KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







REvil ransomware has set a price for decrypting all systems locked during the Kaseya supply-chain attack. The gang wants $70 million in Bitcoin for the tool that allows all affected businesses to recover their files.
The attack on Friday propagated through Kaseya VSA cloud-based solution used by managed service providers (MSPs) to monitor customer systems and for patch management.
Customers of multiple MSPs have been impacted by the attack, REvil ransomware encrypting networks of at least 1,000 businesses across the world.
In a post on their leak site, the threat actor says that they locked more than a million systems and are willing to negotiate for a universal decryptor, starting from $70 million.
Also Read: How to Choose a Penetration Testing Vendor
/REvilKaseya70Mil.jpg)
This is the highest ransom demand to date, the previous record also belonging to REvil, asking $50 million after attacking Taiwanese electronic and computer maker Acer.
Previously, REvil ransomware asked $5 million from MSPs for a decryption tool and a $44,999 ransom from their customers.
However, the gang used multiple extensions when encrypting the files, and the $44,999 demand was for unlocking files with the same extension, as the negotiations with the victims show.
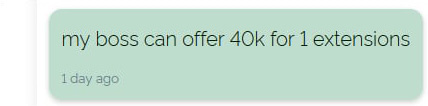
For victims with locked files that have multiple extensions following the REvil ransomware encryption, the gang’s demand can be as high as $500,000, BleepingComputer learned.
REvil was able to pull this massive attack by exploiting a zero-day vulnerability in Kaseya VSA server that had been reported privately and was in the process of being fixed.
It turns out that researchers from the Dutch Institute for Vulnerability Disclosure (DIVD) reported the bug and that Kaseya had created a patch that was being validated, the stage before delivering it to customers.
“Also, partial patches were shared with us to validate their effectiveness. During the entire process, Kaseya has shown that they were willing to put in the maximum effort and initiative into this case both to get this issue fixed and their customers patched” – Victor Gevers, DIVD Chair
However, it appears that REvil affiliates knew about the vulnerability, too, and exploited it before Kaseya could push the fix to customers.
The full extent of this REvil ransomware attack remains unclear at the moment but the incident has triggered strong reactions from law enforcement, with the FBI announcing that they are working with CISA during their investigation.
Also Read: The 5 Phases of Penetration Testing You Should Know
U.S. President Biden also addressed the Kaseya supply-chain attack, directing intelligence agencies to investigate the hack that affected hundreds of U.S. businesses.