KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A website named ‘SolarLeaks’ is selling data they claim was stolen from companies confirmed to have been breached in the SolarWinds attack.
Last month, it was disclosed that network management company SolarWinds suffered a sophisticated cyberattack that led to a supply chain attack affecting 18,000 customers.
According to a joint statement issued by the FBI, CISA, and the NSA, this attack was “likely” conducted by a Russian state-sponsored hacking group who wanted to steal cloud data such as email and files from its victims.
Today, a solarleaks[.]net website was launched that claims to be selling the stolen data from Microsoft, Cisco, FireEye, and SolarWinds. All of these companies are known to have been breached during the supply chain attack.
Also Read: Data Centre Regulations Singapore: Does It Help To Progress?
The website claims to be selling Microsoft source code and repositories for $600,000. Microsoft confirmed that threat actors accessed their source code during their SolarWinds breach.
[Microsoft Windows (partial) source code and various Microsoft repositories]
price: 600,000 USD
data: msft.tgz.enc (2.6G)The threat actors also claim to be selling the source code for multiple Cisco products, even more concerning, the company’s internal bug tracker.
[Cisco multiple products source code + internal bugtracker dump]
price: 500,000 USD
data: csco.tgz.enc (1.7G)In an advisory updated today, Cisco states they are aware of the SolarLeaks site and that there is no evidence that attackers stole their source code.
“Cisco is aware of this website and has no evidence at this time of any theft of intellectual property related to recent events. We are committed to transparency and should we find information our customers need to be aware of, we will share it through our established channels,” Cisco’s advisory states.
The website also claims to be selling the private red team tools, and source code that FireEye disclosed were stolen during their attack for $50,000.
[FireEye private redteam tools, source code, binaries and documentation]
price: 50,000 USD
data: feye.tgz.enc (39M)
Finally, the website sells SolarWinds source code and a dump of the customer portal for $250,000.
[SolarWinds products source code (all including Orion) + customer portal dump]
price: 250,000 USD
data: swi.tgz.enc (612M)
For $1 million, the website says you get all of the leaked data.
In style similar to the Shadow Brokers, the SolarLeaks actors state that they will be selling the stolen data in batches, and more will be released at a later date.
The solarleaks.net domain is registered through NJALLA, a known registrar used by the Russian hacking groups Fancy Bear and Cozy Bear.
When looking at the WHOIS record for solarleaks[.]net, the assigned name servers also taunt researchers with the statement “You Can Get No Info”.
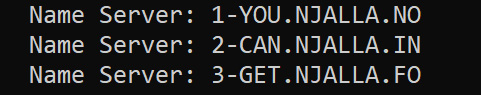
It is not confirmed if this site is legitimate and if the site owners have the data they are selling.
Also Read: What Is A Government Framework? The Importance And How It Works
Rendition Infosec’s President Jake Williams states that the sale leaning towards commercially valuable data, rather than intelligence stolen from government agencies, may indicate that this is a real group.
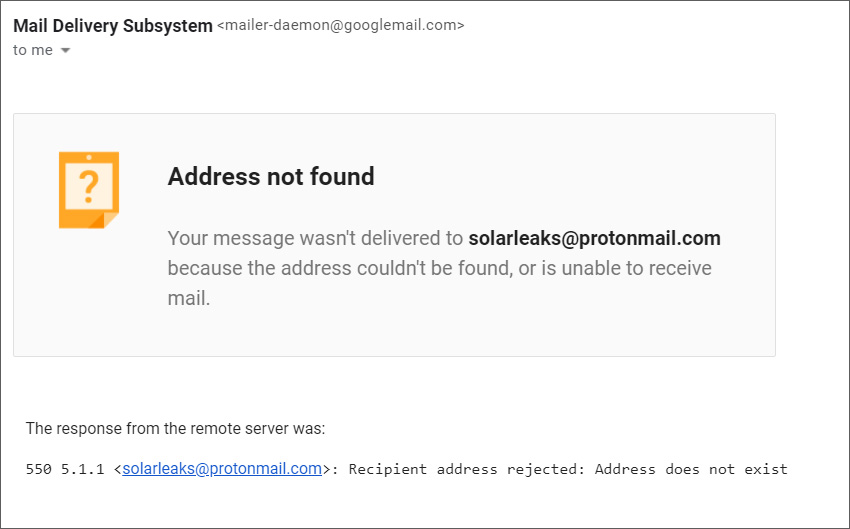
When we attempted to contact them with questions, the listed email address bounced back with an error that the email does not exist.
BleepingComputer has contacted Microsoft to confirm if they know the site and if the hackers exfiltrated their data rather than just accessed it as initially stated.
This is a developing story.