





Researchers have spotted two campaigns linked to either the REvil ransomware gang or the SolarMarker backdoor that use SEO poisoning to serve payloads to targets.
SEO poisoning, also known as “search poisoning,” is an attack method that relies on optimizing websites using ‘black hat’ SEO techniques to rank higher in Google search results.
Due to their high ranking, victims who land on these sites believe they are legitimate, and actors enjoy a heavy influx of visitors who look for specific keywords.
Also Read: Battling Cyber Threats in 4 Simple Ways
According to the findings of the Menlo Security team, SEO poisoning by malware distributors is on the rise, with two notable examples being the Gootloader and SolarMarket campaigns.
The actors inject sites with keywords that cover over 2,000 unique search terms, including “sports mental toughness,” “industrial hygiene walk-through,” “five levels of professional development evaluation,” and more.
The optimized sites appear in search results as PDFs that, when visited, prompt a user to download the document, as shown below.

When they click on the download button, the users are redirected through a series of sites that ultimately drop a malicious payload.
The threat actors use these redirects to prevent their sites from being removed from the search results for hosting malicious content.
In these particular campaigns, the threat actors were either dropping REvil via Gootloader or the SolarMarker backdoor.
Also Read: What is Smishing? How Can We Prevent It? Explained.
In the two campaigns spotted by the researchers, the actors didn’t create their own malicious sites but instead hacked legitimate WordPress sites that already had a good Google search ranking.
The sites were hacked by abusing an undisclosed flaw in the ‘Formidable Forms’ WordPress plugin, which the hackers used to upload laced PDF into the ‘/wp-content/uploads/formidable/’ folder.
If you are using this particular plugin, upgrading to version 5.0.10 or later is advisable, even though 5.0.07 was the most recent version spotted in the compromised set.
The industry verticals for the types of sites compromised in this campaign are shown in the chart below.
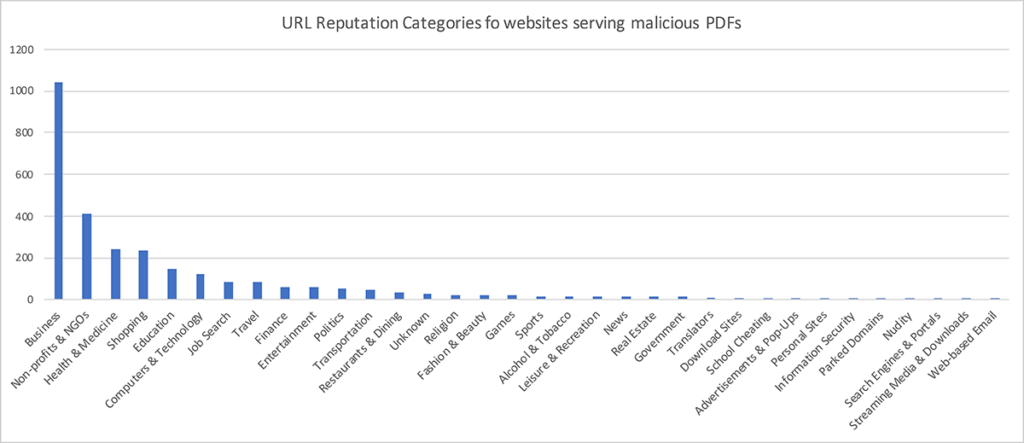
As you can see from the image above, the attackers heavily targeted sites in the business category, likely because they commonly host PDFs in the form of guides and reports.
When modern encrypting ransomware first launched in 2012, threat actors would spread a wide net in their attacks in the hopes of infecting as many people as possible.
As ransomware gangs are now targeting high value companies for multi-million dollar payouts, this spray and pray approach is not seen as often as you likely will infect consumers who would not be willing to pay large ransoms.
However, BleepingComputer knows of one REvil affiliate who performed wide-scale attacks to infect consumers and small businesses alike.
Instead of demanding hundreds, if not millions of dollars as ransoms, this affiliate would demand between $1,500 and $7,500.
While it is not known if this affiliate utilized SEO poisoning attacks, this type of attack would have fit their model of indiscriminately targeting any kind of victims.