KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A flood of attacks is targeting unsecured MongoDB servers and wiping their databases. Left behind are notes demanding a ransom payment, or the data will be leaked, and the owners reported for GDPR violations.
Being tracked by Victor Gevers, the chairman of the non-profit GDI Foundation, attackers are scanning the Internet for unsecured MongoDB servers.
Once they gain access to the server, they wipe the databases and create a new database called “READ_ME_TO_RECOVER_YOUR_DATA.”
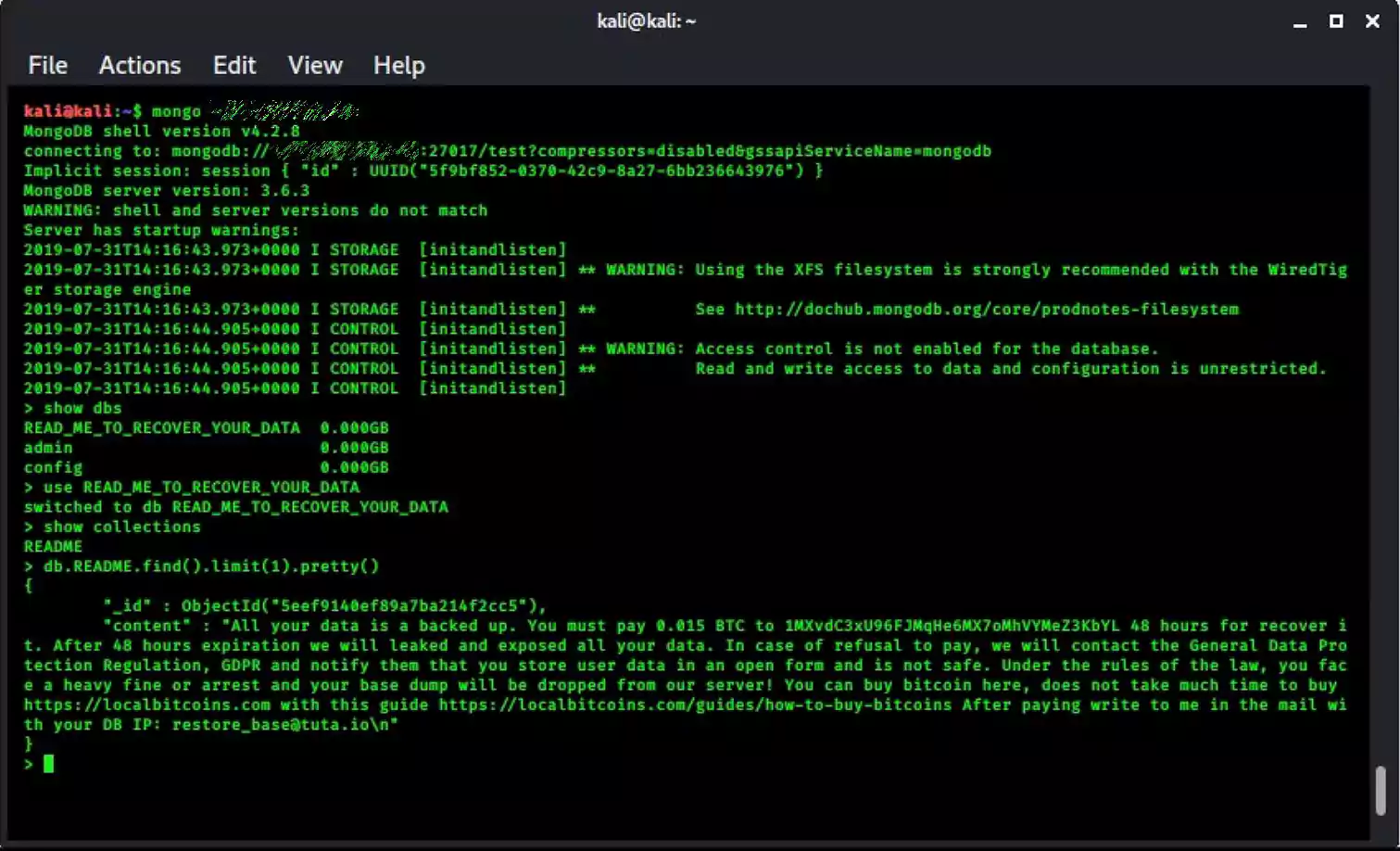
Within this database is a collection named ‘README’ that contains a ransom note explaining that their data was “backed up” and that the victim must pay 0.015 BTC ($135.55) to recover their data.
"All your data is a backed up. You must pay 0.015 BTC to 13JwJDaU3xdNFfcSySFCy95E2Tko18fiyB 48 hours for recover it. After 48 hours expiration we will leaked and exposed all your data. In case of refusal to pay, we will contact the General Data Protection Regulation, GDPR and notify them that you store user data in an open form and is not safe. Under the rules of the law, you face a heavy fine or arrest and your base dump will be dropped from our server! You can buy bitcoin here, does not take much time to buy https://localbitcoins.com with this guide https://localbitcoins.com/guides/how-to-buy-bitcoins After paying write to me in the mail with your DB IP: [email protected]"
Gevers told BleepingComputer that the IoT search engine Shodan lists 15K affected MongoDBs, while BinaryEdge shows 23K servers.
When BleepingComputer performed a quick test of searching for MongoDB servers on Shodan, we quickly saw numerous servers being ransomed from this attack,
Also read: 7 Key Principles of Privacy by Design that Businesses should adopt
Attacks against unsecured database servers are nothing new, with MongoDB and ElasticSearch databases being targets in massive attacks in the past.
What makes this attack stand out is the extortionist’s threat to leak the data in the database if not paid and then report the owners for GDPR violations.
“After 48 hours expiration we will leaked and exposed all your data. In case of refusal to pay, we will contact the General Data Protection Regulation, GDPR and notify them that you store user data in an open form and is not safe. Under the rules of the law, you face a heavy fine or arrest and your base dump will be dropped from our servers,” the ransom note reads.
With the ransom amount being small at $135.55 and the worry of GDPR violations, Gevers feels that it may cause some people to pay. The actors then know that the data is valuable to the owner and extort them for even more money.
“The trick is if you pay, then you want your data back and no GDPR trouble. So this means you are willing to pay even more when they extort for more? People pay for real valuable data. So this way, they figure out what has value, I guess.”
From preliminary analysis, Gevers does not think the data was backed up before being wiped.
While he is still performing more analysis, it is strongly advised that you do not pay any ransoms as it’s not likely to get your data back.
Also read: The impact of GDPR and PDPA in Singapore