





A new phishing campaign dubbed MirrorBlast is deploying weaponized Excel documents that are extremely difficult to detect to compromise financial service organizations
The most notable feature of MirrorBlast is the low detection rates of the campaign’s malicious Excel documents by security software, putting firms that rely solely upon detection tools at high risk.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
The developers of these malicious documents have made considerable effort to obfuscate malicious code, achieving zero detections on VirusTotal.
However, these optimized documents have drawbacks that the actors are apparently willing to accept as trade-offs. Most notably, the macro code can only be executed on a 32-bit version of Office.
If the victim is tricked into opening the malicious document and “enable content” in Microsoft Office, the macro executes a JScript script which downloads and installs an MSI package.”
Prior to that though, the macro performs a basic anti-sandboxing check on whether the computer name is equal to the user domain, and if the username is equal to ‘admin’ or ‘administrator’.
According to researchers at Morphisec who analyzed several samples of the dropped MSI package, it comes in two variants, one written in REBOL and one in KiXtart.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
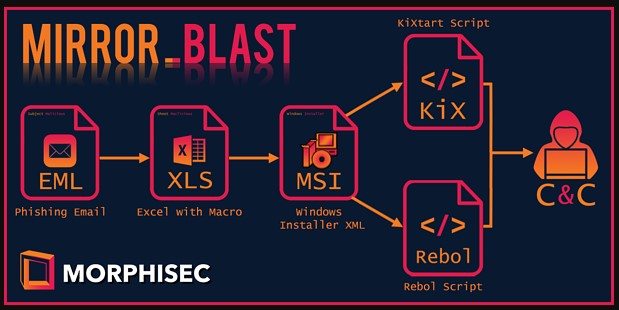
The REBOL variant, which is base64 encoded, begins by exfiltrating information like the username, OS version, and architecture.
Next, it waits for a C2 command that initiates a Powershell which will fetch the second stage. The researchers weren’t able to retrieve that stage though, so its functions are unknown.
The KiXtart payload is also encrypted and also attempts to exfiltrate basic machine information to the C2, including the domain, computer name, user name, and process list.
The actors behind the campaign appear to be ‘TA505,’ an active Russian threat group that has a long history of creativity in the way they lace Excel documents in malspam campaigns.
Morphisec was able to link the actors with the MirrorBlast campaign thanks to infection chain similarities with past operations, the abuse of OneDrive, the particularities in domain naming methods, and the existence of an MD5 checksum mismatch that points to a 2020 attack launched by TA505.
TA505 is a highly sophisticated threat actor that is known for a wide-range of malicious activity over the years.
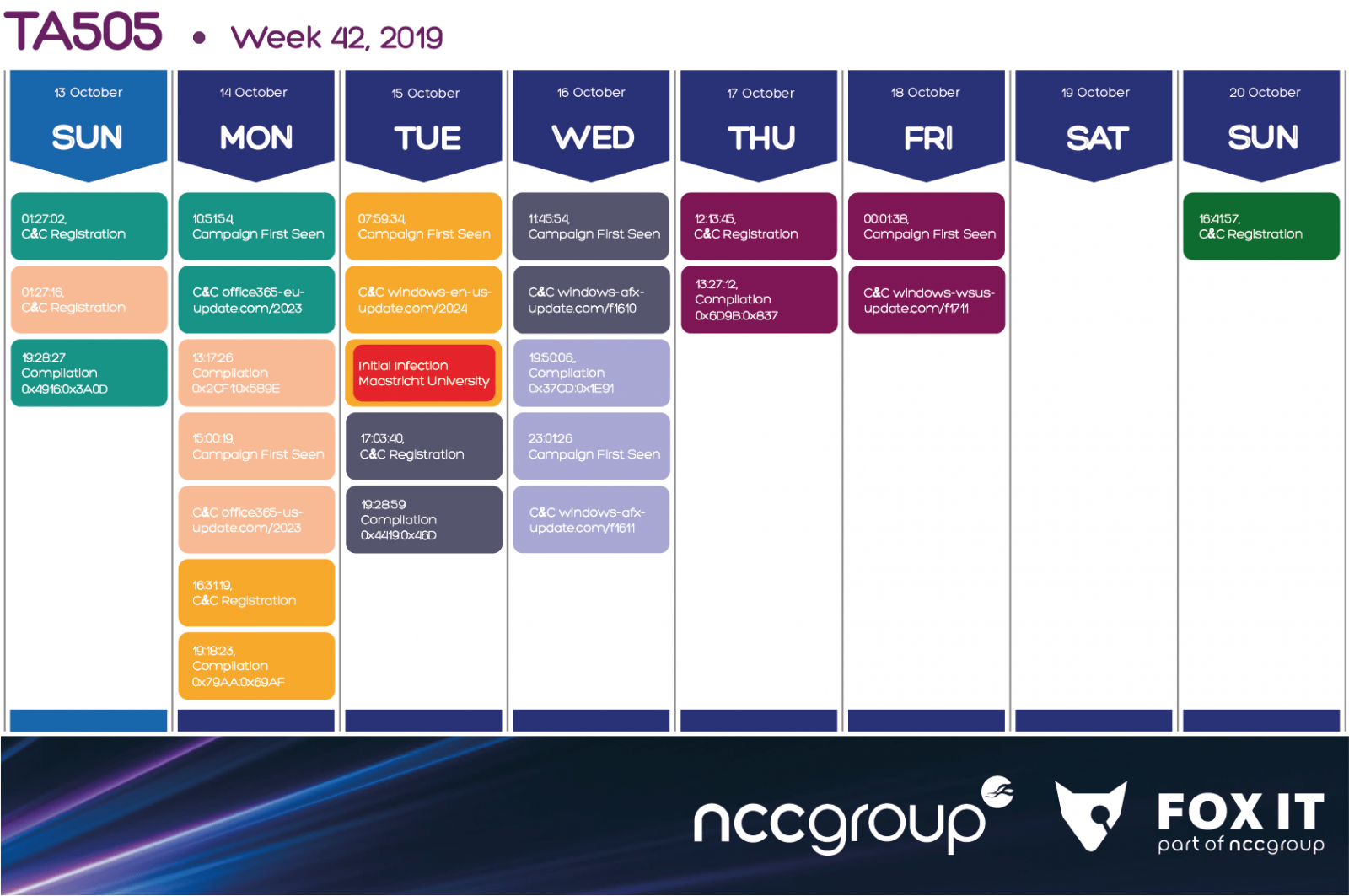
An NCCGroup analysis on the actor’s work schedule reflects an organized and well-structured group that utilizes zero-day vulnerabilities and a variety of malware strains in its attacks. This includes the deployment of Clop ransomware in double-extortion attacks.
TA505 is also attributed to numerous attacks using a zero-day vulnerability in Accenture FTA secure file sharing devices to steal data from organizations.
The threat actors then attempted to extort the companies by demanding $10 million ransoms to not publicly leak the data on their Clop data leak site.
As such, the IT teams at the financial organizations targeted by the MirrorBlast campaign cannot afford to lower their shields even for a moment.