KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A crew of highly-skilled hackers specialized in corporate espionage has resumed activity, one of their victims this year being a large wholesale company in Russia.
Tracked as RedCurl, the group attacked the Russian business twice this year, each time using carefully constructed spear-phishing emails with initial-stage malware.
Active since 2018, RedCurl is responsible for at least 30 attacks against businesses in Russia (18 of them), Ukraine, Canada, Norway, the UK, and Germany, the latest four of them occurring this year.
Also Read: 6 Simple Guides On PDPA Clause For Agreements Of Personal Data
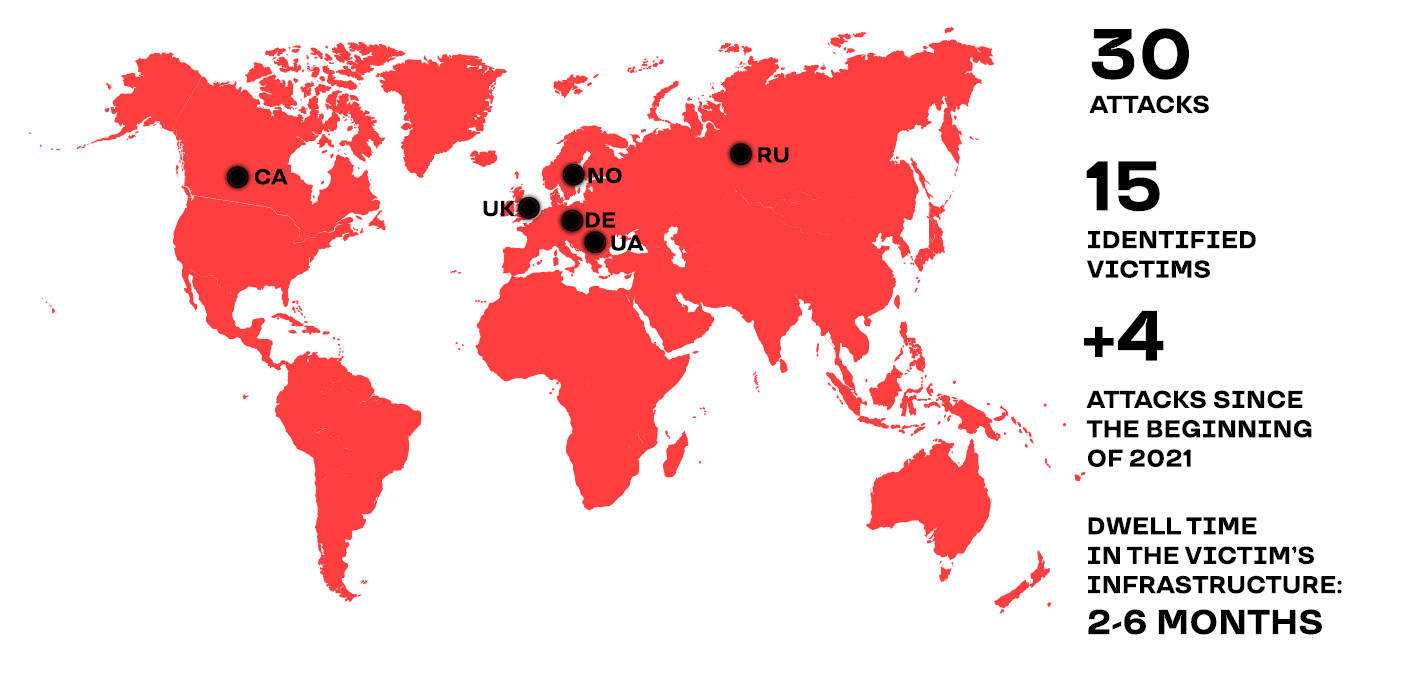
The hackers are proficient at staying undetected for long periods, between two and six months, before stealing corporate data (staff records, documents about legal entities, court records, internal files, email history).
Researchers at cybersecurity company Group-IB noticed a seven-month gap in RedCurl’s activity, which the hackers used to add significant improvements to their set of custom tools and attack methods.
Among the hacker’s latest victims is one of Russia’s largest wholesale companies, which supplies chain stores and other wholesalers with home, office, and leisure goods.
For reasons that remain unknown, RedCurl attacked this company twice, gaining initial access via emails impersonating the company’s human resources department announcing bonuses and the government services portal.
Also Read: The Top 10 Primary GDPR Requirements PDF To Secure Business
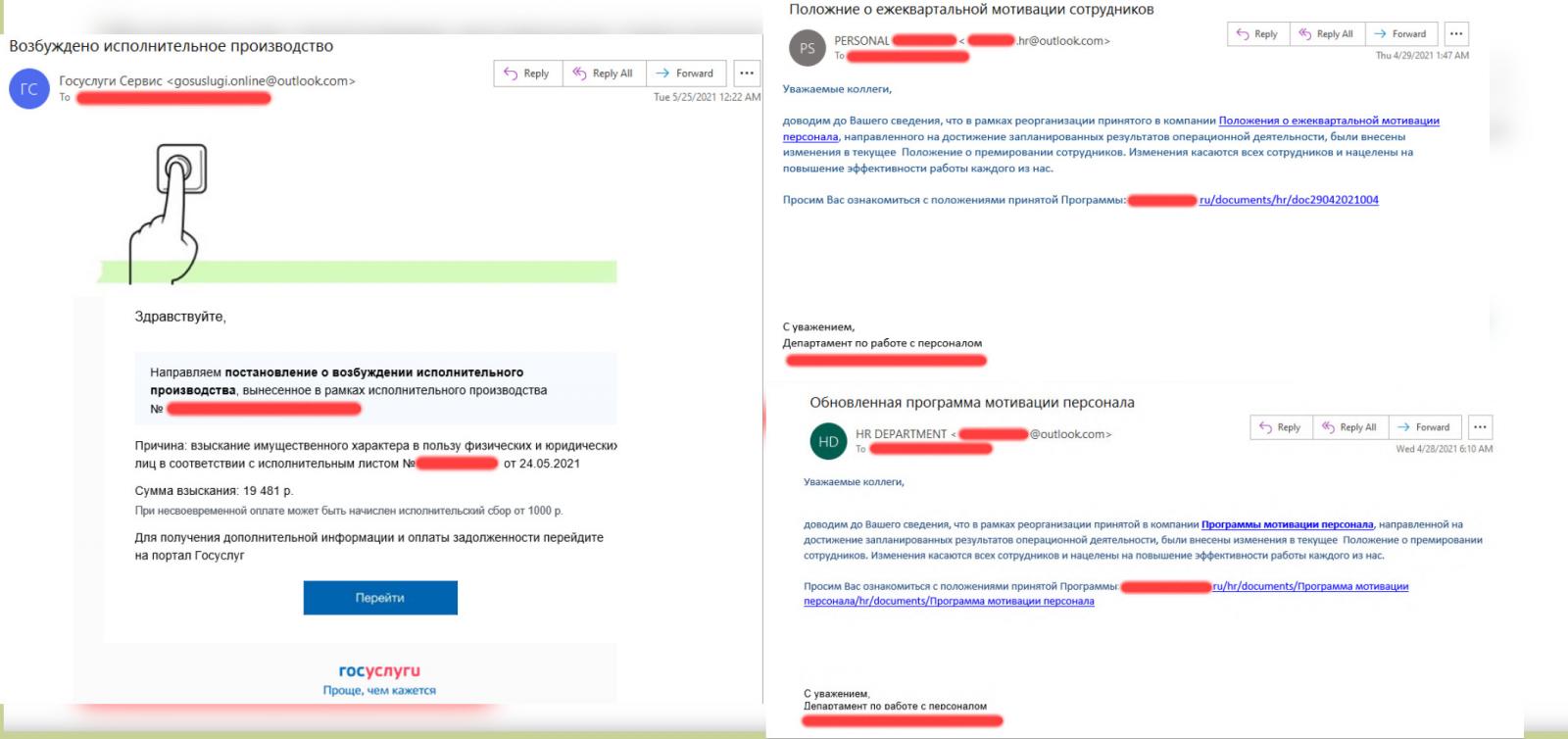
In both cases, the goal was to deploy on the employee’s computer a malware downloader (RedCurl.InitialDropper) hidden in an attached document that could launch the next stage of the attack.
During the investigation, Group-IB found that the RedCurl extended the attack chain to five stages, from the previously observed three or four steps.
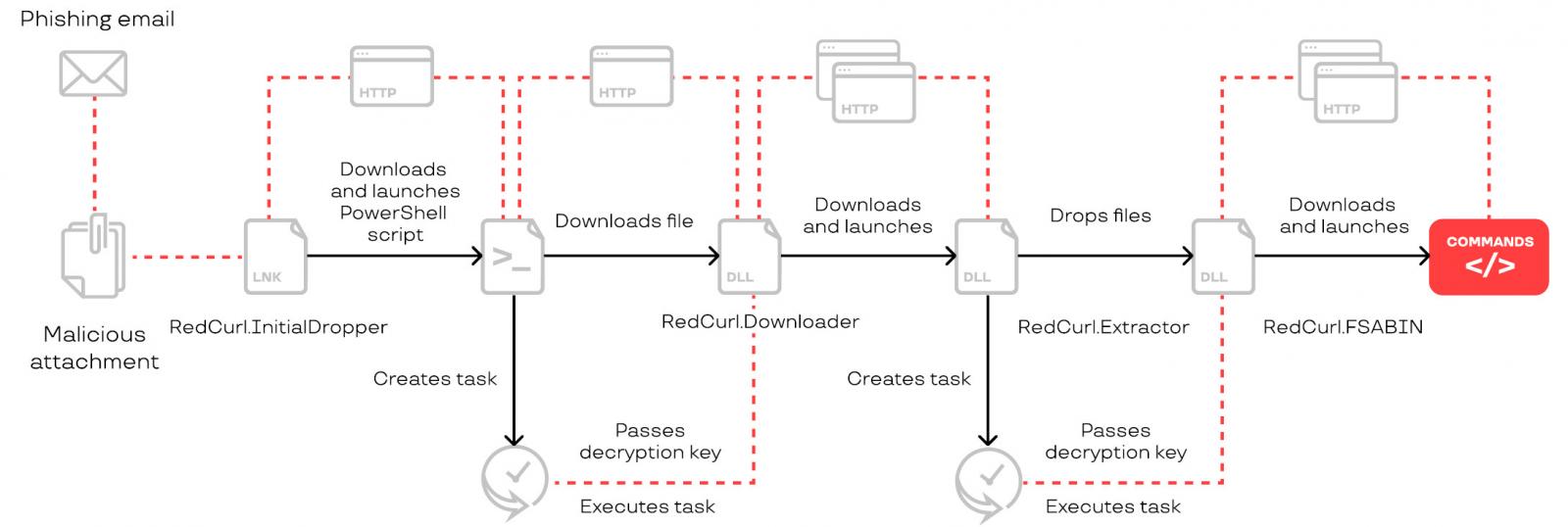
The hackers were careful not to raise any suspicion when the recipient opened the malicious document that launched the initial dropper, so they included a well-crafted decoy file with content related to the organization.
The dropper would fetch the RedCurl.Downloader tool, which collected info about the infected machine and delivered it to a command and control server (C2), and also initiated the next stage of the attack.
Group-IB discovered that the hackers now used RedCurl.Extractor, a modified version of the RedCurl.Dropper they found in previous attacks from this threat actor.
The purpose of this tool was only to prepare the final step of the attack, which involved achieving persistence on the system.
The researchers note that RedCurl has shifted from the typical use of batch and PowerShell scripts to executable files and that antivirus software failed to detect the initial infection or the attacker moving laterally on the victim network.
However, the improvements to RedCurl’s toolset appear to have been rushed, as Group-IB discovered a logical error in one of the commands. One explanation is that the group had little time to start the attack and could not properly test their tools.
Group-IB has published a report today with indicators of compromise and technical information on RedCurl’s updated set of tools and their functionality:
Despite not being as active as in other years, RedCurl maintains its sophistication and remains an advanced threat actor capable to stay undetected for months.
Group-IB says that of the four attacks identified this year, two were against the same target. However, they expect more victims to appear since RedCurl’s updated tools have been detected in the wild with increased frequency.