KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A vulnerability exists in certain implementations of Bluetooth 4.0 through 5.0 which allows an attacker to overwrite or lower the strength of the pairing key, giving them access to authenticated services.
The bug was discovered independently by two teams of academic researchers and received the name BLURtooth. It affects “dual-mode” Bluetooth devices, like modern smartphones.
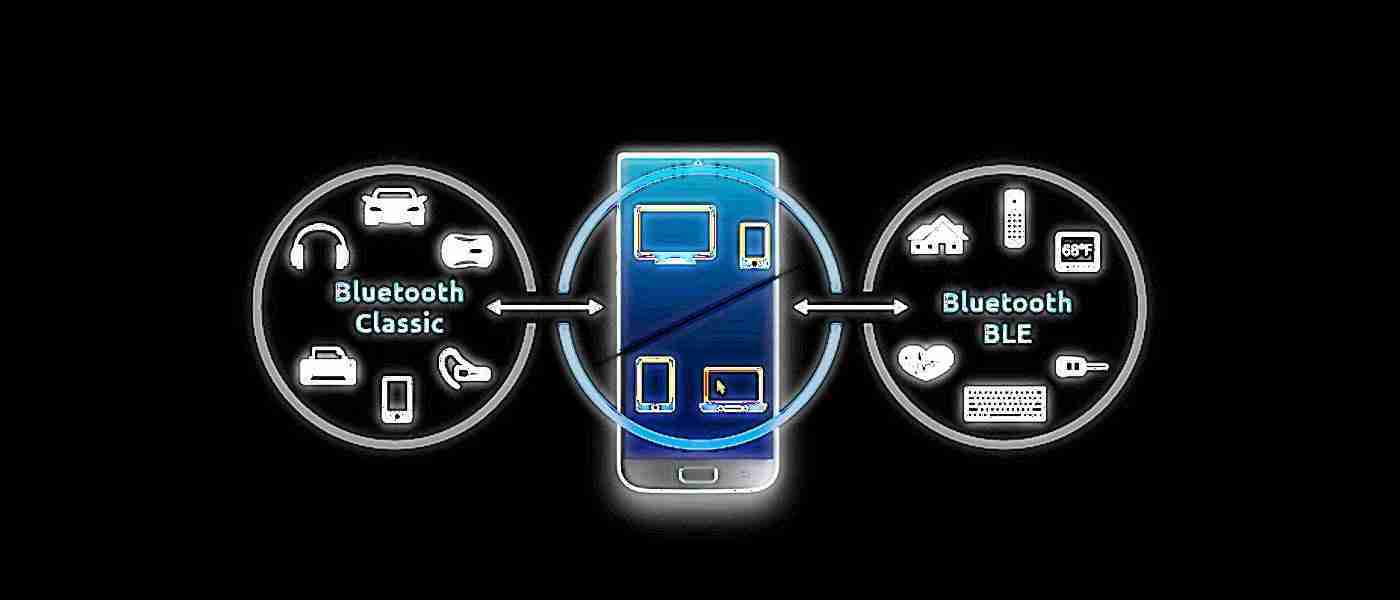
An attacker can exploit BLURtooth on devices that support both Bluetooth Classic and Low Energy (LE) data transport methods and use Cross-Transport Key Derivation (CTKD) for pairing with each other.
The former mode, needed in applications that require a higher throughput at a constant rate (e.g. headphones), is technically referred to as Basic Rate/Enhanced Data Rate (BR/EDR).
Bluetooth LE is less data-intensive and fits applications where information is needed in short bursts, as is the case with smaller sensors, which also conserves energy.
A security advisory from Carnegie Mellon CERT Coordination Center explains that when CTKD is used for pairing dual-mode Bluetooth devices, the procedure happens only once over one of the two data transport methods.
In the process, Long Term Keys / Link Keys (LTK/LK) are generated and they can be overwritten for cases where the transport enforces a higher level of security, which is what a BLUR attack takes advantage of.
“When this results in the reduction of encryption key strength or the overwrite of an authenticated key with an unauthenticated key, an attacker could gain additional access to profiles or services that are not otherwise restricted” – Carnegie Mellon CERT CC
Also read: 10 Government Data Leaks In Singapore: Prevent Cybersecurity
The Bluetooth Special Interest Group (SIG), the organization that oversees the development of Bluetooth standards, also published an advisory describing an attack scenario and the result of successful exploitation.
An attacker in the Bluetooth proximity of a vulnerable target device could spoof the identity of a paired device to overwrite the original key and access authenticated services.
“If a device spoofing another device’s identity becomes paired or bonded on a transport and CTKD is used to derive a key which then overwrites a pre-existing key of greater strength or that was created using authentication, then access to authenticated services may occur” – Bluetooth SIG advisory
BLURtooth is also suitable for man-in-the-middle (MitM) type of attacks, with the attacker sits between two vulnerable devices that had been linked using authenticated pairing.
The vulnerability was discovered and reported independently by researchers at Purdue University and École Polytechnique Fédérale de Lausanne (EPFL).
The solution from Bluetooth SIG for vendors with potentially vulnerable implementations is to introduce the restrictions on Cross-Transport Key Derivation that are required in Bluetooth Core Specification versions 5.1 and later.
A list of vendors with vulnerable implementations impacted by BLURtooth available in CERT CC’s advisory shows only the Bluetooth SIG organization with the status “affected,” many others being listed with the status “unknown.” The list will change as implementations from other vendors are confirmed to be affected or not.
Also read: How To Anonymised The Data: What Are The Importance Of This?