KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A researcher has managed to crack 70% of a 5,000 WiFi network sample in his hometown, Tel Aviv, to prove that home networks are severely unsecured and easy to hijack.
CyberArk security researcher Ido Hoorvitch first wandered in the city center with WiFi sniffing equipment to gather a sample of 5,000 network hashes to use in the research.
Next, the researcher exploited a flaw that allows the retrieval of a PMKID hash, usually generated for roaming purposes.
To gather PMKID hashes, Hoorvitch used a $50 network card that can act as a monitor and a packet injection tool and sniffed with WireShark on Ubuntu, both free software.
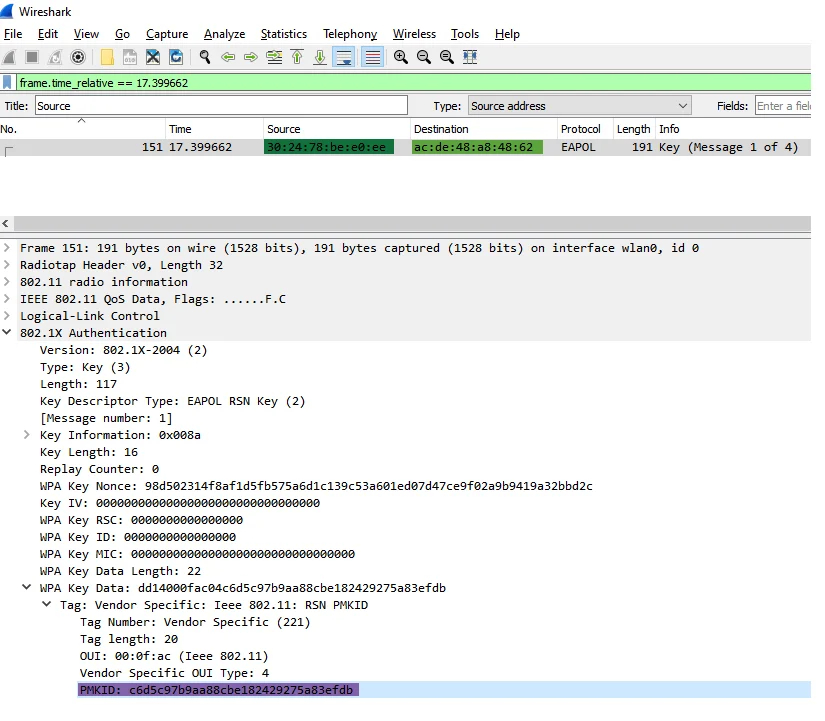
The PMKID hash comprises the network’s SSID, the passphrase, the MAC address, and a static integer.
.jpg)
Using a previously discovered method by Jens “atom” Steube’s (Hashcat’s lead developer), the researcher gathered PMKIDs that would be cracked to derive the password.
“Atom’s technique is clientless, making the need to capture a user’s login in real time and the need for users to connect to the network at all obsolete,” explains Hoorvitch in the report.
“Furthermore, it only requires the attacker to capture a single frame and eliminate wrong passwords and malformed frames that are disturbing the cracking process.”
At first, “mask attacks” were launched to determine if any users had set their cellphone number as their WiFi password, which is common in Israel.
Cracking such passwords would be a case of calculating all number options for Israeli phone numbers, and that’s ten digits starting with 05, so it’s only eight digits.
Using a standard laptop, the researcher cracked 2,200 passwords at an average speed of nine minutes per password using this method.
The next phase of the attack involved a standard dictionary attack, using the ‘Rockyou.txt’ dictionary.
This led to quickly cracking another 1,359 passwords, with most of them using only lower-case characters.
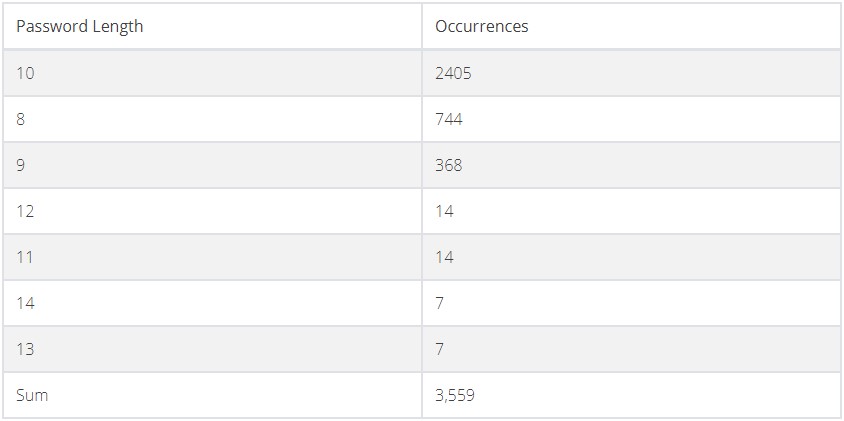
By following this simple and inexpensive cracking method, the researcher cracked roughly 70% of the passwords for the sampled WiFi networks.
The research shows that most people are not setting a strong password for their WiFi networks even though they are at risk of being hacked.
If your WiFi password is hacked, anyone can access your home network, change your router’s settings, and potentially pivot to your personal devices by exploiting flaws.
Good passwords should be at least ten characters long and have a mix of lower case and upper case letters and symbols and digits.
If you want a password that is easier to remember, you can try a three-word random passphrase that contains numeric or special symbols as separators.
Finally, if your router supports roaming or WPS, disable them both, as it trades security for convenience.