KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







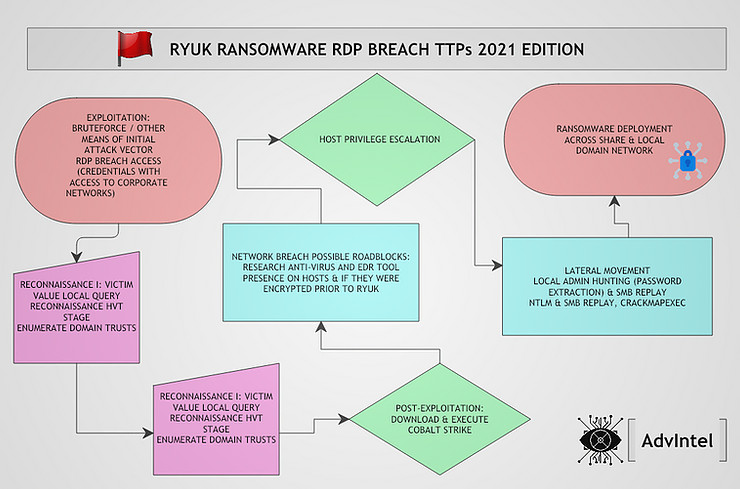
Recent attacks from Ryuk ransomware operators show that the actors have a new preference when it comes to gaining initial access to the victim network.
The trend observed in attacks this year reveals a predilection towards targeting hosts with remote desktop connections exposed on the public internet.
Furthermore, using targeted phishing emails to deliver the malware continues to be a favored initial infection vector for the threat actor.
Security researchers from the threat intelligence boutique Advanced Intelligence (AdvIntel) observed that Ryuk ransomware attacks this year relied more often on compromising exposed RDP connections to gain an initial foothold on a target network.
The actors have been running “large-scale brute force and password spraying attacks against exposed RDP hosts” to compromise user credentials.
Another vector for initial compromise was spear phishing and the use of the BazaCall campaign to distribute malware through malicious call centers that targeted corporate users and directed them to weaponized Excel documents.
AdvIntel researchers say that the Ryuk attackers ran reconnaissance on the victim in two stages. Once, to determine the valuable resources on the compromised domain (network shares, users, Active Directory Organization Units).
The second time, the objective is to find information on the company’s revenue to set a ransom amount that the victim can afford to pay to recover systems.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
To enumerate the active directory information, Ryuk ransomware operators rely on the tried and tested AdFind (AD query tool) and the post-exploitation tool Bloodhound that explores relationships in an Active Directory (AD) domain to find attack paths.
Getting financial details about the victim relies on open-source data. AdvIntel says that the actors search on services like ZoomInfo for information about the company’s recent mergers and acquisitions and other details that can increase the profitability of the attack.
Additional reconnaissance is carried out using the Cobalt Strike post-exploitation tool that’s become a standard in most ransomware operations and scans that reveal the security products like antivirus and endpoint detection response (EDR) defending the network.
The researchers say that the actor engages other cybercriminals to learn about the defenses on a network they attack to find a way to disable them.
Among the newer techniques the researchers saw in Ryuk ransomware attacks was the use of KeeThief, an open-source tool for extracting credentials from KeePass password manager.
KeeThief works by extracting key material (e.g. master password, key file) from the memory of a running KeePass process with an unlocked database.
Vitali Kremez, the CEO of AdvIntel, told BleepingComputer that the attackers used KeeThief to bypass EDR and other defenses by stealing the credentials of a local IT administrator with access to EDR software.
Another tactic was to deploy a portable version of Notepad++ to run PowerShell scripts on systems with PowerShell execution restriction, Kremez says.
According to AdvIntel, Ryuk ransomware attacks this year are exploiting two vulnerabilities to increase their permissions on a compromised machine. Both flaws are older and patches are available for them:
Another observation from AdvIntel is that a recent Ryuk ransomware attack used the open-source CrackMapExec penetration tool to extract admin credentials and move laterally on the victim network.
“Once actors have successfully compromised a local or domain admin account, they distribute the Ryuk payload through Group Policy Objects, PsExec sessions from a domain controller, or by utilizing a startup item in the SYSVOL share”
– Advanced Intelligence
The researchers recommend organizations the following risk mitigation steps:
Ryuk has been in the ransomware business for a long time and is known as a tough negotiator. It is estimated that they collected at least $150 million in ransoms, with one victim ending up paying $34 million to restore its systems.
Also Read: Data Protection Officer Singapore | 10 FAQs
Given these figures, it makes sense that the actor switched to new tactics, techniques, and procedures to stay ahead of the game and keep the lucrative ransomware business running.