KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Russian state-sponsored hackers known as the Turla APT group have been using new malware over the past year that acted as a secondary persistence method on compromised systems in the U.S., Germany, and Afghanistan.
Named TinyTurla due to its limited functionality and uncomplicated coding style, the backdoor could also be used as a stealthy second-stage malware dropper.
Security researchers at Cisco Talos say that TinyTurla is a “previously undiscovered” backdoor from the Turla APT group that has been used since at least 2020, slipping past malware detection systems particularly because of its simplicity.
“This malware specifically caught our eye when it targeted Afghanistan prior to the Taliban’s recent takeover of the government there and the pullout of Western-backed military forces” – Cisco Talos
Forensic evidence indicates that Turla APT (advanced persistent threat) actors have been targeting the previous Afghan government with the newly discovered backdoor.https://www.ad-sandbox.com/static/html/sandbox.html
However, Cisco Talos’ telemetry data, which is how the researcher discovered the new malware, shows that TinyTurla has also been deployed on systems in the U.S. and Germany.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
Linking the TinyTurla backdoor to the Russian state hackers was possible because the threat actor used the same infrastructure seen in other attacks attributed to the Turla APT group.
“One public reason why we attributed this backdoor to Turla is the fact that they used the same infrastructure as they used for other attacks that have been clearly attributed to their Penguin Turla infrastructure” – Cisco Talos
In research published today, the researchers say that the hackers used the malware “as a second-chance backdoor to maintain access to the system” if the primary access tool got removed.
Compared to a full-fledged backdoor, TinyTurla’s functionality is limited to essential tasks that include downloading, uploading, and executing files.
Looking at the codes received from the command and control (C2) server, the researchers collected the following commands:
Since the malware was found through telemetry collection, it remains unknown how it landed on victim systems. Cisco Talos provides some technical details, though, in a blog post today.
The threat actor used a .BAT file to install the backdoor. It comes disguised as a DLL file (w64time.dll) to impersonate w32time.dll, a legitimate Windows Time Service.
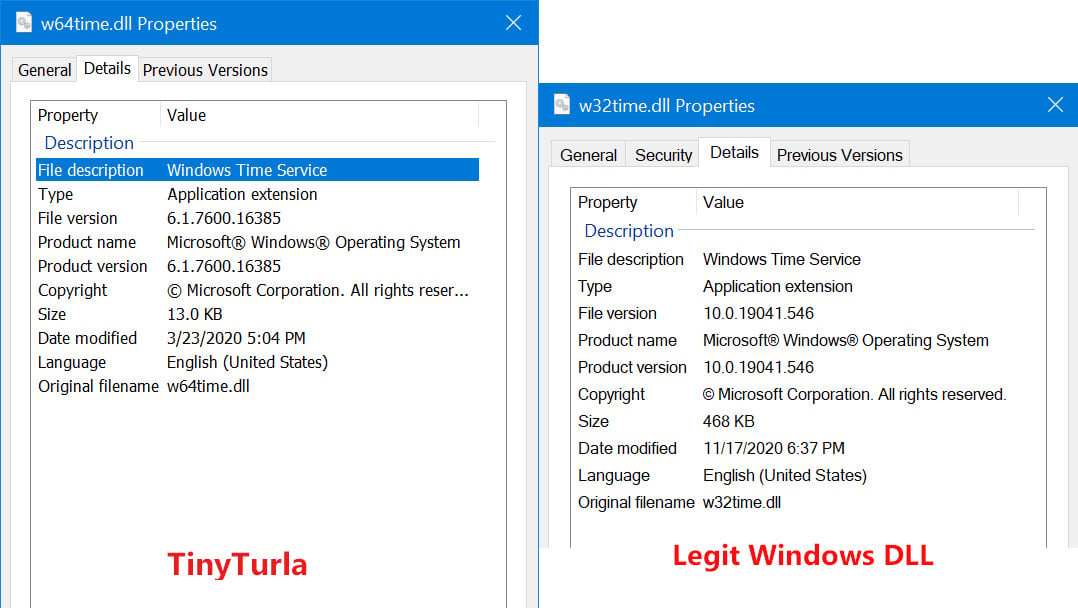
Camouflaging as a service is what made TinyTurla evade detection because the large number of legitimate services active in the background makes it difficult for admins to check if a malicious one hides among them.
The analysis of the malware showed that it is contacting the C2 server every five seconds, which creates an anomaly in the network traffic that administrators should investigate.
Despite this tell, though, Turla was able to use this backdoor for almost two years, the researchers say.
TinyTurla’s simplicity contrasts Turla’s typical tactics, which include covert exfiltration methods using hijacked satellite connections, watering hole attacks, rootkits, and stealthy channel backdoors.
The APT group is referred to by various names (e.g. Waterbug, Venomous Bear, Iron Hunter, Krypton, Snake, Uroburos) in the infosec industry.
It has been targeting victims across a wide range of industries for espionage and data theft since at least 2014.
The early history of the group may go as far back as 1996, though, connected to the Moonlight Maze cyberespionage operation, a massive data breach targeting classified information on systems from NASA, the Pentagon, military contractors, and multiple government agencies in the U.S.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
According to investigators, had the stolen documents been printed, the stack would be three times taller than the Washington Monument.
Almost 20 later, researchers from Kaspersky Lab and King’s College London found a link between Turla and malware used in the Moonlight Maze attack.