




The official Python software package repository, PyPI, is getting flooded with spam packages, as seen by BleepingComputer.
These packages are named after different movies in a style that is commonly associated with torrents and “warez” sites hosting pirated content.
Each of these packages is posted by a unique pseudonymous maintainer account, making it challenging for PyPI to remove the packages and spam accounts all at once.
PyPI is being flooded with spam packages named after popular movies in a style commonly associated with torrent or “warez” sites that provide pirated downloads: watch-(movie-name)-2021-full-online-movie-free-hd-…
The discovery came to light when Adam Boesch, senior software engineer at Sonatype was auditing a dataset and noticed a funny-sounding PyPI component named after a popular TV sitcom.
“I was looking through the dataset and noticed ‘wandavision‘ which is a bit strange for a package name.”
“Looking closer I found that package and looked it up on PyPI because I didn’t believe it,” Boesch told BleepingComputer in an interview.
Also Read: 4 Best Practices on How to Use SkillsFuture Credit
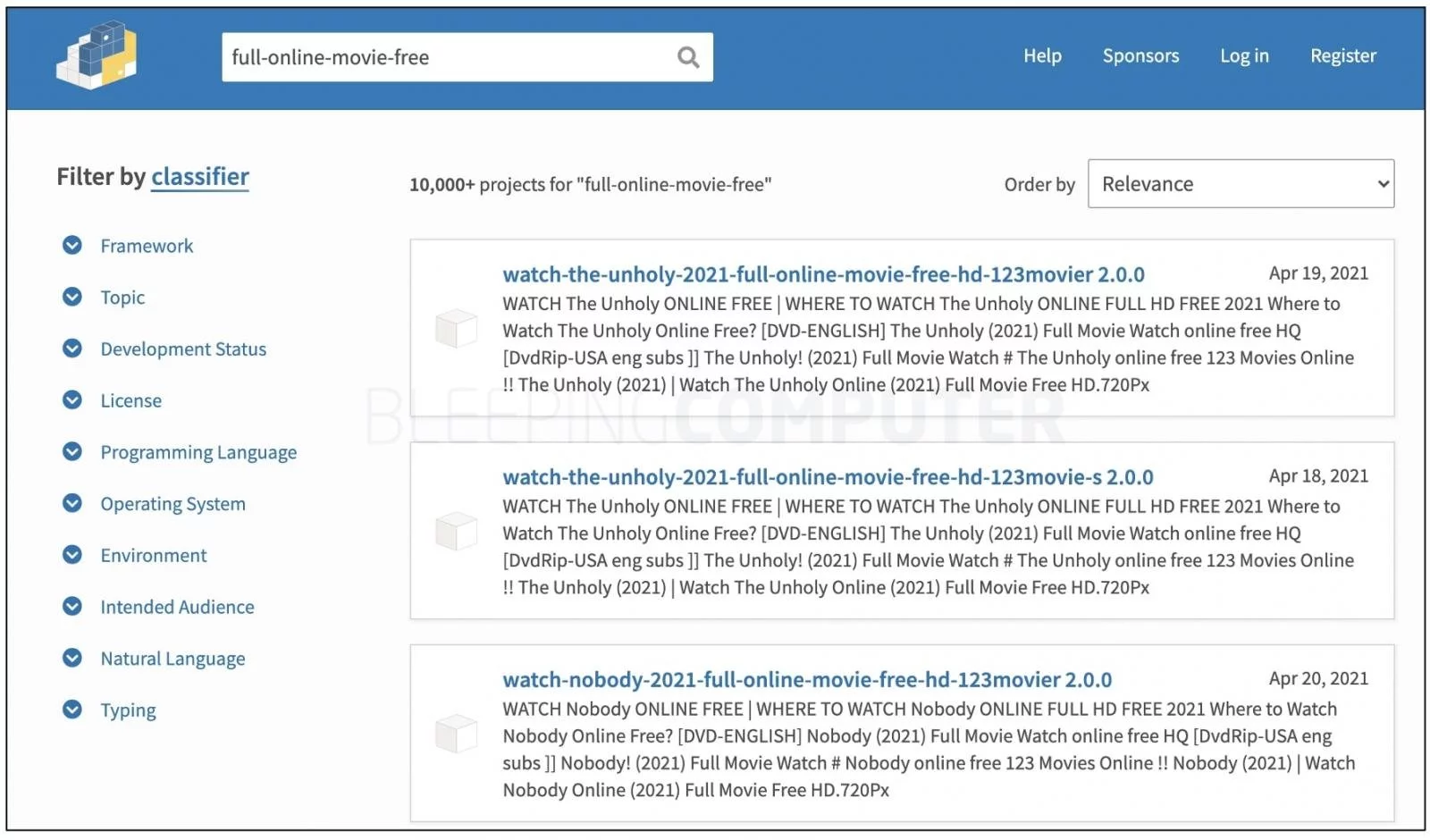
Although some of these packages are a few weeks old, BleepingComputer observed that spammers are continuing to add newer packages to PyPI, as recently as an hour ago.
The search result count of “10,000+” could be inaccurate, as we observed the actual number of spam packages being shown on PyPI repository was much less.
The web page for these bogus packages contain spam keywords and links to movie streaming sites, albeit of questionable legitimacy and legality, such as:https://besflix[.]com/movie/XXXXX/profile.html
Below is one example of the many packages posted about an hour ago, at the time of writing:
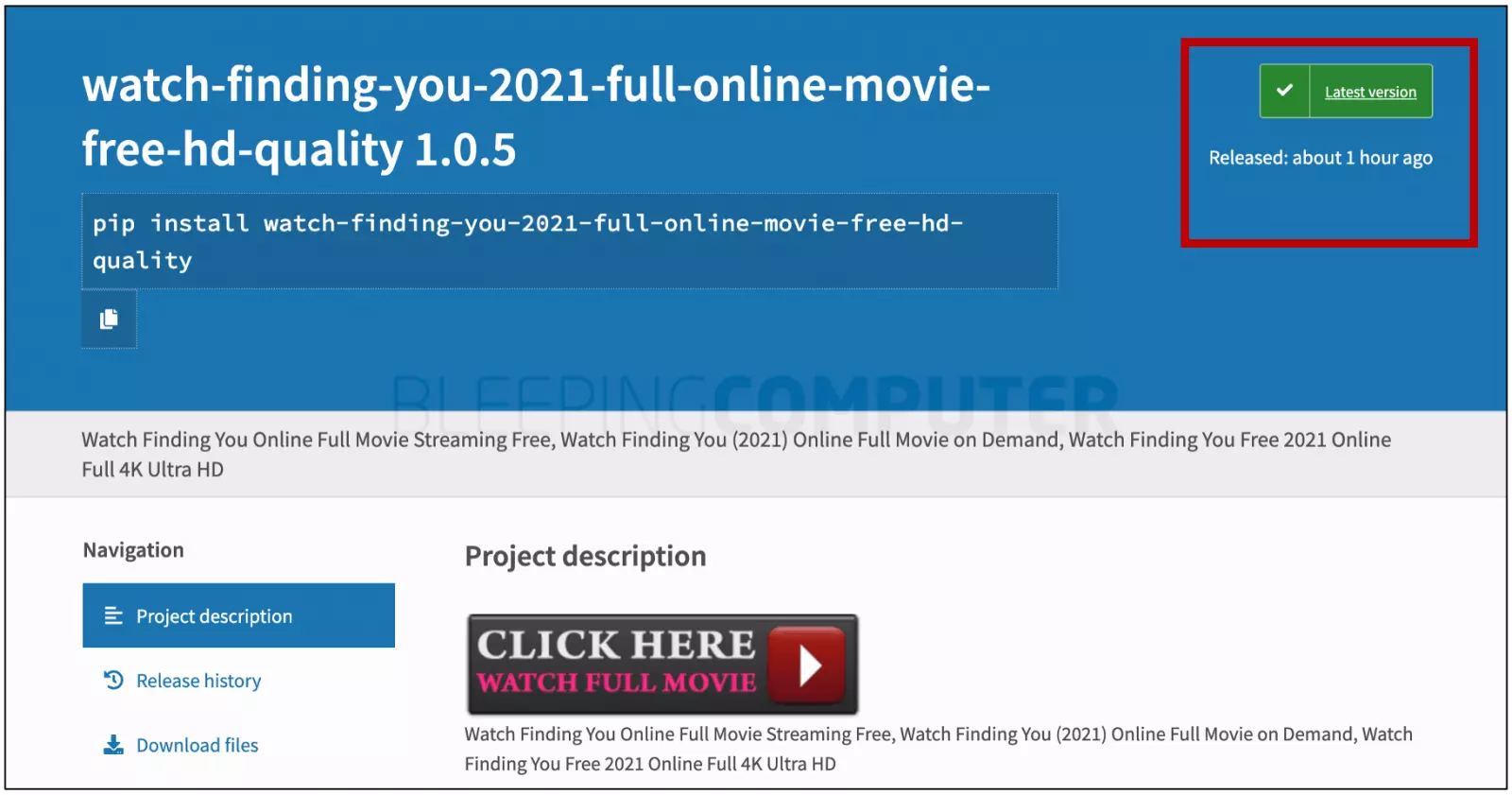
BleepingComputer also observed each of these packages were published by a distinct author (maintainer) account using a pseudonym, likely to make it hard for PyPI admins to take these packages down.
February this year, PyPI had been flooded with bogus “Discord”, “Google”, and “Roblox” keygens in a massive spam attack, as reported by ZDNet.
At the time, Ewa Jodlowska, Executive Director of the Python Software Foundation had told ZDNet that the PyPI admins were working on addressing the spam attack, however, by the nature of pypi.org, anyone could publish to the repository, and such occurrences were common.
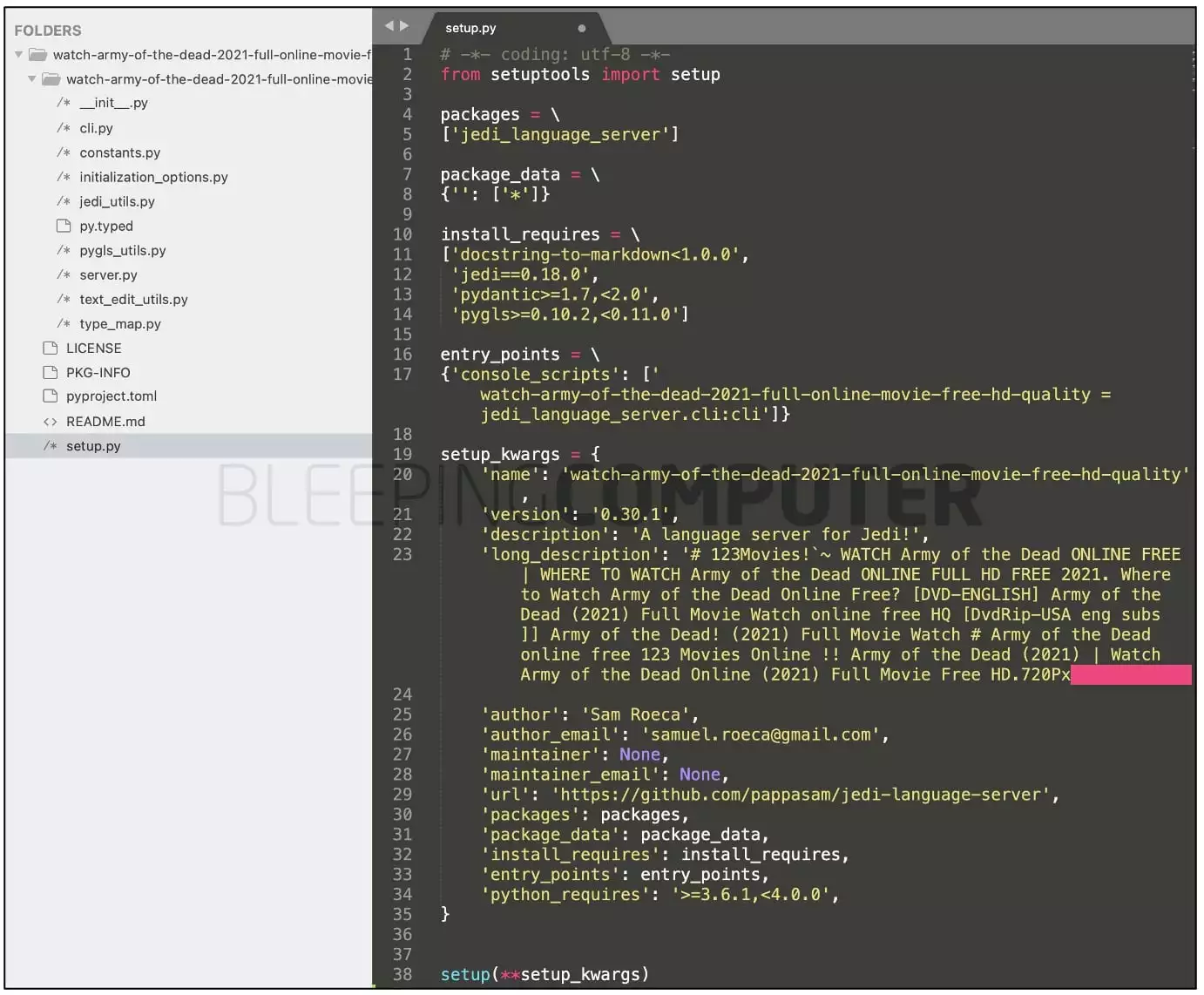
Other than containing spam keywords and links to quasi-video streaming sites, these packages contain files with functional code and author information lifted from legitimate PyPI packages.
For example, BleepingComputer observed that the spam package “watch-army-of-the-dead-2021-full-online-movie-free-hd-quality,” contained author information and some code from the legitimate PyPI package, “jedi-language-server.”
Also Read: 3 Reasons Why You Must Take a PDPA Singapore Course
As previously reported by BleepingComputer, malicious actors have combined code from legitimate packages with otherwise bogus or malicious packages to mask their footsteps, and make the detection of these packages a tad more challenging.
“It’s not uncommon in other ecosystems like npm, where you have millions of packages. Packages like these luckily are fairly easy to spot and avoid.”
“Always a good idea to investigate a package before using it. If something seems off, there’s a reason for that,” smiled Boesch.
In recent months, the attacks on open-source ecosystems like npm, RubyGems, and PyPI have escalated.
Threat actors have been caught flooding software repositories with malware, malicious dependency confusion copycats, or simply vigilante packages to spread their message.
As such, securing these repositories has turned into a whack-a-mole race between threat actors and repository maintainers.
BleepingComputer has reached out to PyPI for comment before publishing and we are awaiting their response.