





US cybersecurity firm Rapid7 has disclosed that some source code repositories were accessed in a security incident linked to the supply-chain attack that recently impacted customers of the popular Codecov code coverage tool.
The computer and network security company has already notified a “small subset of customers” potentially impacted by this breach to take measures to mitigate any potential risks.
The unknown threat actors behind this incident were only able to gain access to a “small subset” of repositories containing source code for internal tooling used for Rapid7’s Managed Detection and Response (MDR) service.
“These repositories contained some internal credentials, which have all been rotated, and alert-related data for a subset of our MDR customers,” Rapid7 revealed.
“No other corporate systems or production environments were accessed, and no unauthorized changes to these repositories were made.”
The cybersecurity firm added that the Codecov tools compromised in last month’s supply-chain attack were not used to work with production code.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing
“Our use of Codecov’s Bash Uploader script was limited: it was set up on a single CI server used to test and build some internal tooling for our Managed Detection and Response (MDR) service,” Rapid7 said. “We were not using Codecov on any CI server used for product code.”
Codecov, the company behind a popular code coverage solution used by over 29,000 enterprises, disclosed on April 15th that unknown attackers maliciously altered its Bash Uploader script.
The compromised tool allowed the threat actors to harvest sensitive information (e.g., credentials, tokens, or API keys) from customers’ continuous integration (CI) environments and send it to attacker-controlled servers for more than two months.
A few days later, federal investigators reportedly discovered that the threat actors behind the Codecov hack automated the process of testing the stolen credentials, managing to breach the networks of hundreds of Codecov clients.
Two weeks after disclosing the breach discovered on April 1st, Codecov began notifying customers affected by the supply-chain attack, informing them that the unknown attackers might have downloaded their source code repositories.
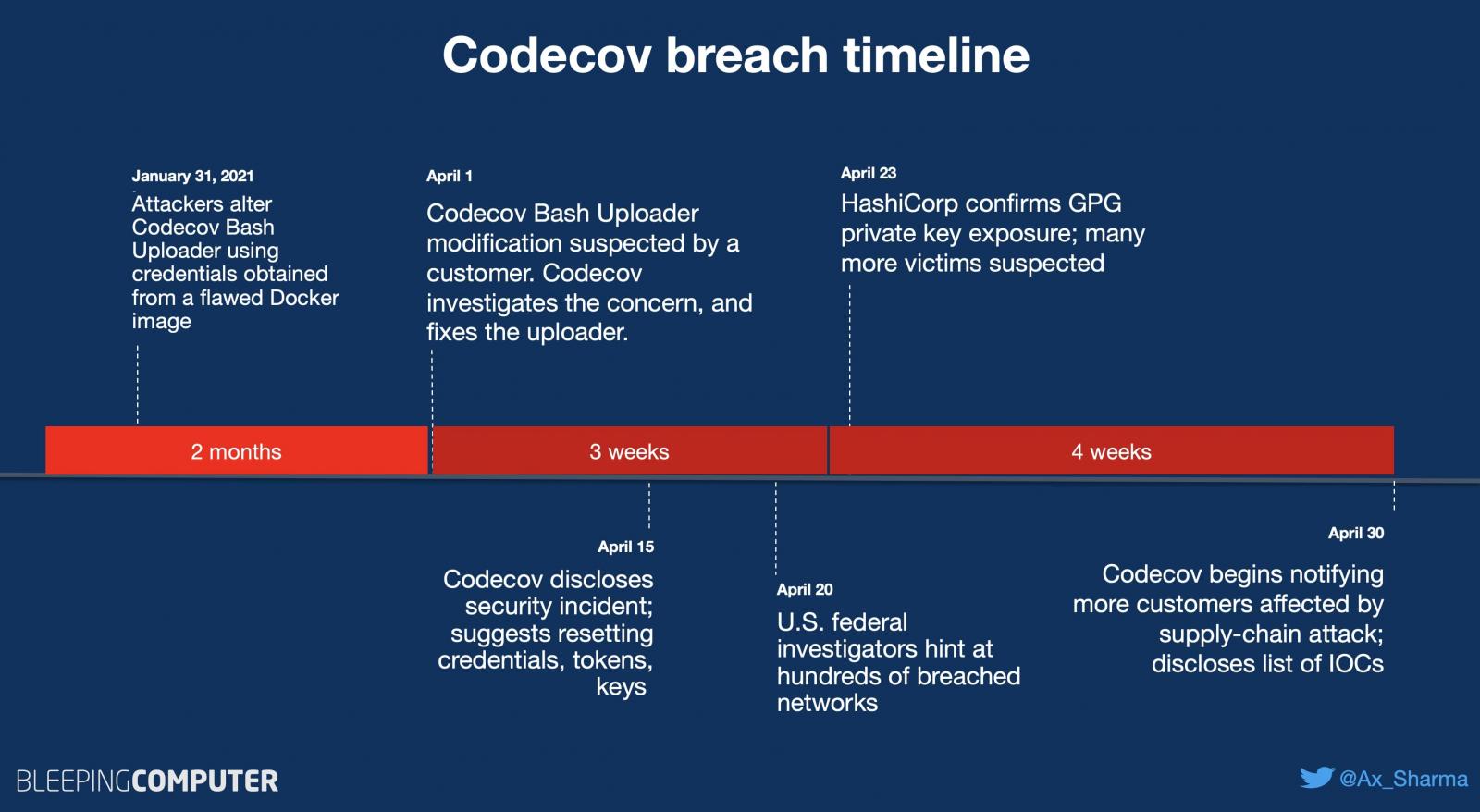
As first reported by BleepingComputer, Codecov customer and open-source software maker HashiCorp disclosed that the code-signing GPG private key used for signing and verifying software releases was exposed in the attack.
Cloud communications company Twilio also revealed that it was also impacted in the Codecov supply-chain attack, with critical systems not being affected.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
Codecov customers are advised to scan their networks and CI/CD environments for evidence of compromise and rotate all potentially exposed secrets.