





Some Windows 10 users have issues with DNS resolution after installing the latest Windows 10 cumulative updates released this week.
As part of this week’s April 2021 Patch Tuesday, Microsoft released the Windows 10 KB5001330 & KB5001337 cumulative updates to fix various security vulnerabilities and bugs discovered in the operating system.
Since installing the updates, some corporate users have reported having issues with DNS resolution that prevent access to shared folders on servers when trying to access them by the server’s name. If attempting to access the shared folder via the server’s IP address, users can properly connect to the shared folders.
To access shared folders again, admins had to uninstall the cumulative update, which is not a good solution as it removes security fixes.
After users began reporting the issue on BleepingComputer’s forum, users determined that many affected users are using the Dentrix Dental Practice Management software in their offices.
A longstanding support recommendation for Dentrix customers to reduce network lag has been to disable multicase name resolution (LLMNR) on Windows workstations. This is done by enabling the ‘Turn off multicast name resolution’ group policy under Computer Configuration > Administrative Templates > Network > DNS Client.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
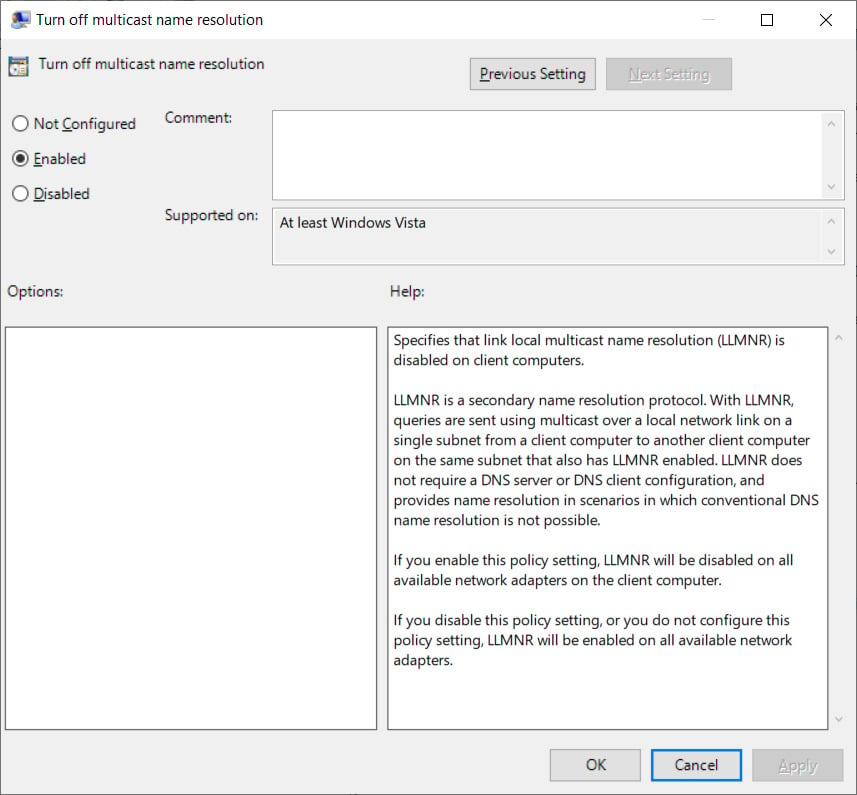
However, since installing the latest cumulative updates, this policy prevents users from accessing their shared server folders.
Dentrix has acknowledged the issue and stated that after coordinating with Microsoft, disabling this group policy is the recommended way to resolve this issue.
“After working with Microsoft, we believe that we have found a solution that allows you to keep the critical Microsoft Security Update installed. It appears that this issue can be resolved by enabling “Link Layer Multi-cast Name Resolution” (LLMNR). This is a Windows Group Policy that many users have disabled over the years. Re-enabling it seems to restore proper IP Address resolution which in turn restores connectivity to the Dentrix Database. To enable LLMNR, follow the steps below.”
To disable the policy (enable LLMNR) and fix the DNS resolution issues, the recommended steps are:
Dentrix customers do not see this as an adequate solution as LLMNR could cause lag while using the software. Instead, they recommend users add the affected server’s name and IP address to the HOSTS file, which seems to fix the issue.
“Enabling Multicast is definitely not an option for Dentrix due to slowness.
Microsoft needs to release a fix asap.
Best resolution we have found so far is the host file fix, the DNS service fix hasn’t fixed any of them yet for us but was reported by someone else as a fix.”
– a Dentrix customer posted to our forums.
This bug is not related solely to Dentrix users but instead to whoever has LLMNR disabled, which for the most part, has been Dentrix customers who were told to disable it.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
While it is unknown what caused this bug, Microsoft fixed two DNS vulnerabilities [1, 2] this month that may have contributed to this abnormal behavior.
BleepingComputer has contacted Microsoft regarding this bug but has not heard back.