KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Ransomware Task Force, a public-party coalition of more than 50 experts, has shared a framework of actions to disrupt the ransomware business model.
One of the priority recommendations refers to better regulating the cryptocurrency sector, which plays an essential part in obfuscating the threat actors and making ransomware attacks a lucrative endeavor.
In a document released today, the Institute for Security and Technology (IST) provides a list of 48 actions that governments and leaders in the private sector can adopt to seriously curb the ransomware threat.
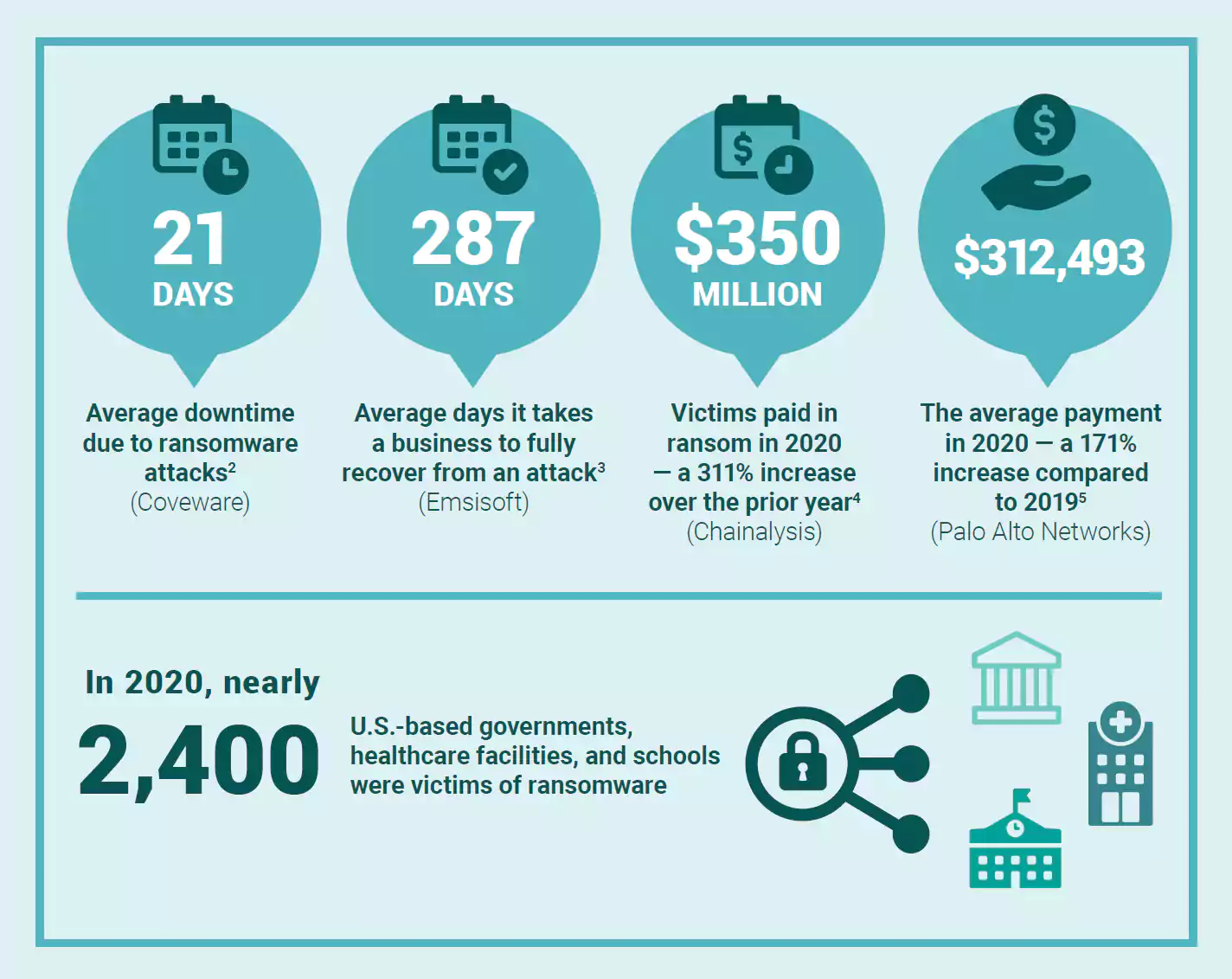
Ransomware activity has grown constantly over the past years as cybercriminals increased their attacks to targets in both the private and the public sector (including healthcare and education branches).
The ransom demands last year averaged hundreds of thousands of U.S. dollars but the highest payouts were between $1 and $2 million for some ransomware gangs.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
Priority recommendations:
Some of the rules developed within the Ransomware Task Force (RTF) require Congressional help to modernize some cybersecurity laws, such as the Cybersecurity Information Sharing Act of 2015 and the Computer Fraud and Abuse Act (CFAA).
The changes should incentivize ransomware victims to share anonymously ransomware payment details (cryptocurrency wallet addresses, transaction hashes, ransom notes).
They should also allow a broader set of actions to parties dealing with a ransomware incident “when acting in good faith without fear of legal liability.”
“The strategic framework is organized around four primary goals: to deter ransomware attacks through a nationally and internationally coordinated, comprehensive strategy; to disrupt the business model and reduce criminal profits; to help organizations prepare for ransomware attacks; and to respond to ransomware attacks more effectively” – Ransomware Task Force
Also Read: Personal Data Websites: 3 Things That You Must Be Informed
RTF’s recommendations are designed for long-term effect once adopted and are likely to improve the cybersecurity posture of organizations. They can also tighten the collaboration between multiple actors dedicated to keeping the world safe from cyber threats.