KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Ransomware gangs continue to target organizations large and small, including a brazen attack on the Washington DC police department.
This week, we learned of attacks affecting the Metropolitan Police Department, Merseyrail UK rail operator, the Whistler Resort Municipality, and an attack on Brazil’s court systems in Rio Grande do Sul.
We also reported that the Qlocker ransomware targeting QNAP devices had made $260,000 by Sunday, which is likely much higher now.
Finally, after threatening to release data for the Metropolitan Police Department, Babuk Locker has suddenly decided to no longer encrypt systems and focus entirely on the ransoming of stolen data.
Contributors and those who provided new ransomware information and stories this week include: @fwosar, @PolarToffee, @Seifreed, @struppigel, @jorntvdw, @BleepinComputer, @Ionut_Ilascu, @LawrenceAbrams, @malwareforme, @demonslay335, @serghei, @malwrhunterteam, @FourOctets, @DanielGallagher, @VK_Intel, @ValeryMarchive, @emsisoft, @fbgwls245, @Amigo_A_, @chum1ng0, @pcrisk, @GrujaRS, @BruteBee, @FireEye, @ddd1ms, @coveware, @campuscodi, and @JakubKroustek.
A ransomware gang has made $260,000 in just five days simply by remotely encrypting files on QNAP devices using the 7zip archive program.
Jakub Kroustek found a new Dharma ransomware variant that appends the .bdev extension to encrypted files.
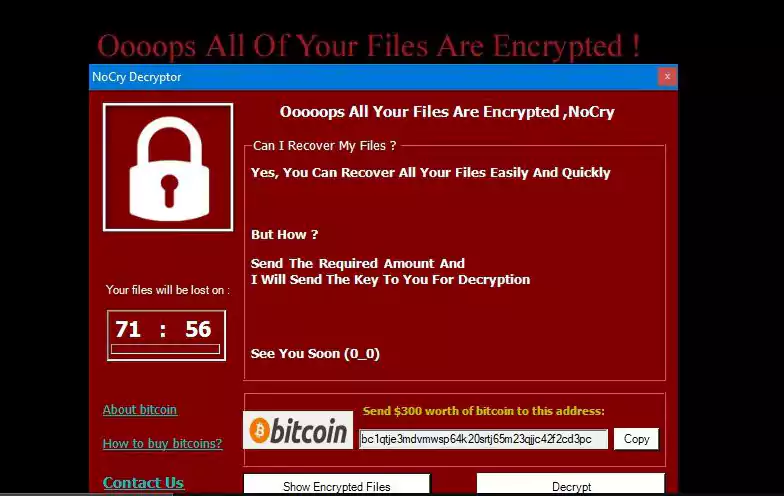
GrujaRS found a variant of the Stupid Ransomware calling itself NoCry that appends the .Cry extension.
GrujaRS found a new variant of the Conti Ransomware that appends the .GFYPK extension.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
The Metropolitan Police Department has confirmed that they suffered a cyberattack after the Babuk ransomware gang leaked screenshots of stolen data.
The REvil ransomware gang has mysteriously removed Apple’s schematics from their data leak site after privately warning Quanta that they would leak drawings for the new iPad and new Apple logos.
The data breaches caused by the Clop ransomware gang exploiting a zero-day vulnerability have led to a sharp increase in the average ransom payment calculated for the first three months of the year.
dnwls0719 found a new Dharma ransomware variant that appends the .ALNBR extension to encrypted files.
The Coveware Quarterly Ransomware Report describes ransomware incident response trends during Q1 of 2021. Data exfiltration extortion continues to be prevalent and we have reached an inflection point where the vast majority of ransomware attacks now include the theft of corporate data. Q1 saw a reversal of average and median ransom amounts. The averages in Q1 were pulled up by a raft of data exfiltration attacks by one specific threat actor group that opportunistically leveraged a unique vulnerability (more on this below).
PCrisk found a new Phobos ransomware variant that appends the .lookfornewitguy extension.
Oui, le groupe Revil, qui pilote le rançongiciel Sodinokibi, est très actif ces temps-ci. Et il semble décidé à enchaîner les coups d’éclat. Mais ses activités semblent de moins en moins couronnées de succès. Et de plus en plus, ce qu’il exhibe comme un tableau de chasse prend des airs de triste galerie de ses échecs.
The statistics below show the devastating economic toll ransomware has taken in a number of key markets. The data includes ransom demands, the cost of downtime, and the overall global cost of ransomware, as well as separate statistics focused on the public and private sectors.
Microsoft SharePoint servers have now joined the list of network devices being abused as an entry vector into corporate networks by ransomware gangs.
UK rail network Merseyrail has confirmed a cyberattack after a ransomware gang used their email system to email employees and journalists about the attack.
dnwls0719 found a new Dharma ransomware variant that appends the .cum extension to encrypted files.
The Ransomware Task Force, a public-party coalition of more than 50 experts, has shared a framework of actions to disrupt the ransomware business model.
The Whistler municipality in British Columbia, Canada, has suffered a cyberattack at the hands of a new ransomware operation.
Brazil’s Tribunal de Justiça do Estado do Rio Grande do Sul was hit with an REvil ransomware attack yesterday that encrypted employee’s files and forced the courts to shut down their network.
A financially motivated threat actor exploited a zero-day bug in Sonicwall SMA 100 Series VPN appliances to deploy new ransomware known as FiveHands on the networks of North American and European targets.
QNAP customers are once again urged to secure their Network Attached Storage (NAS) devices to defend against Agelocker ransomware attacks targeting their data.
After just a few months of activity, the operators of Babuk ransomware briefly posted a short message about their intention to quit the extortion business after having achieved their goal.
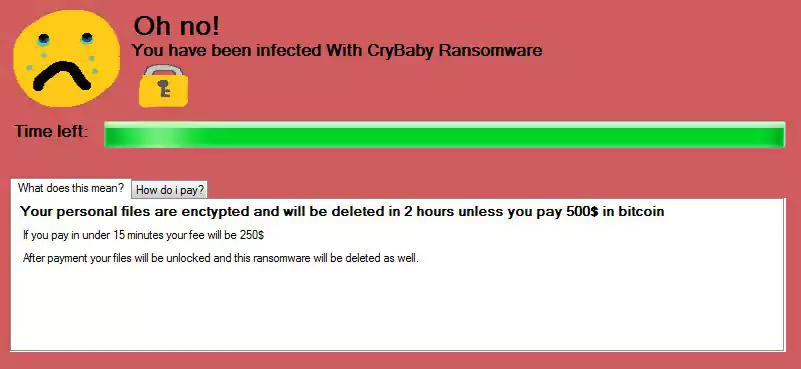
MalwareHunterTeam found a new ‘CryBaby’ ransomware.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
A new message today from the operators of Babuk ransomware clarifies that the gang has decided to close the affiliate program and move to an extortion model that does not rely on encrypting victim computers.
That’s it for this week! Hope everyone has a nice weekend!