KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hackers suspected to work for the Chinese government have used a new malware called PortDoor to infiltrate the systems of an engineering company that designs submarines for the Russian Navy.
They used a spear-phishing email specifically crafted to lure the general director of the company into opening a malicious document.
The threat actor targeted Rubin Central Design Bureau for Marine Engineering in Saint Petersburg, a defense contractor that designed most of Russia’s nuclear submarines.
The method for delivering the backdoor was a weaponized RTF document attached to an email addressed to the company CEO, Igor V. Vilnit.
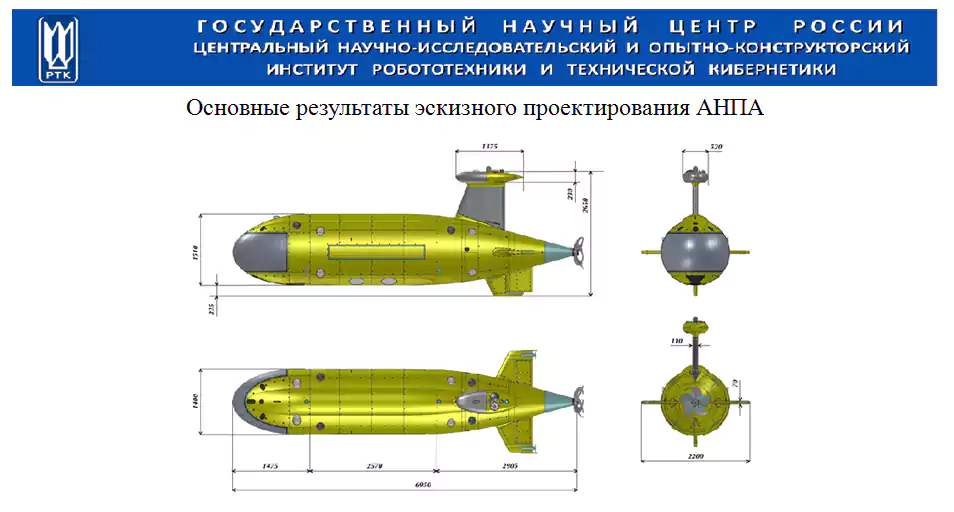
Threat researchers at Cybereason Nocturnus found that the attacker lured the recipient to open the malicious document with a general description for an autonomous underwater vehicle.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
Digging deeper, the researchers discovered that the RTF file had been weaponized using RoyalRoad, a tool for building malicious documents to exploit multiple vulnerabilities in Microsoft’s Equation Editor.
The use of RoyalRoad has been linked in the past to several threat actors working on behalf of the Chinese government, like Tick, Tonto Team, TA428, Goblin Panda, Rancor, Naikon.
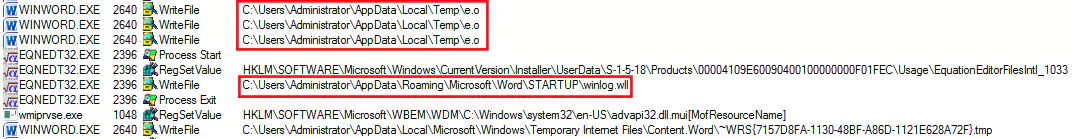
When launched, the RTF document drops the PortDoor backdoor in the Microsoft Word startup folder disguising it as an add-in file, “winlog.wll.”
According to Cybereason’s analysis, PortDoor is a full-fledged backdoor with an extended list of features that make it suitable for a variety of tasks:
In a technical report today, Cybereason Nocturnus Team describes the functionality of the malware and provides indicators of compromise to help organizations defend against it.
The researchers attributed PortDoor to a Chinese state-sponsored hacker group based on similarities in tactics, techniques, and procedures with other China-linked threat actors.
Based on work from security researcher nao_sec, Cybereason was able to determine that the malicious RTF document was created with RoaylRoad v7 with a header encoding associated with operations from Tonto Team (a.k.a. CactusPete), Rancor, and TA428.
CactusPete and TA428 are known for attacking organizations in Eastern Europe (Russia) and Asia [1, 2, 3, 4]. Furthermore, Cybereason saw linguistic and visual elements in the PortDoor phishing email and documents that resemble the lures in attacks from Tonto Team.
However, at the code level, PortDoor does not share significant similarities with other malware used by the aforementioned groups, indicating that this is a new backdoor.
Also Read: How To Comply With PDPA: A Checklist For Businesses
Cybereason’s attribution of PortDoor does not come with a high level of confidence. The researchers are aware that other groups may be behind this malware. Current evidence, though, points to an attacker of Chinese origin.
“Lastly, we are also aware that there could be other groups, known or yet unknown, that could be behind the attack and the development of the PortDoor backdoor. We hope that as time goes by, and with more evidence gathered, the attribution could be more concrete”
– Cybereason