



Web browser vendors are planning to block a new attack technique that would allow attackers to bypass a victim’s NAT, firewall, or router to gain access to any TCP/UDP service hosted on their devices.
The attack method, dubbed NAT Slipstreaming, was discovered by security researcher Samy Kamkar and it requires the victims to visit the threat actor’s malicious website (or a site with maliciously crafted ads).
To expose hosted services, the attack abuses certain NAT devices scanning port 5060 to create port forwarding rules when detecting maliciously-crafted HTTP requests camouflaged as valid SIP requests.
Kamkar also provides proof-of-concept exploit code to demonstrate the validity of this newly disclosed NAT/firewal/router bypass technique.
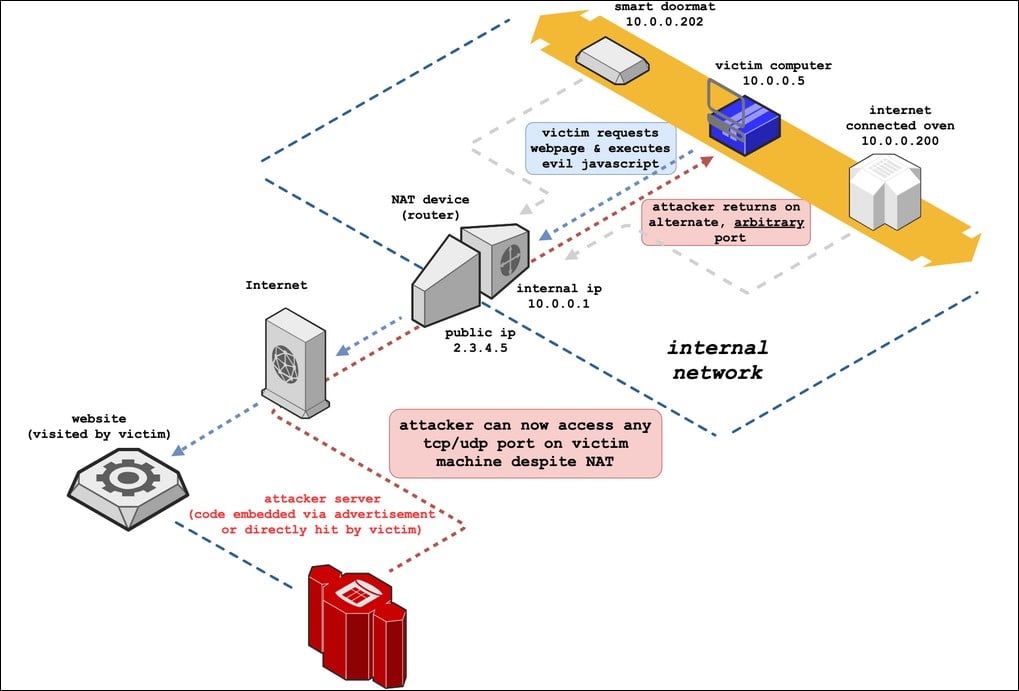
“This attack takes advantage of arbitrary control of the data portion of some TCP and UDP packets without including HTTP or other headers; the attack performs this new packet injection technique across all major modern (and older) browsers, and is a modernized version to my original NAT Pinning technique from 2010 (presented at DEFCON 18 + Black Hat 2010). Additionally, new techniques for local IP address discovery are included,” Kamkar explained.
Also Read: IT Governance Framework PDF Best Practices And Guidelines
“This attack requires the NAT/firewall to support ALG (Application Level Gateways), which are mandatory for protocols that can use multiple ports (control channel + data channel) such as SIP and H323 (VoIP protocols), FTP, IRC DCC, etc.”
To block such attacks, web browser vendors are planning to block the 5060 and 5061 TCP ports used in this attack by adding them to the restricted list.
“As a workaround for the ‘Slipstream’ NAT bypass attack, we will be blocking HTTP and HTTPS connections to the SIP ports 5060 and 5061,” Chromium developer Adam Rice says. “This will mean that connections to servers on those ports will fail.”
Once the ports will be added to the restricted ports list, Rice expects some impact to be observed by browser users including:
At the moment, development teams behind Firefox, Safari, and Blink (the Chromium rendering engine) have expressed their intent in implementing the mitigation needed to block NAT Slipstreaming attacks.
Also Read: EU GDPR Articles: Key For Business Security And Success