KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A trick has been discovered that prevents your device from being taken over by vulnerable Windows applications when devices are plugged into your computer.
Last month, researchers detailed how simply plugging in a device in Windows may also install a vendor’s application that allows regular users to quickly gain SYSTEM privileges, the highest user privilege level in Windows.
For example, when users plugged in a Razer USB mouse, Windows would automatically install its driver and the Razer Synapse software.
However, since Windows started the software’s installation using a process with SYSTEM privileges, the Razer Synapse software also ran with SYSTEM privileges.
During the Razer Synapse installation, you could specify a different folder to install the program, which would open a ‘Choose a Folder’ dialog.
However, when this dialog is open, it is possible to open a PowerShell console, which would also open with the SYSTEM privileges of the Razer Synapse installer.
For those not familiar with SYSTEM privileges, they are the highest user rights available in Windows and allow you to perform any command in the operating system.
Also Read: Data Protection Policy: 8 GDPR Compliance Tips
Using these bugs, users with little privileges on a Windows device could easily take complete control over it by simply plugging in a $20 USB mouse.
This vulnerability was discovered in apps known as “co-installers” and, since the first one was spotted, other researchers found more devices that may allow local privilege elevation, including SteelSeries devices.
When hardware developers submit drivers to Microsoft for distribution through Windows, they can configure device-specific co-installers that will be executed after Windows Plug-and-Play installs the driver.
These co-installers can be used to configure device-specific Registry keys, download and install other applications, or perform other necessary functions for the device to work correctly.
Through the co-installer feature, Razer, Synapse, and other hardware manufacturers can install their configuration utilities when their USB devices are plugged into a computer.
As first discovered by Will Dormann, a vulnerability analyst for CERT/CC, it is possible to configure a Windows Registry value that blocks co-installers from being installed during the Plug-and-Play feature.
To do this, open the Registry Editor and navigate to the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Device Installer Registry key. Under that key, add a DWORD-32 value named DisableCoInstallers and set it to 1, as shown below.
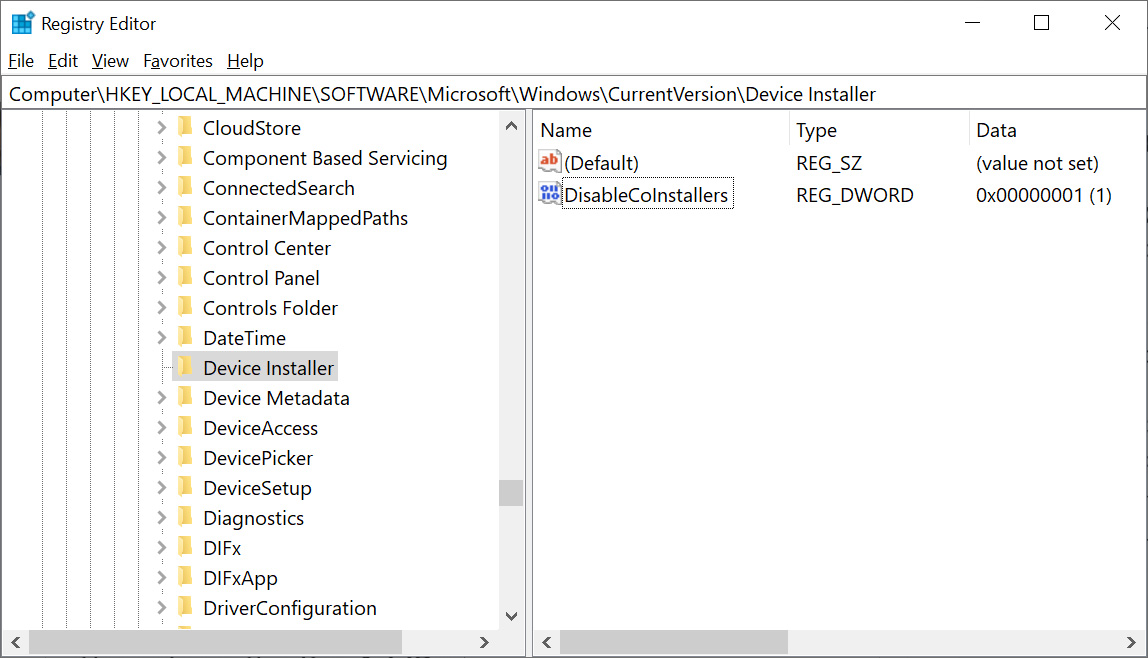
Once enabled, Windows will block co-installers from being installed when you plug an associated USB device into your computer.
It is important to note that making this change will block a device’s configuration software from automatically being installed. Instead, you will need to download and install it from the vendor’s site manually.
Also Read: Don’t Be Baited! 5 Signs of Phishing in Email
However, the inconvenience is worth the added security received by blocking the installation of potentially exploitable applications during the Windows Plug-and-Play process.