KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







South Korea’s ‘Korea Atomic Energy Research Institute’ disclosed yesterday that their internal networks were hacked last month by North Korean threat actors using a VPN vulnerability.
The Korea Atomic Energy Research Institute, or KAERI, is the government-sponsored institute for the research and application of nuclear power in South Korea.
The breach was first reported earlier this month when South Korean media Sisa Journal began covering the attack. At the time, KAERI initially confirmed and then denied that the attack occurred.
In a statement and press conference held yesterday by KAERI, the institute has officially confirmed the attack and apologized for attempting to cover up the incident.
KAERI states the attack took place on June 14th after North Korean threat actors breached their internal network using a VPN vulnerability.
Also Read: Limiting Location Data Exposure: 8 Best Practices
KAERI states that they have updated the undisclosed VPN device to fix the vulnerability. However, access logs show that thirteen different unauthorized IP addresses gained access to the internal network through the VPN.
One of these IP addresses is linked to a North Korean state-sponsored hacking group known as ‘Kimsuky’ that is believed to work under the North Korean Reconnaissance General Bureau intelligence agency.
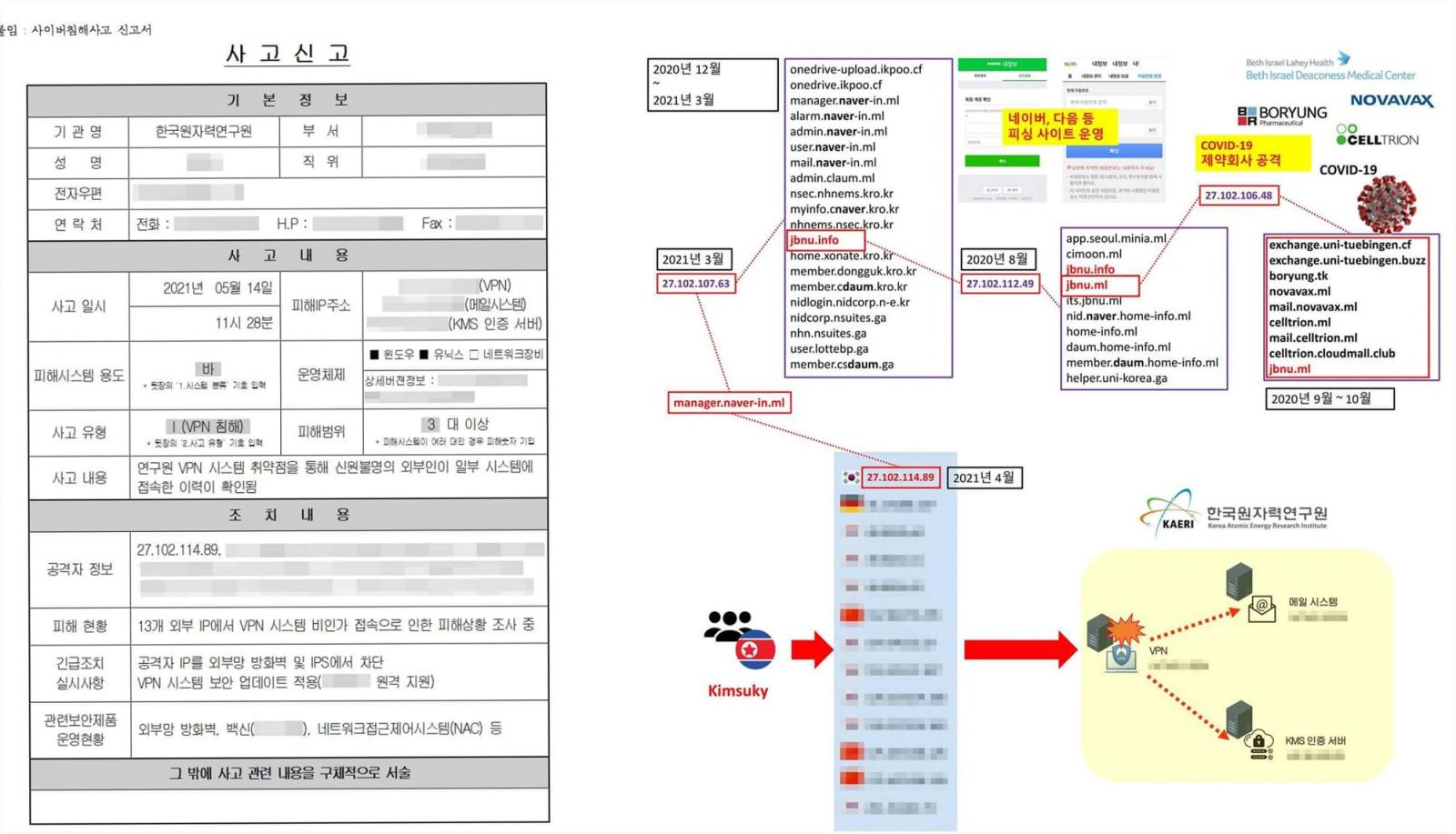
In October 2020, CISA issued an alert on the Kimsuky APT group and stated that they are “likely tasked by the North Korean regime with a global intelligence gathering mission.”
More recently, Malwarebytes has issued a report on how Kimsuky (aka Thallium, Black Banshee, and Velvet Chollima) has been actively targeting the South Korean government using the ‘AppleSeed’ backdoor in phishing attacks.
“One of the lures used by Kimsuky named “외교부 가판 2021-05-07” in Korean language translates to “Ministry of Foreign Affairs Edition 2021-05-07” which indicates that it has been designed to target the Ministry of Foreign Affairs of South Korea,” explains Malwarebytes’ report on the threat actor’s recent activities.
“According to our collected data, we have identified that it is one entity of high interest for Kimsuky.”
Also Read: 10 Practical Benefits of Managed IT Services
Malwarebytes states that Kimsuky has targeted other South Korean government agencies in recent phishing attacks, including:
KAERI states that they are still investigating the attack to confirm what information has been accessed.