





Software developed by data extraction company Cellebrite contains vulnerabilities that allow arbitrary code execution on the device, claims Moxie Marlinspike, the creator of the encrypted messaging app Signal.
Cellebrite products are commonly used by police and governments to unlock iOS and Android phones and extract data on them. Last December, the company announced that its Physical Analyzer also gave access to data from Signal.
In a blog post earlier today, Marlinspike, a cryptographer and security researcher, said that Cellebrite’s software works by parsing data that comes from an untrusted source.
This means that it accepts input that may not be formatted correctly, which could trigger a memory corruption vulnerability that leads to code execution on the system.
Because of this risk, one would assume that the developer was sufficiently careful to set up protections or use code that is not susceptible to vulnerabilities.
“Looking at both UFED and Physical Analyzer, though, we were surprised to find that very little care seems to have been given to Cellebrite’s own software security. Industry-standard exploit mitigation defenses are missing, and many opportunities for exploitation are present”
– Moxie Marlinspike
Furthermore, the researcher found that Cellebrite’s software had outdated open-source code that had not been updated in almost a decade, despite security updates being available.
Also Read: Compliance Course Singapore: Spotlight On The 3 Offerings
Exploring possibilities for exploitation, Marlinspike found that he could run arbitrary code on a Cellebrite machine when it parsed a specially formatted, yet non-offensive file on a device it scanned.
“For example, by including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures”
– Moxie Marlinspike
The researcher provides proof of successful exploitation of UFED, Cellebrite’s product for collecting evidence from sources ranging from mobile devices and apps to public-domain social media services.
The payload uses the MessageBox Windows API to deliver a message that is iconic in hacker culture:
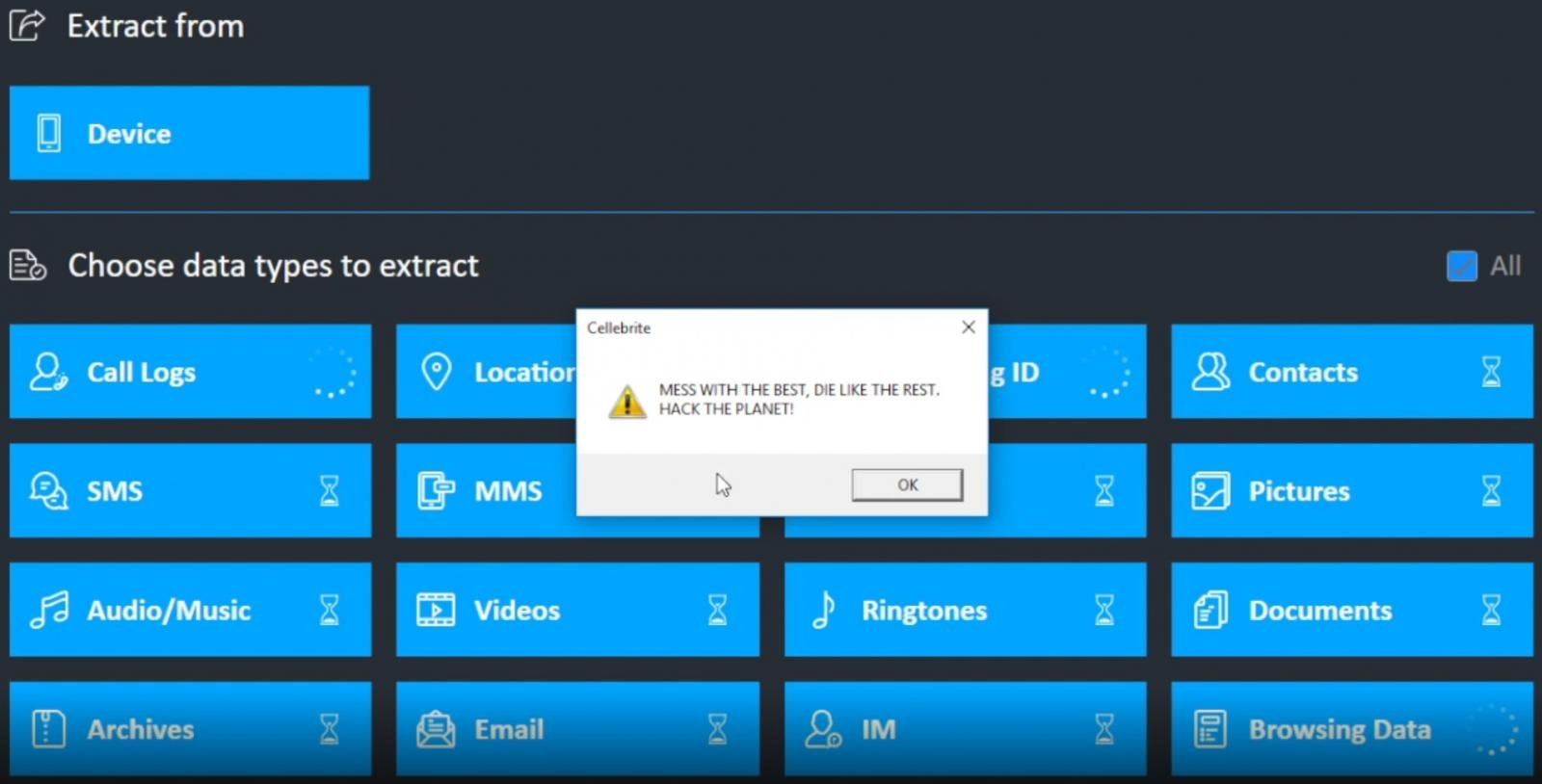
Another interesting point is that Marlinspike said in the installer for the Packet Analyzer he found MSI packages with a digital signature from Apple.
These appear extracted from the Windows installer for iTunes 12.9.0.167 and contain DLL files that help Cellebrite’s program interact with iOS devices and extract data from them.
While the announcement is far from the protocol of responsible disclosure, Marlinspike says that he will provide Cellebrite the specifics of the vulnerabilities if the company does the same for all the security issues they exploit for physical extraction services “now and in the future.”
In seemingly “completely unrelated” news, Marlinspike says that future versions of Signal will add to the app storage files that are “aesthetically pleasing.”
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
These files, add nothing to Signal’s functionality and will not interact with the app, “but they look nice, and aesthetics are important in software.” If these are formatted in a special way, Cellebrite’s customers will likely have a hard time demonstrating the integrity of the scan reports from devices where Signal is installed.