KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The SolarWinds supply chain attack has dominated this week’s cybersecurity news, but there was still plenty of ransomware news this week.
Over the past month, Israel has been targeted in a series of cyberattacks that are attributed to Iran. This week, the Pay2Key ransomware actors targeted on another Israel company in an attack on Intel’s Habana Labs. This group appears to be focused on causing havoc for Israeli interests rather than generating a ransom payment.
We also saw a threat actor capitalizing on Cyberpunk 2077’s release by distributing ransomware disguised as the game.
Other than that, it has been mostly new variants of existing ransomware released this week.
Contributors and those who provided new ransomware information and stories this week include: @Seifreed, @FourOctets, @malwareforme, @jorntvdw, @VK_Intel, @malwrhunterteam, @BleepinComputer, @LawrenceAbrams, @DanielGallagher, @Ionut_Ilascu, @demonslay335, @serghei, @struppigel, @fwosar, @PolarToffee, @GelosSnake, @sh1shk0va, @ClearskySec, @ProferoSec, @OhadMZ, @Sophos, @thepacketrat, @JakubKroustek, @siri_urz, @BeazleyGroup, @darb0ng, @Kangxiaopao, and @RakeshKrish12.
Intel-owned AI processor developer Habana Labs has suffered a cyberattack where data was stolen and leaked by threat actors.
S!ri found a new Conti variant that appends the .KCWTT extension to encrypted files.
S!ri found a new variant of the Ouroboros ransomware that appends the .Sophos extension.
Also Read: The Scope Of Singapore Privacy: How We Use It In A Right Way
MalwareHunterTeam found a new Zeoticus 2.0 ransomware variant that appends the .2020END extension. Guess they are fed up with this year also.
Michael Gillespie found a new STOP Ransomware variant that appends the .booa extension.
Minhee Lee found the Clop ransomware variant used in the Symrise attack.
The City of Independence, Missouri, suffered a ransomware attack last week that continues to disrupt the city’s services.
Jakub Kroustek found two new Dharma Ransomware variants that append the .msf or .lock extensions.
Michael Gillespie found a new Phobos variant that appends the “.id[].[ICQ_Sophos].Antivirus” extension.
SystemBC, a commodity malware sold on underground marketplaces, is being used by ransomware-as-a-service (RaaS) operations to hide malicious traffic and automate ransomware payload delivery on the networks of compromised victims.
In an incredibly challenging year in which ransomware has easily become the biggest cyber threat to impact individuals and organizations alike, the severity of ransomware attacks has continued to escalate. During 2020, these incidents have reached new levels of complexity, having developed a long way from the early incarnations of ransomware designed to trick an employee into clicking on a bad email that then encrypts a workstation and file shares.
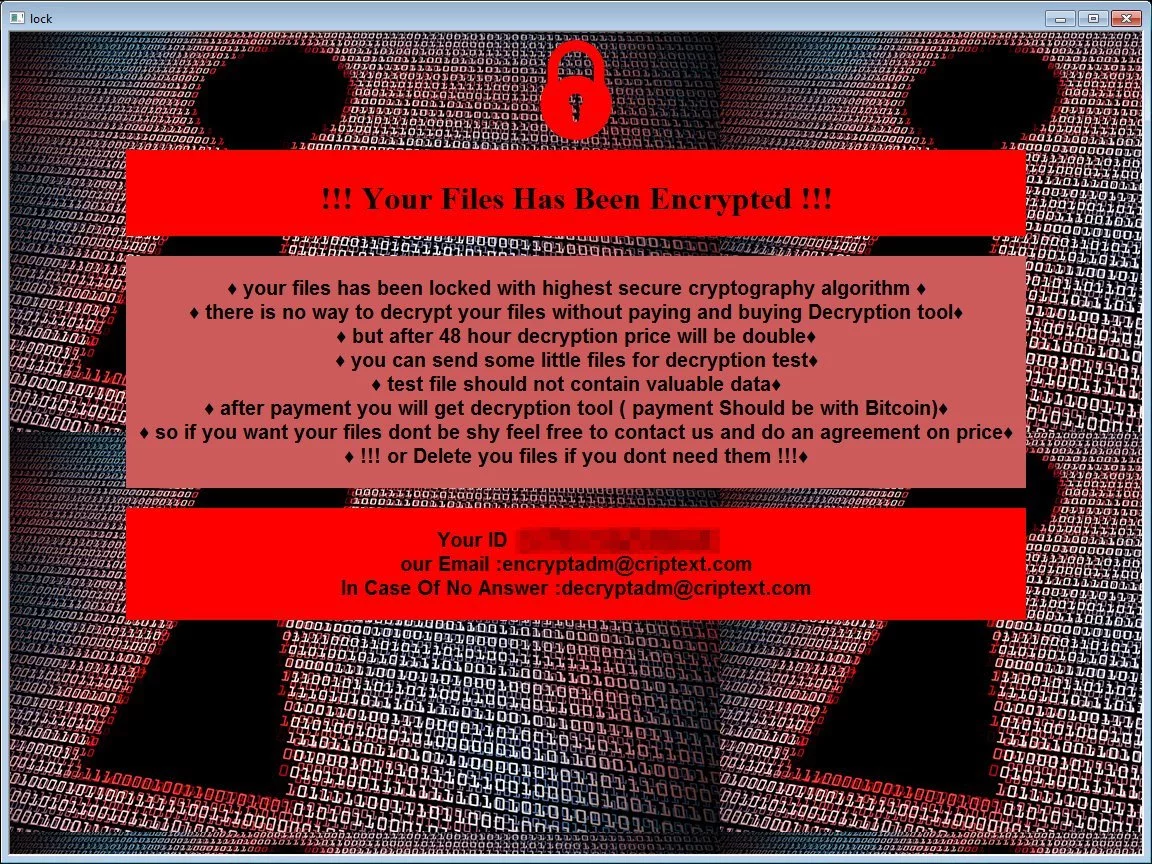
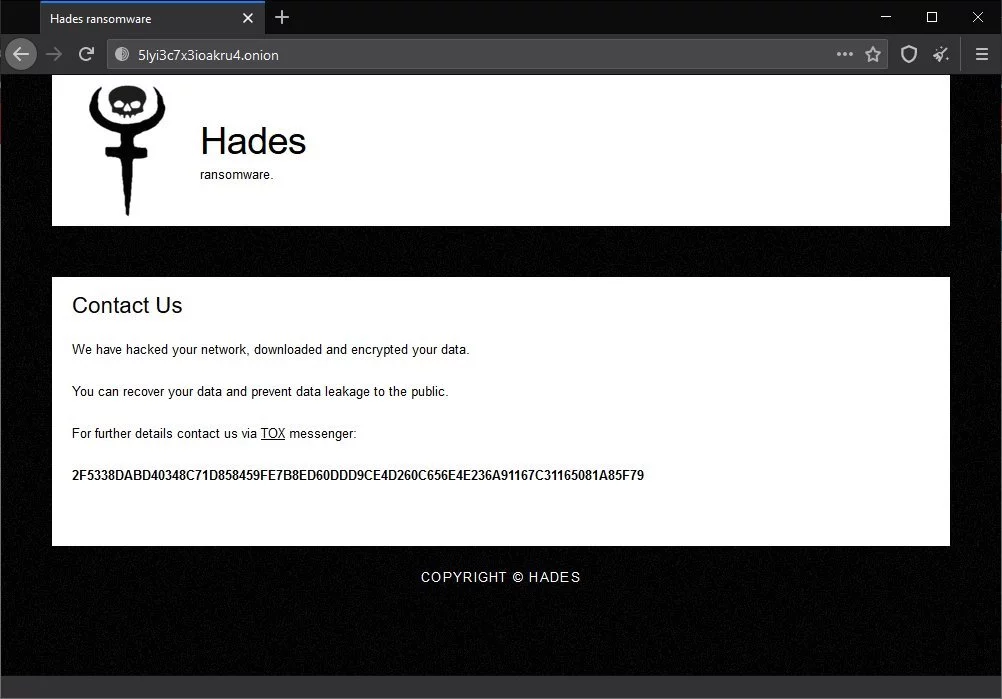
Michael Gillespie found a new ransomware calling itself Hades Ransomware that appends a random extension and drops ransom note named “HOW-TO-DECRYPT-xxxxx.txt.”
Also Read: Deemed Consent PDPA: How Do Businesses Comply?
MalwareHunterTeam found a HiddenTear variant that appends the .fmfgmfgm extension.
MalwareHunterTeam found a silly bootlocker named COVID-20 ransomware.
Iranian-backed hacking group Fox Kitten has been linked to the Pay2Key ransomware operation that has recently started targeting organizations from Israel and Brazil.
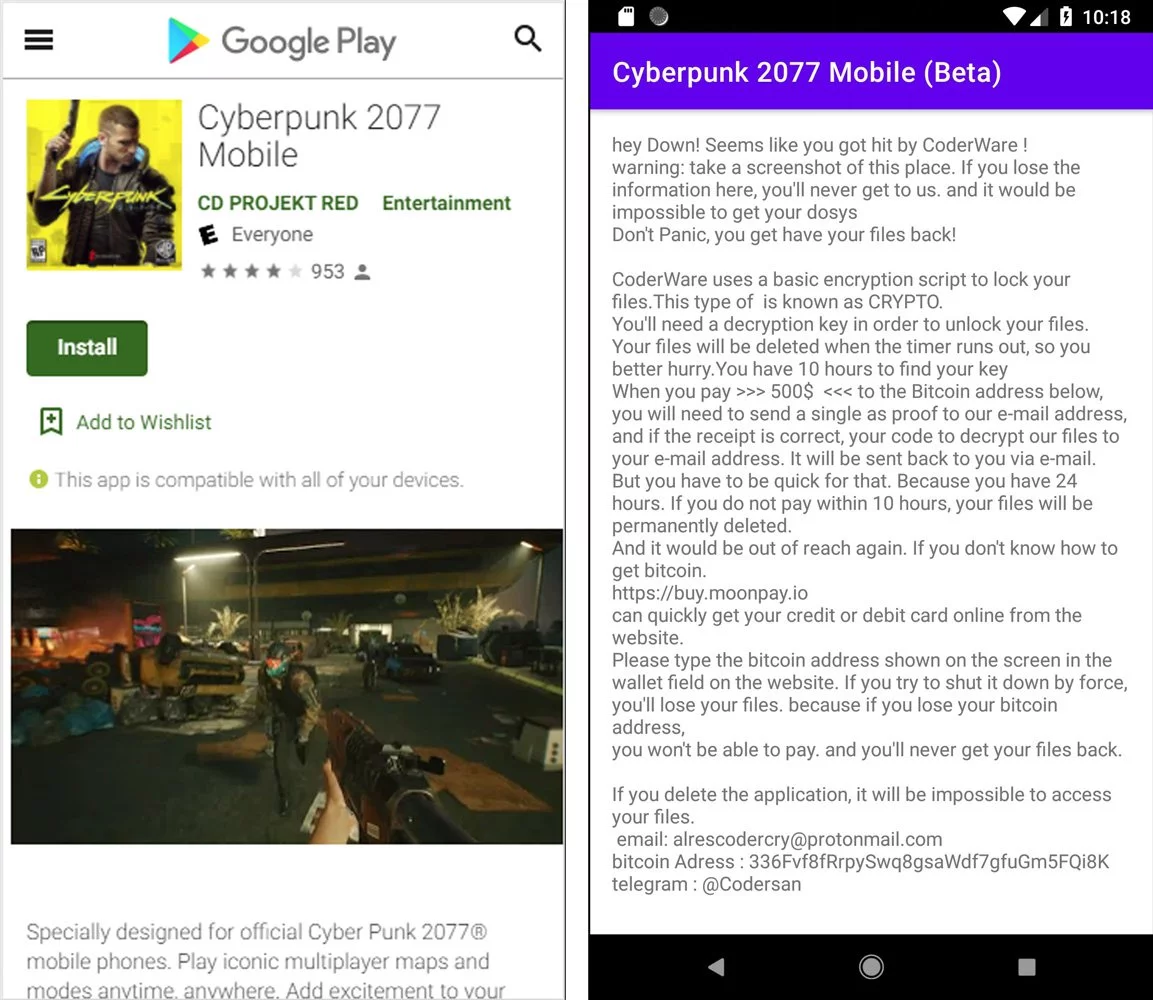
A threat actor is distributing fake Windows and Android installers for the Cyberpunk 2077 game that is installing a ransomware calling itself CoderWare.
Michael Gillespie found a new STOP Ransomware variant that appends the .omfl extension.
xiaopao found a new Hakbit variant that appends the .rastar extension.
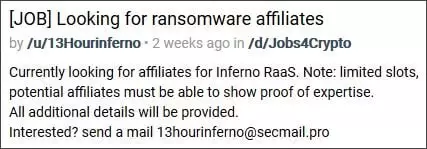
RAKESH KRISHNAN found a new ransomware-as-a-service called Inferno that is recruiting affiliates.