT infrastructure and services, causing flights to suffer delays.
A threat brief published by the US Department of Health and Human Services (HHS) on Thursday paints a grim picture of how Ireland’s health service, the HSE, was overwhelmed and had 80% of its systems encrypted during last year’s Conti ransomware attack.
A new Sugar Ransomware operation actively targets individual computers, rather than corporate networks, with low ransom demands.
A representative from the group, which has also been called BlackCat in some reports, agreed to talk to Recorded Future analyst Dmitry Smilyanets about the group’s background, intentions, and plans for the future. The interview was conducted in Russian via TOX messaging, and was translated to English with the help of a linguist from Recorded Future’s Insikt Group. It has been lightly edited for clarity.
dnwls0719 found a new ransomware that appends the .SG1995 extension.