KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Target, one of the largest American department store chains and e-commerce retailers, has open sourced ‘Merry Maker’ – its years-old proprietary scanner for payment card skimming.
A skimmer is malicious code injected into shopping sites to steal customers’ credit card data at checkout. The code can be hidden on the online store or it can be loaded from external resources, sometimes via a local element such as a favicon.
By open-sourcing Merry-Maker, Target helps online retailers fight the credit card skimming threat that’s been affecting the sector for years.
Also Read: How To Delete Security Camera Footage: 5 Different Ways
Target has been running its online shop since 2002, offering almost all products that one can find in the brick-and-mortar locations of the chain. The site is an attractive target for credit card thieves as it enjoys high traffic (Alexa rank: 200).
As the credit card skimming threat increased, two of Target’s security engineers, Eric Brandel and Caleb Walch, took action and in 2018 they created ‘Merry Maker’ to detect code that steals payment card data.
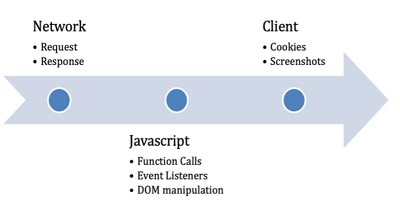
The tool simulates real user activity through test transactions, which are flagged accordingly internally. It then collects and analyzes the resulting network requests, JavaScript file activations, and any other signs of unwanted or suspicious activity.
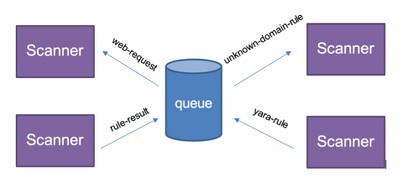
The scanner component of the Merry Maker framework inspects events and determines which rules to apply. There is support for YARA rules, indicators of compromise (IoCs), unknown domain rule.
Merry Maker relies on Puppeteer – a Node.js component, to control the client-side scanner implemented through a headless browser (Headless Chrome), Target explains in a more technical report.
Also Read: Top 10 Reliable IT Companies in Singapore
An administration dashboard shows “the current state and health of the system,” recent alerts, the number of events pending, and active scans.
After more than a million scans on Target.com, the company believes that the tool has matured enough to be deployed anywhere without causing operational hiccups.
As such, Target has decided to open-source the tool and share it with the community along with several detection rules to help “other cybersecurity teams stand up their own customized defense.”
The framework is available on the company’s GitHub page.